Shadow Brokers’ latest leak could have come from beyond NSA staging servers

A mysterious group that claims to have stolen tools once used by the NSA published material Sunday to show it is in possession of Microsoft Windows software exploits.
Screenshots of the alleged exploits in use, along with a comprehensive list of filenames and directories were all shared by the enigmatic group the “Shadow Brokers,” in a new blog post. Beyond the supplementary evidence is a set of encrypted folders, each protected by a PGP key. The encrypted folders presumably hold the actual, functioning exploits Rendition Infosec founder Jake Williams told CyberScoop.
A meticulous inspection of the aforementioned filenames and directories provides some clues about where the hacking tools came from and when they were developed.
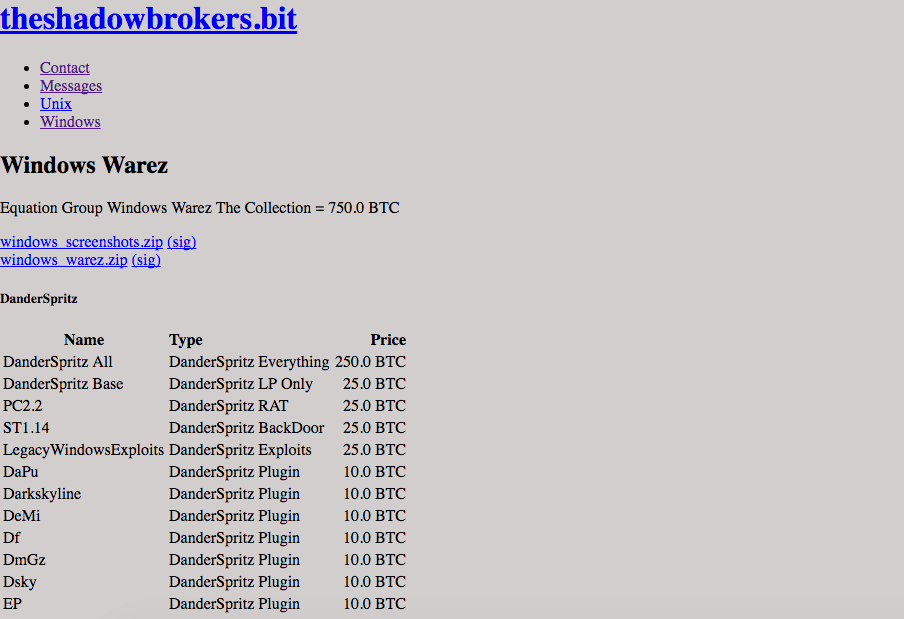
ShadowBrokers leak page/website
Cybersecurity experts tell CyberScoop the viewable evidence suggests the existence of advanced hacking tools, which could be used to exfiltrate data, destroy digital forensic evidence, attribute old cyberattacks and compromise numerous systems running older versions of Windows. The Shadow Brokers are supposedly selling the exploits for roughly $650,000 worth of bitcoin in total.
“These filenames and directories look familiar to me … Based on their [Shadow Brokers] past behavior, other things they’ve posted, I have no reason to be believe they don’t have them,” a former U.S. intelligence official told CyberScoop on the condition of anonymity.
Microsoft security teams are aware of the leaked exploits and have begun investigating the incident.
“[But] there’s not much for Microsoft to do until the files themselves are made public,” said Williams, a former vulnerability analyst with the Defense Department.
“Microsoft has telemetry where they get crash reports that include data about what caused a crash. Given that the Shadow Brokers’ are indicating they have zero days for IIS [Internet Information Services for Windows Servers], RDP [Microsoft Remote Desktop] and SMB [Microsoft Server Message Block], teams are likely taking a hard look at crash reports for those services,” Williams said.
Among the trove of published file names and directories is reference to “DANDERSPRITZ,” a software tool used by attackers to obfuscate IP and MAC addresses. Documents previously revealed by former NSA contractor Edward Snowden show that DANDERSPRITZ was used by operators at the spy agency.
