WikiLeaks left key details unredacted in CIA leak
Though editors working on behalf of WikiLeaks removed a vast majority of the technical details previously attached to CIA documents the group published on Tuesday, it appears that sensitive information was available to anyone who accessed the files, according to a confidential analysis obtained by CyberScoop.
“The censoring appears to have been done by a highly knowledgeable team or individual, indicating deep knowledge into cyber espionage, opsec, ITSec and creating indicator of compromise,” Kaspersky Lab researchers wrote in a report released Wednesday. “Nevertheless some pieces of data allowed us to identify different artifacts … the editors made several mistakes by leaving behind several uncensored details.”
Artifact is a term used among information security professionals to describe digital forensic evidence, which in some instances may be helpful to better understand how a breach occurred and who was responsible.
Some of the artifacts found in the leaked CIA documents have given researchers insight into unique malware and a command-and-control server that was likely used to deploy implants onto Cisco routers.
In a few cases, different license keys stored in the “Vault 7” archive also provided personal information for individuals and businesses that were apparently involved in supplying hacking tools and other IT services to the agency. While an employee or contractor’s name was plainly spelled out in some documents, other instances required some effort and other artifacts to uncover identities.
“Names, email addresses and external IP addresses have been redacted in the released pages (70,875 redactions in total) until further analysis is complete,” a WikiLeaks press release reads. “These redactions include ten [sic] of thousands of CIA targets and attack machines throughout Latin America, Europe and the United States.”

Via WikiLeaks press release
This is not the first time that WikiLeaks has been criticized for sharing poorly redacted material.
After a coup attempt in Turkey last year, WikiLeaks published what it promised were thousands of internal emails belonging to the country’s ruling Justice and Development Party, or AKP. The massive trove of emails contained some private personal information of citizens that were completely uninvolved in government, according to Turkish sociologist Zeynep Tufekci.
Partners, suppliers and authors
Licenses for 010 Editor — a program that allows for edits of raw binary code — that had been acquired by the CIA based on the leaked documents are under the name of an employee of D.C.-based SC3, an information technology and services firm.

(Screenshot from Kaspersky report obtained by CyberScoop)
Another PDF file holds screenshots of an internal content management system used by the CIA, where the name of the last user to modify the page is clearly shown. Security researcher Nicholas Weaver noted the redaction mistake on Twitter.
https://twitter.com/ncweaver/status/839162128636391424
Other licenses for Sublime text editor can be seen registered to Affinity Computer Technology, which through a Google search shows a computer repair and installation store based in Sterling, Virginia.
An Apple iOS 8 vulnerability codenamed Ironic, which was mentioned in a leaked document describing CIA hacking capabilities, points to the name of the researcher who originally discovered the software flaw, Stefan Esser. WikiLeaks did not redact Esser’s name in any way.
Servers and tools
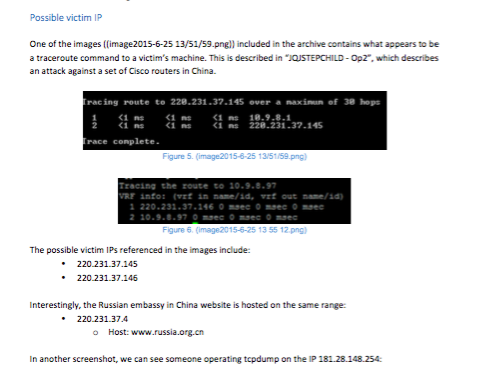
One image published in WikiLeaks’ archive contains what looks like trace route commands to Cisco routers in China. Interestingly, several of the possible victim IPs referenced in the image are hosted on the same range as the website for Russia’s embassy in China.
Confidential analysis report obtained by CyberScoop
A command and control server used to validate some attacks was identified by researchers and traced back to vesselwatcher[.]net, a now defunct domain. It’s believed that several other attack servers were registered by the same actor linked to this “vesselwatcher” domain, based on a confidential Kaspersky Lab report.
Confidential analysis report obtained by CyberScoop
Researchers were also able to partially reconstruct two malware tools, codenamed Zabbix and JQJSNICKER — a feat that WikiLeaks hoped to stop from happening.
Zabbix appears to be a utility for managing services while JQJSNICKER is a backdoor .NET payload that uses PowerShell.
UPDATE, 3/21: CyberScoop has learned that the Zabbix malware referenced above shares a name with a popular open source application monitoring software program. Below we have shared a screenshot from the report where Kaspersky labels the malware based on the data it uncovered.
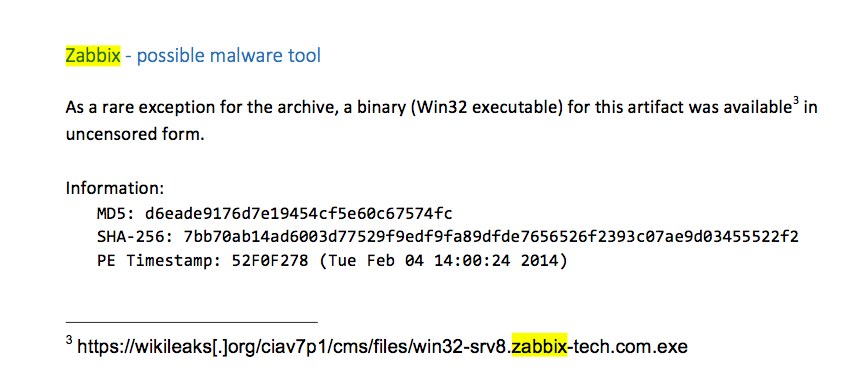
(Screenshot from Kaspersky obtained by CyberScoop)