Leaked CIA documents show just how complicated computer warfare really is

Providing context to the CIA documents published last week by WikiLeaks has proven challenging because of the prevalence of codenames, unfamiliar acronyms and other unique jargon in the material. But with the help of a former U.S. intelligence official, CyberScoop has been able to identify an internal conversation evident in the leaked documents that shows employees of the spy agency discussing how to remotely disrupt a video player likely being used by a terrorist.
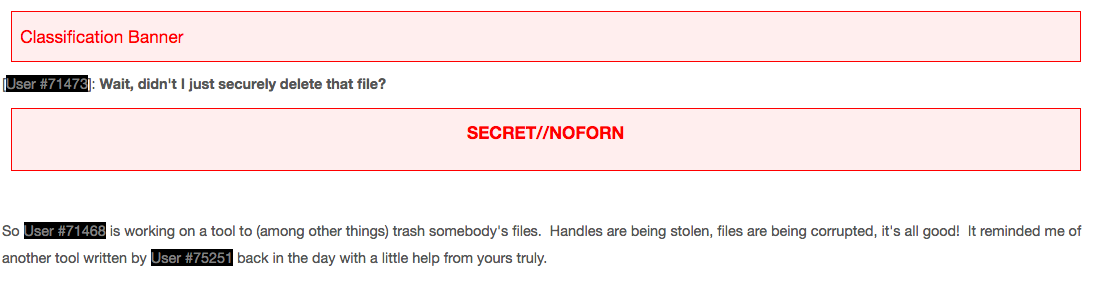
An author identified only as “User #71468” in one apparent internal CIA discussion forum published by WikiLeaks describes the use of an old hacking tool to “trash somebody’s files.” The author’s post is classified “SECRET//NOFORN,” meaning secret and not for review by foreign nationals.
Screenshot of CIA doc published by WikiLeaks
User #71468’s comment reads:
“We were trashing data. It was awesome. We were even overwriting files opened for exclusive write by using direct writes to the physical drive (XP only folks, Vista and up broke the ability to do that.) We were targeting multimedia files, and the requirements said ‘thou shalt interrupt playback.’ We figured trashing the files at such a low level would obviously stop the playback, right? No bytes, no playback? Turns out, we were wrong. The system’s filesystem read cache was happily keeping the entire file in memory and the media player was happily playing it from the cache as if nobody had come in and barfed garbage bytes all over the clusters. Frustration ensued. Rage++… but what were we to do? The answer came from a single StackOverflow post that mentioned a side-effect of opening a volume handle in a peculiar way.”
Following this commentary is a text box containing code evidently used to interrupt Microsoft XP’s default video player. Though WikiLeaks redacted a significant portion of sensitive, potentially executable computer code in the document dump, CyberScoop previously found cases in which the editors failed to properly censor highly sensitive material.
“The document describes a computer network warfare operation, commonly known as a Computer Network Attack (CNA), probably part of the CIA’s covert action program against terrorists proliferating jihadi material,” a former U.S. intelligence official, who spoke on the condition of anonymity to discuss a classified operation, told CyberScoop. “The attacker is under direction to stop playback of a video. However, the attacker struggles to stop the media file from playing due to the Windows Operating System pre-caching its contents to memory. Looking for a solution, the attacker turns to StackOverflow,” a website where programmers crowdsource answers to technical questions.
Such an operation would have been likely conducted, the former official said, under legal authority derived from the Authorization for Use of Military Force, or AUMF, which was signed immediately following the 9/11 attacks.
The leaked CIA document showcases, among other things, the irrefutable complexities associated with modern computer network warfare.
“Even a simple operation to stop someone from playing a video is incredibly complex. More broadly, software variants introduce more complexity. Each patch, update, and operating system need to be individually tested and evaluated to determine if a specific technique will work to cause an intended effect. This challenge is costly in resources as it takes significant time to test each variant,” the former intelligence official said.
Documents taken by former contractor Edward Snowden showed that technology development teams in agencies like the NSA and CIA are commonly tasked with engineering highly specialized tools — with each capability individually designed to target a certain version of software.
The specificity required to develop effective hacking capabilities, however, also underlines the simple fact that computer warfare techniques often have a very short shelf life, the former official explained.
“In this case, an effect that works on Windows XP is known to now work on any newer versions of Windows. To cause a similar effect on a newer version of Windows, probably involves even more complex techniques such as overwriting the memory segments containing a playing video.”