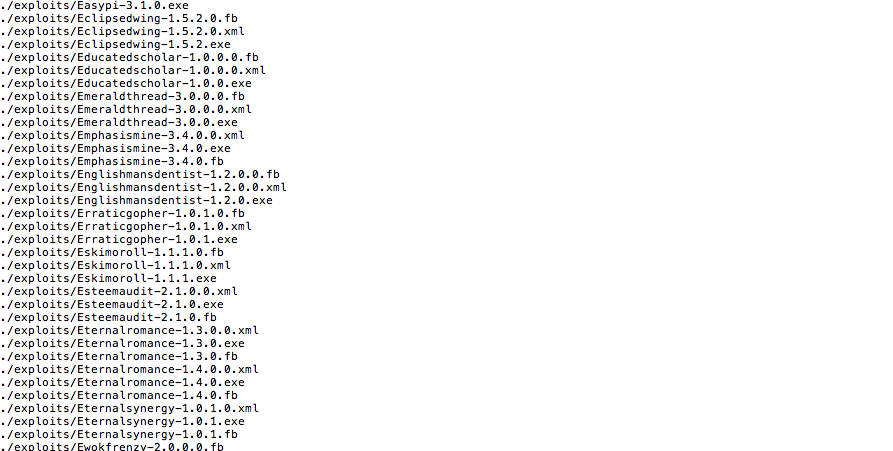
Leaked filenames and directories for Windows exploits
Leaked documents describing another plugin, named “EventLogEdit,” show it could be used to edit event logs, giving the attacker the ability to manipulate digital forensic evidence that would normally show anomalies after an intrusion, said Williams.
“EventLogEdit” was likely developed and deployed by a well resourced and technically gifted adversary, like an intelligence service, described Michael Zeberlein, director of intelligence analysis with Area 1 Security.
“You can think of most of these exploits as basically offensive, intelligence gathering forensic tools; as [system administrator] internals that would help an operator get into the guts of a Windows system,” Zeberlein explained.
The use of specific, outdated terminology overlaying specific files, for example, and the presence of older versions of JavaScript implies that many of the referenced exploits were created prior to 2008, said Zeberlein.
Additionally, the listed files appear to have come from a source repository, he said, meaning the leak came from inside a closed environment, rather than on a staging attack server that once existed on the open internet.
“An external source would not have all the eggs in the same basket,” said Zeberlein, “none of the data is obfuscated to look non-malicious via encryption, packing, compression, or renamed to look like something benign to fool a victim … the organization of the folder structure is also similar to a source repository and there are clear development files in there such as optimized and compiled Python files that are not .EXE files.”
If a spy were to rely on these tools for an intelligence gathering operation then it should have been heavily audited to confuse the targets, Zeberlein told CyberScoop. The files, detailing what each exploit does, are laden with the “fingerprints” of its operators.
The new findings are significant because it counters a once prominent theory that the Shadow Brokers had stolen their material solely from poorly configured NSA staging servers.
The ShadowBrokers first emerged on social media in August after dumping a trove of sophisticated, albeit also outdated, firewall exploits on Github. At the time, security experts told CyberScoop that these firewall exploits — a cohort of hacking tools designed to target vulnerabilities in Cisco, Fortinet and Juniper Networks products — were authentic and capable of penetrating systems. Because the source code for these firewall exploits was provided in a public forum, random hackers began using the tools themselves.
Sunday’s message from the Shadow Brokers differs from their original firewall exploit dump in August as it includes evidence of the tools without ever posting the operational code.
“The U.S. has significantly assisted the CNE [computer network exploitation] capabilities of our adversaries [by allowing] this leak of code,” said Zeberlein, “we respond with a pin-prick Persona non grata response to kick out Russian diplomats, whereas this action just Persona non grata’ed our entire SIGINT [signals intelligence] capability for cyber.”
“I think that the timing is likely retaliation for the ODNI report and a demonstration that they can hurt us more than we can hurt them,” Williams said, “it takes more than just listing tools to create good cyber attribution.”






