Alphabet’s Chronicle banks on big data with new threat analysis platform
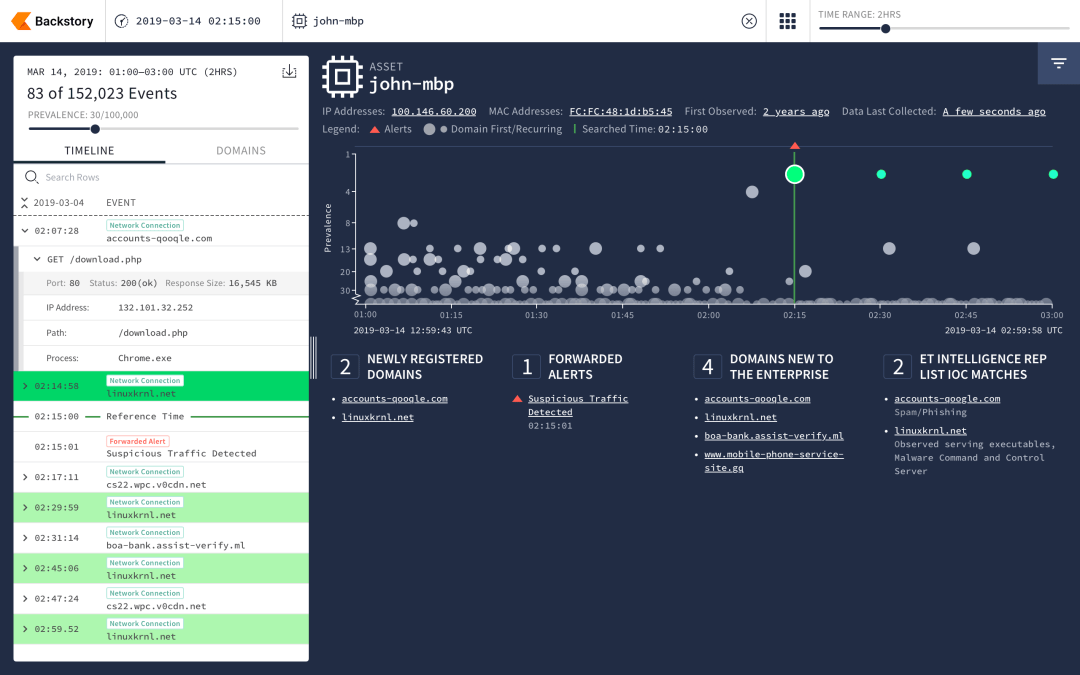
Chronicle, the cybersecurity firm stood up last year by Google parent company Alphabet, entered the threat analysis business Monday when it announced a cloud-based platform that compares reams of network data with malicious cyber activity.
In doing so, Chronicle is betting that Google’s access to immense amounts of stored data will help security professionals make better sense of information in what is already a crowded threat-intelligence market.
The tool, called Backstory, allows companies to upload their internal security data and then analyze it, offering a repository stretching back years. It constantly compares that historical corporate ledger with new threat data to inform companies of any “historical access” to malicious domains or files, according to Chronicle. Hackers can linger on organizations’ networks for months, if not longer, and Backstory aims to use Google’s search capabilities to find breaches that slipped through the cracks.
“Backstory was designed for a world where companies generate massive amounts of security telemetry and struggle to hire enough trained analysts to make sense of it,” Chronicle said in a blog post.
The company’s engineers built a network layer over Google’s infrastructure to allow companies to upload large caches of data; things like DNS traffic and proxy logs. That information is kept private and isn’t scannable by other parties, the company said.
The project was born in the aftermath of a breach of Google by suspected Chinese hackers in 2009. After that incident, Google’s Threat Analysis Group developed security tools that Chronicle says laid the groundwork for the Backstory platform.
“Massive telemetry that enterprises either could not afford to log or simply didn’t, we actually turned into extremely valuable signals,” Mike Wiacek, Chronicle chief security officer and co-founder, declared at a press event Monday at the RSA Conference in San Francisco. The more data fed into the Backstory’s cloud, the more detailed a picture it paints, he said.
Chronicle representatives did not disclose details on how much it costs a company to use Backstory, only saying that pricing depends on the number of employees at an organization.
Chronicle executives say the platform allows analysts to dive deeper into malicious indicators by building on the company’s popular VirusTotal search engine. As an example, they pointed to the hacking documented in an indictment of 12 Russian military officers unsealed by the Justice Department in July 2018.
The indictment mentions a malicious domain used by the hackers to communicate with the Linux-based malware. With that domain called out by U.S. authorities as potentially infectious, security officers at companies around the world would want to know if devices on their networks had communicated with the domain. VirusTotal would return much of the information on that domain, but the idea behind Backstory is to give a fuller picture of a company’s network to see if there were any compromises.





