Islamic State supporters hit by Android malware on Telegram

Islamic State supporters are warning one another of malware targeting the militant group through the chat app Telegram.
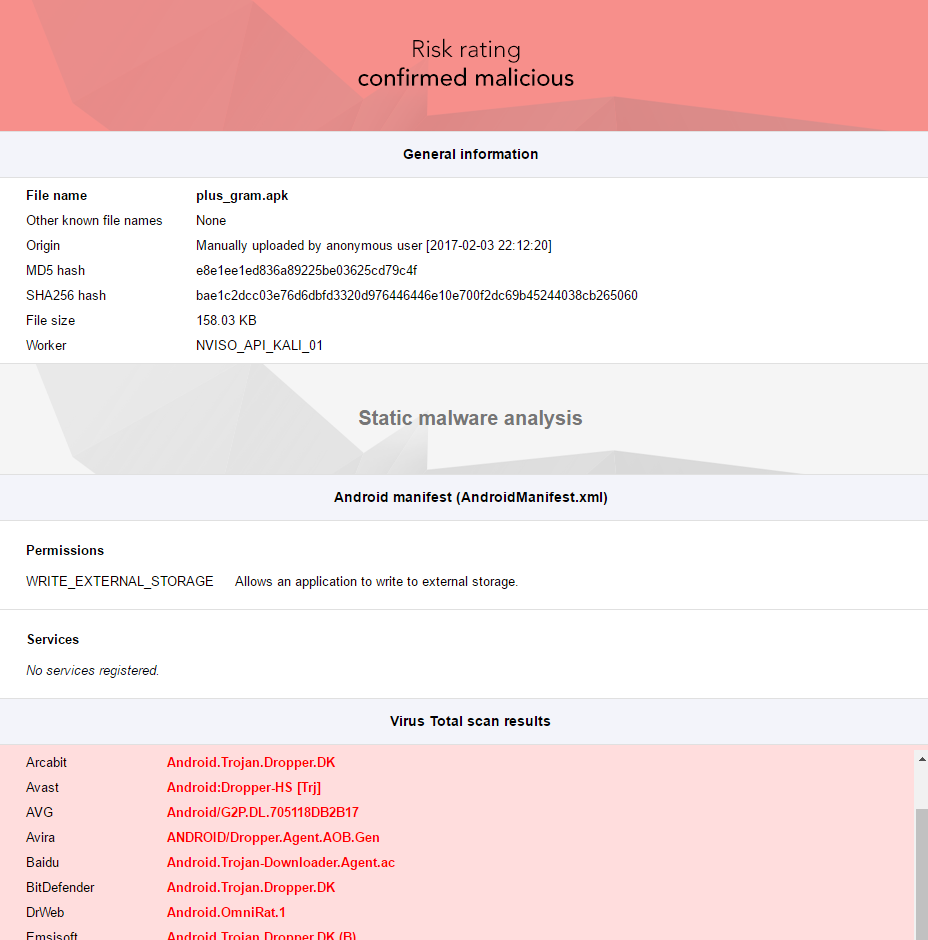
One member on a popular ISIS forum alerted users to plus_gram.apk, a trojanized RAT (a remote access tool disguised as harmless software) that allows an attacker to spy on and take full control of the target’s Android device. The ISIS supporter used malware analysis at NVISIO, a popular free platform to test Android software for malicious code.
The warning was first spotted and described by @switch_d, a veteran ISIS watcher.
This attack arrives as a phishing link disguised as an invitation to a video chat, according to the warning, a tactic ISIS supporters have fallen victim to in the past. The responses to the warning include a thanks and common sense guidance to “only accept files from brothers you know.”
This malware runs in multiple stages, Khalil Sehnaoui, a Middle East-based cybersecurity specialist and founder of Krypton Security, told CyberScoop. “The exploit code is usually small and after successful exploitation it runs a dropper code which will in turn download new applications/malware in order to get more control of the system by escalating privileges.”
Sehnaoui hadn’t obtained a copy of the malware, but was instead looking at the NVISO analysis.
“Now the code the dropper loads is usually more complex and depends on the attacker’s objective (trojan, ransomware, scareware, etc),” Sehnaoui explained. “The location the dropper goes to in order to retrieve the code usually changes quickly as it’s a race against authorities and/or security companies tracking the attacker’s steps. The dropper is loaded with the exploit code; The second stage could, like I mentioned previously, be any other application depending on the attacker’s goals.”
Widely popular across the Muslim world, Telegram has been one of the the Islamic State’s favorite communications apps for at least three years. It boasts both far-reaching public channels, akin to Twitter feeds, as well as encrypted private messaging. The security behind the software has been sharply criticized by many prominent technologists, but it remains exceedingly popular with over 100 million monthly users — and it’s an obvious vector of attack for adversaries looking to hack Islamic State supporters.
Recruiters and plotters working for the Islamic State use Telegram and other apps to communicate and coordinate with newcomers. A recent New York Times analysis outlined several terror plots in which Telegram was the chief planning app. It also serves as an effective propaganda vector that can reach millions with a single post.
The internet is a uniquely utilized weapon for Islamic State supporters that allows them to wage propaganda, disinformation and recruiting campaigns at an unprecedented level. Due to the terrorist groups Internet use, cyberattacks regularly target ISIS online. Last year, McAfee uncovered a Trojan spread via Twitter (another ISIS favorite) disguised as Al Rayan Radio, which promises propaganda but delivers surveillance.
The United States has ramped up cyberwar operations against ISIS in recent years. Details of operations are rare as much of it is classified. The offensive, centered at U.S. Cyber Command, came after long bouts of criticism from the public as well as former Defense Secretary Ash Carter who grew frustrated with the lack of effective weapons against ISIS’s online presence. Late last year, all 133 of U.S. Cyber Command’s Cyber Mission Force teams achieved initial operating capacity to “execute their fundamental mission.” The force is set to grow to 6,200 individuals across 133 teams by the end of 2018 when they are meant to achieve “full operational capability.”
There is no definitive information on the source and targeting of this particular malware, only that it’s hitting Islamic State users and they are issuing security warnings as a result.
Cyberwar is no stranger to the Middle East’s cacophony of conflicts. Hackers on every side of the Syrian civil war have exchanged blows for the last half-decade. Before Telegram became popular, software like Skype was used widely by militants and was the attack vector of choice to spread RAT attacks against anti-Bashar al-Assad fighters.
“Google runs a malware analysis software, and a good one at that, on all apps coming from its store,” Sehnaoui said. “So it is not surprising that people would try to spread infected applications through other means, namely chat applications like Telegram. It’s a social engineering game at this point. For example: ‘Hey download this new app as it is more secure than [your current chat application here] and it does not go through Google so the Government can’t spy on us.'”
Both Telegram and Twitter have engaged in numerous waves of mass shuttering of ISIS-related accounts in the past half decade. The efforts have failed to completely stopped the militant group’s use of either platform.





