A phishing campaign with nation-state hallmarks is targeting Chinese government agencies

Hackers with possible ties to an advanced persistent threat (APT) group are trying to steal usernames and passwords of Chinese government officials as part of an apparent cyber-espionage effort, according to findings provided exclusively to CyberScoop prior to scheduled publication Thursday.
Researchers from the threat intelligence company Anomali have uncovered malicious websites with registrations dating back to November 2018 that impersonate email login pages from the Chinese Ministry of Foreign Affairs; China’s National Development and Reform Commission, an economic management agency under the State Council; and the National Aero-Technology Import and Export Corporation, a Chinese state-owned defense company.
While it’s not clear who exactly is behind the effort, CyberScoop independently verified the findings with three external threat intelligence practitioners, two of whom said with confidence the attack resembles a nation-state plot. All three spoke only on the condition of anonymity because they were not authorized to speak to reporters.
Upon discovering a website masquerading as a login page for the Chinese Ministry of Foreign Affairs, Anomali researchers found a family of five domains and close to 40 subdomains which rely on domain validation certificates issued by Let’s Encrypt, a free-to-use certificate authority. Along with the pages posing as Chinese government or state-owned organizations, other sites also impersonate a Hong Kong-based auction house and email service providers Gmail and NetEase Inc.
But the hackers apparently made a huge mistake. The group tied multiple subdomains to individual Let’s Encrypt certificates, allowing anyone who investigated the certificate to quickly determine all the sites were related.
One certificate with a validity period from April 23 through July 22 of this year was used for nine distinct subdomains, which then were disguised as login pages from China’s Ministry of Foreign Affairs, China’s National Aero-Technology Import and Export Corporation, the NetEase services 126.com and 163.com, and Poly Auction Hong Kong Ltd., an auction house.
The graphic below demonstrates how one certificate was used to mimic those five entities, according to Anomali. In this case, hackers registered the domain WinManagerService.net on Nov. 20, 2018 with NetEarth One Inc., using the European Union’s General Data Protection Regulation to mask the registrant’s information, Anomali found.
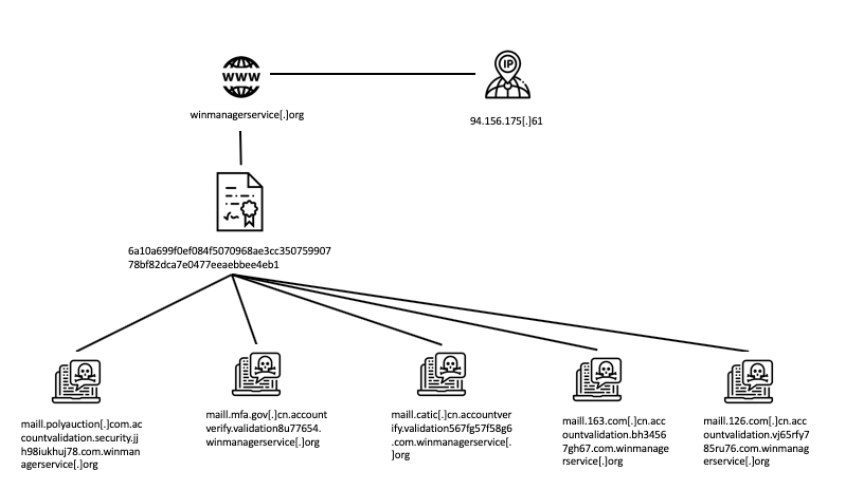
A graphic, provided by Anomali, detailing an apparent mistake by hackers.
“This is the same s— China is doing to us from the other side of the pond,” said one source outside Anomali. “It’s the equivalent of launching a business email compromise attack against a nation-state target. Based on the tactics, techniques and procedures, it’s not cybercriminals doing this for cash.”
Two of the three independent experts suggested the attack appears to be nation-state activity because of the organizations targeted; the use of Let’s Encrypt, which is known to be used by nation-state hackers and scammers alike; and most notably, the IP addresses involved, which two sources said they already have been tracking independently.
A third source questioned the idea that a capable nation-state is behind this attack, saying the magnitude of the mistake in tying multiple sites to the same certificate constitutes a level of sloppiness uncharacteristic of state-sponsored hackers.
One of the domains uncovered in the investigation was, in May 2019, attributed by the Chinese security vendor CERT 360 to be used by the APT group known as Bitter. Forcepoint first detected Bitter in 2016, revealing attacks against Pakistani targets. Since then, Tencent blamed Bitter for attacks on Chinese military, nuclear and government agencies, and Palo Alto Networks in February revealed the same group had started using a new hacking tool to target Pakistani and Chinese targets, as well as Saudi Arabian organizations.
“We expect to see BITTER APT continuing to target the government of China by employing spoofed login pages designed to steal user credentials and obtain access to privileged account information,” Anomali researchers wrote in their findings. The company did not speculate on which nation may be behind the Bitter APT, if any at all.
A high-level threat intelligence researcher told CyberScoop there was not enough evidence in the Anomali research to conclusively tie the phishing campaign to the Bitter APT, adding that the findings would “certainly” warrant further investigation.
Anomali has submitted the phishing pages used in the attack to Google and Microsoft for blacklist consideration.






