Mysterious malware campaign targets just 13 iPhones in India
An application-warping malware campaign in India is aimed at just 13 iPhones in what researchers are calling a “highly targeted” operation.
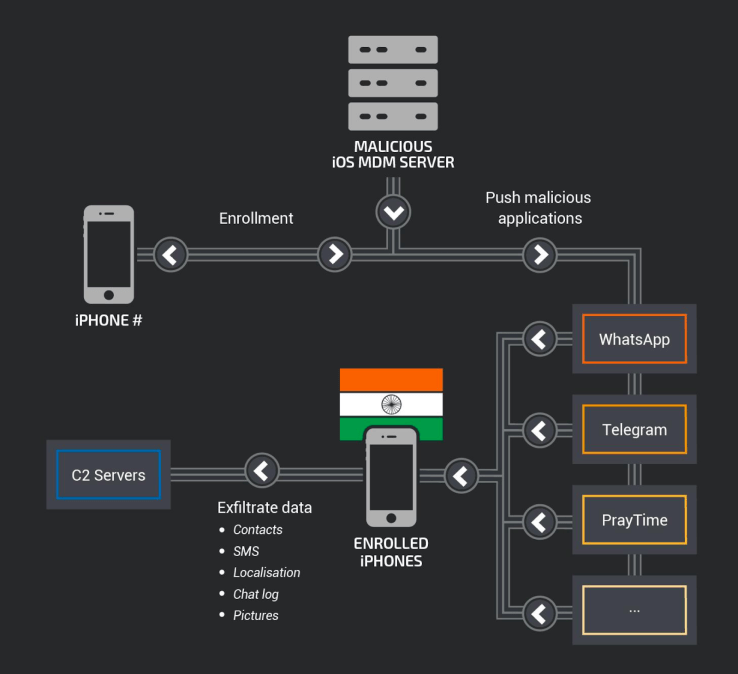
The attackers are using an open-source mobile device management (MDM) server to distribute the malware through popular apps like Telegram and WhatsApp, researchers from Talos, Cisco’s threat intelligence unit, revealed Thursday. The use of MDM, a popular enterprise tool for administering mobile apps, allows hackers to control how their malware is interacting with the target phones.
“This campaign is of note since the malware goes to great lengths to replace specific mobile apps for data interception,” researchers Warren Mercer, Paul Rascagneres, and Andrew Williams wrote in a blog post.
The researchers don’t know who was targeted in the campaign, who carried out the attack, or why. While the hackers apparently tried to plant a “false flag” by posing as Russian, evidence suggests they were operating in India, according to Talos.
The malicious code injected into the apps can collect and exfiltrate phone and serial numbers, location, contacts, and Telegram and WhatsApp messages. The iPhone users are likely lured into enrolling in the MDM service through a social engineering campaign, according to the researchers. Each step of the enrollment process requires interacting with the user, such as installing a certificate authority on the iPhone.
Apple has revoked 5 certificates linked with the campaign, according to the researchers.
“The likely use of social engineering to recruit devices serves as a reminder that users need to be wary of clicking on unsolicited links and verify identities and legitimacy of requests to access devices,” they wrote.
The growing use of MDM at large organizations means users need to understand that installing additional certificates on devices can expose them to malicious activity, the researchers advised. “By installing a certificate outside of the Apple iOS trusted certificate chain, you may open up to possible third-party attacks like this,” they added.
It’s an open question as to why the malware, which the researchers say has been in use since August 2015, has gone after just 13 iPhones. Asked about this, a Talos spokesperson said that, for now, the researchers won’t be offering additional information beyond the blog post.
“Over a three-year period, the attackers remained under the radar — likely due to the low number of compromised devices,” the blog post states.