WikiLeaks is probably exaggerating what’s in its latest CIA leak
WikiLeaks’ latest disclosure of secret CIA hacking capabilities, published March 31 as part of a package of documents dubbed “Marble,” describes how the spy agency obfuscates certain digital espionage techniques. The transparency organization is overselling what’s actually in the leaked computer code, experts say.
The documents show that some hacking tools used by the CIA may have been constructed with code that contains foreign languages. It’s not uncommon nor out of scope for an intelligence service to design malware that can avoid detection, or to trick a target into believing a file is legitimate, according to Rendition InfoSec founder Jake Williams, including the use of a foreign language trait.
“The news here is that the [CIA] does string obfuscation to keep their malware hidden from detection,” Williams said, “meaning they aren’t wasting your tax dollars.”
The transparency organization led by Julian Assange has described the Marble library as “the digital equivalent of a specialized CIA tool to place covers over the English language text on U.S. produced weapons systems before giving them to insurgents.” Cybersecurity experts and former intelligence officials say, however, that the release showcases an unsurprising practice that is already used by a bevy of different attackers, including the Russian FSB and Chinese military.
The disclosures may specifically hamper the CIA’s ability to camouflage current intelligence gathering efforts and blow the cover on older operations now that the spy agency’s own obfuscation library is out in the open.
“If this is in widespread use in CIA tools it could lead to the discovery of them that were previously misattributed,” said Williams, “for forensic teams, I think there’s some work to do to write signatures for the obfuscation library.”
WikiLeaks’ claims about the March 31 disclosure suggested that the obfuscation techniques were more than just run-of-the-mill spycraft.
“[Marble] would permit a forensic attribution double game, for example by pretending that the spoken language of the malware creator was not American English, but Chinese, but then showing attempts to conceal the use of Chinese, drawing forensic investigators even more strongly to the wrong conclusion,” a WikiLeaks press release reads.
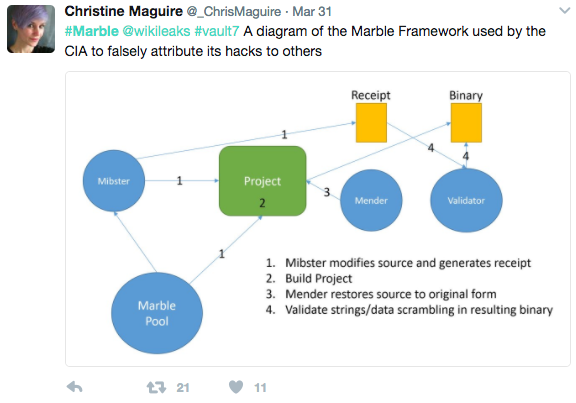
Tweet from a journalist working for RT, a media outlet linked to the Russian government by the U.S. intelligence community.
After publishing the documents on Friday, WikiLeaks also claimed in a tweet that Marble would allow researchers to attribute “thousands of CIA viruses and hacking attacks.”
On social media, the material took on a life of its own, sparking accusations that Marble proved the CIA had engaged in “false flag” operations, including disguising itself as Russia to hack into the Democratic National Committee. The term “false flag” is used to define a covert action that is purposefully designed in such a way that it appears to come from another entity, group or country.
But the actual data provided in Marble does not backup many of the claims now being spread on social media, experts told CyberScoop.
“I doubt this would be the tool they’d use [to false flag],” said security researcher Jonathan Nichols, “a close inspection of a sufficient sample size of code obfuscated this way would reveal that it’s programmatic. This makes it a bad choice for black-ops.”
The techniques can be reversed, Nichols said, which suggests there is a pattern to how the obfuscation is applied.
“I wouldn’t risk my black-ops on such a chance,” he said. “If I were playing the high-stakes game of false flags, It’d be much safer to simply hire foreign language coders than to use this technique.”
The foreign language strings found in Marble show an apparent and noticeable lack of language proficiency by the developers — good enough to potentially trick an automated program, like an antivirus system, but nowhere close to the quality necessary to appear authentic on closer inspection.
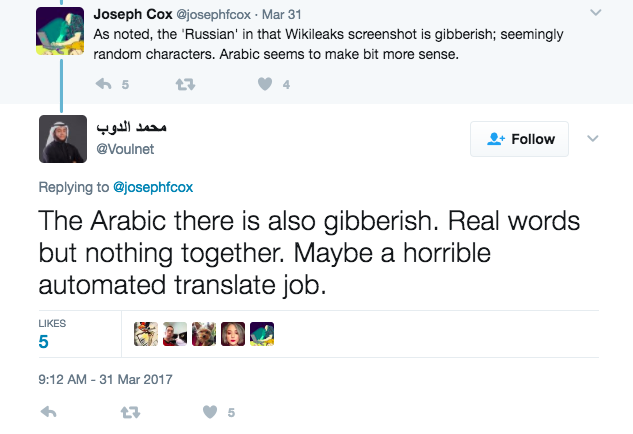
Journalist and security researchers on Twitter realize that foreign language application in Marble largely produces “gibberish”
“Even a cursory examination of the foreign language in the code shows that it is not used for false flag operations,” Williams told CyberScoop.