Data about 57 million people exposed by Elasticsearch servers
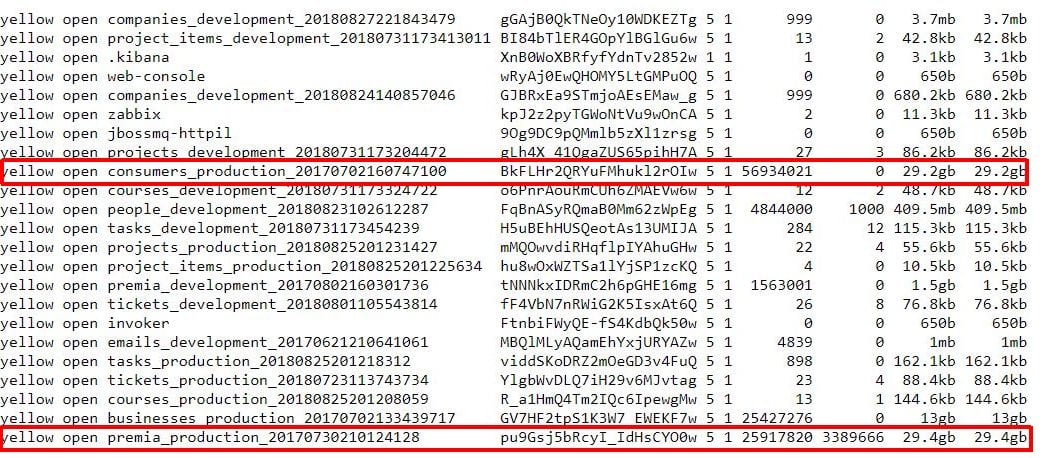
A data breach involving Elasticsearch search-engine technology exposed the personal information of nearly 57 million people for at least two weeks, according to report released Wednesday by the cybersecurity organization Hacken.
The breach exposed 73 gigabytes of data as early as Nov. 14, Hacken said, including the names, employers, job titles, emails, addresses, phone numbers and IP addresses of 56,934,021 U.S. residents. There was a separate cache of data titled “Yellow Pages,” the report said, with 25 million records about businesses, including information such as names, company details, zip addresses, latitude/longitude, census tract, phone numbers, web addresses, emails, revenue numbers and more.
Hacken said it was unclear where the leak originated, but the formatting of the data appeared to have similarities to fields used by Canadian data management company Data & Leads. The database is no longer exposing information to the public, Hacken said.
Elasticsearch is an open-source tool intended to allow users to search data stored in private networks. The leaked data was exposed because the Elasticsearch tools were misconfigured for public access, Hacken said. It found the exposed data as part of a regular security audit using the search engine Shodan, which typically is used for finding specific kinds of computers on the open internet.
According to the report, Elasticsearch servers have been prone to malware and ransomware attacks in the past due to problems with authentication, allowing hackers to remotely assume complete administrative control.
As of Wednesday, Hacken reports that there have been at least three IPs discovered with the same Elasticsearch clusters configured incorrectly. While the first instance of the breach was catalogued two weeks ago, it is unclear how long exactly the exposed information was online.






