As threats increase, audit finds federal agencies struggle to implement cyber plans

A majority of federal civilian agencies examined by a government watchdog are struggling to implement cybersecurity programs capable of adapting to a changing threat landscape.
“Until agencies more effectively implement the government’s approach and strategy, federal systems will remain at risk,” the Government Accountability Office warned in a report Tuesday that assessed security implementation at the departments of Homeland Security, Justice, Energy and others.
Seventeen of 23 inspectors general said their agencies’ cybersecurity programs were not being effectively put into place, and that they had “significant information security deficiencies” in financial reporting controls, the GAO said. The audit is a reminder that, despite years of attention and billions of dollars spent, there is often a discrepancy between objectives and results in the cybersecurity of federal agencies.
Agencies were considered to have an “effective” cybersecurity program if they had, at a minimum, “quantitative and qualitative measures on the effectiveness of policies, procedures, and strategy” across their organization and used that information to make policy changes. Just six agencies met that standard.
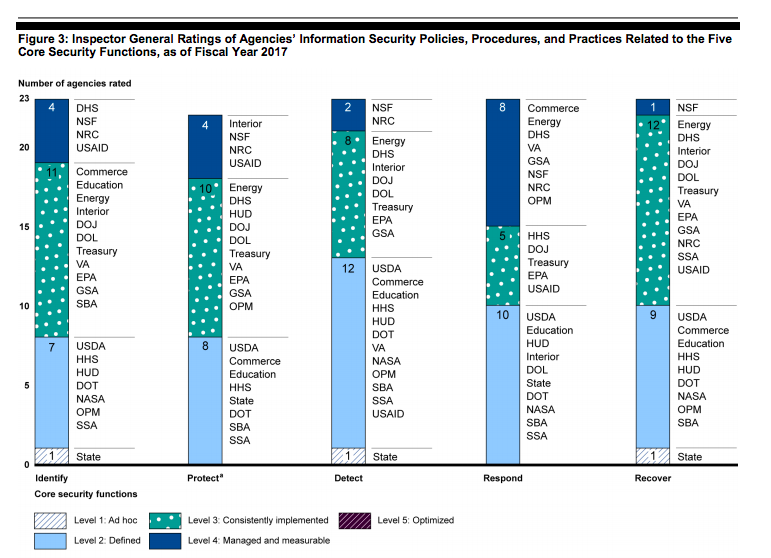
The report also offered a mixed verdict on federal handling of cybersecurity risk. While 13 of the 23 agencies were managing enterprise risk, the other 10 agencies “were at risk of ineffectively identifying, protecting, detecting, responding to, and if necessary, recovering from cyber intrusions,” the report concluded, citing findings from the Office of Management and Budget.
The audit comes at a time when the volume of threats is only increasing. In fiscal year 2017, agencies reported more than 35,000 cybersecurity incidents to the Department of Homeland Security, a 14 percent increase from the year before, according to OMB.
Roughly one-fifth of the incidents reported in 2017 stemmed from email and phishing, GAO said. Agencies have improved at preventing and detecting intrusions, but are still vulnerable to phishing attacks, the watchdog said.
One of the main federal tools for detecting and blocking malware is DHS’s National Cybersecurity Protection System, a multibillion-dollar program commonly known as Einstein. A 2016 GAO report found that Einstein had a “limited ability to detect potentially malicious activity entering and exiting computer networks at federal agencies.”
The latest GAO audit concluded that while Einstein’s capabilities had improved, it still had shortcomings, including an inability to scan encrypted traffic.
The audit also criticized a lack of available information about Einstein’s capabilities. In a report to Congress in September, Federal CIO Suzette Kent did not include a required assessment of whether Einstein is capable of blocking advanced persistent threats, GAO said. Kent also omitted a required cost-benefit analysis of Einstein capabilities and commercial technologies capabilities, and an assessment of the value of classified cyberthreat data and the ability of agencies to protect such sensitive data, the watchdog added.
“Until OMB updates the federal CIO report to address all of the requirements specified in the [Federal Cybersecurity Enhancement Act of 2015], it will continue to be remiss in providing timely and sufficiently detailed information…to congressional stakeholders to support their oversight responsibilities,” GAO said.
GAO said the agency “did not indicate whether it concurred” with the watchdog’s recommendations.
A Trump administration official told CyberScoop that analysis of Einstein’s capability of blocking advanced threats was included in an annual Federal Information Security Modernization Act report to Congress, and that the cost-benefit analysis “was omitted because the Eisenstein program contains classified indicators that could not be compared to commercial technology.”
GAO also advised Homeland Security Secretary Kirstjen Nielsen to direct DHS staff to work with OMB to study what is hindering agencies’ ability to implement intrusion-detection capabilities. DHS agreed with the recommendation and said it plans to carry it out in 2019.





