Banking-focused phishing scheme hits inboxes in wake of Equifax breach

A group of hackers has been sending specially tailored phishing emails to online banking customers, stoking fears among an online population that is increasingly concerned with how cybercriminals could leverage the data stolen from credit monitoring giant Equifax.
This specific phishing campaign, identified by U.S. technology firm Barracuda Networks, focuses on a string of recent banking-related emails that began to hit inboxes shortly after Equifax was originally breached, but several weeks before the incident was first publicly disclosed Sept. 7.
The campaign remains active.
Although the scheme’s timing has caught researchers’ attention, it remains unclear whether the criminal operation was directly related to the Equifax breach.
Security experts have warned that the Equifax breach could lead to fraudulent credit card charges for affected individuals. As a result, it’s no surprise that hackers are actively attempting to impersonate legitimate banking companies as they communicate with clients about suspicious account activity.
Barracuda Networks provided CyberScoop with several screenshots of the aforementioned phishing emails. The banks mentioned in these emails include Bank of America, TD Bank and the Canadian Imperial Bank of Commerce.
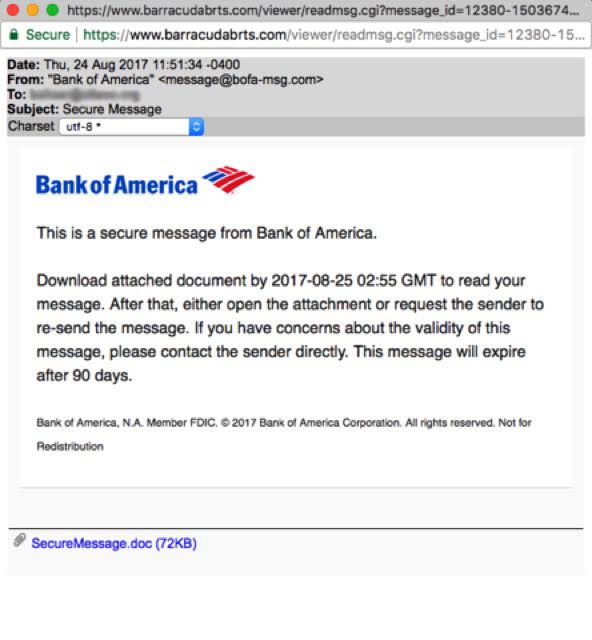
Phishing example A / Barracuda Networks
The phishing emails identified by Barracuda appear to have all been sent by the same actor and they seem to be fairly targeted.
The number of emails sent is low in comparison to most phishing operations, which send millions of emails with little effort in order to trick as many people as possible, according to Shi.
“These attacks occurred a few days apart and were not as high in frequency as the Locky ransomware attack we saw,” Shi said, referring to the recent resurgence of malware first seen several years ago. “These attacks seem to take the attacker longer to harvest data. Information gathering and testing against the victims’ data maybe the reason why the volume is not very high, and why the attacks are spaced out. Also, these attacks do not seem to utilize botnets for delivery. ”
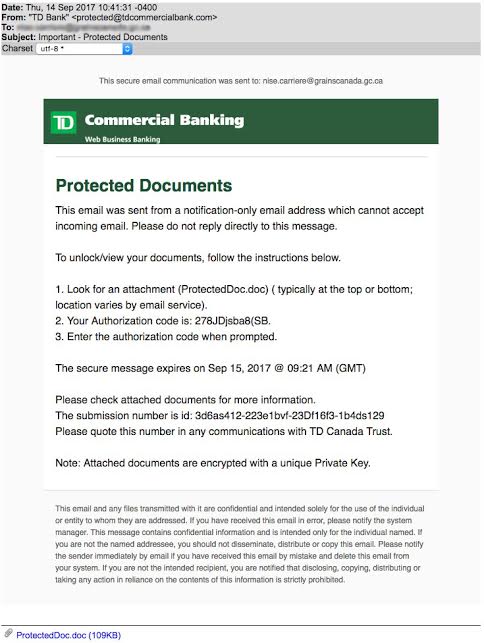
Phishing example B / Barracuda Networks
A leaked internal Equifax incident response report following the breach, obtained by the Wall Street Journal and authored by contractors Mandiant, noted that the attackers were likely criminal in nature and unrelated to a known advanced persistent threat, or APT. Most APTs are associated with foreign governments.






