Shadow Brokers grow increasingly aggressive, threaten to dox former U.S. spy

Just 24 hours after a malicious worm infected thousands of computers across Europe, the now infamous Shadow Brokers group published a message celebrating the chaos, advertised a vague new “VIP service” and threatened an unnamed former NSA official for “writing ugly tweets.”
In a post on social media publishing site Steemit, the group also hinted at being in possession of FBI hacking tools. Until Wednesday, it was largely believed that only NSA-linked exploits had been published by the group.
The Shadow Brokers described a former NSA official “as a doctor living in Hawaii that owns a security company.” The group threatened to publish this person’s personal information — a practice known as “doxxing” — including their operational history at NSA. The person’s record included missions targeting Chinese nationals, the Shadow Brokers said.
“TheShadowBrokers is thinking ‘doctor’ person is former EquationGroup developer who built many tools and hacked organization in China,” the blog post reads. “If theshadowbrokers is not seeing subscription payment with corporate email address of doctor@newsecuritycompany.com then theshadowbrokers might be taking tweets personally and dumping data of ‘doctor’ persons hacks of China with real id and security company name. TheShadowBrokers is thinking this outcome may be having negative financial impact on new security companies international sales.”
At one point, there was speculation that Daniel Wolfford, an employee at United Arab Emirates-based cybersecurity company DarkMatter, was the Shadow Brokers’ target. Wolfford pushed back in a series of tweets Wednesday morning.
https://twitter.com/drwolfff/status/879960675610537984
This is not the first time that the group has accused someone of being part of the spy agency’s elite “Equation Group,” which is thought to conduct some of the NSA’s most sensitive missions.
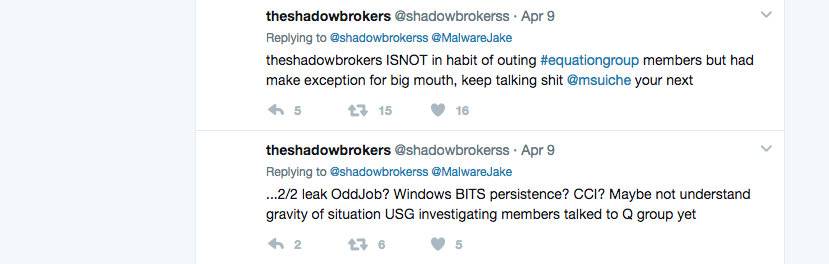
Archived tweet by TSB mentions @MalwareJake and @Msuiche
The Shadow Brokers also previously posted a thinly veiled threat aimed at Jake Williams, the now CEO of Rendition InfoSec and a former NSA employee, for speaking critically about them. Williams is open about his past in government.
“I have changed some travel plans as a result and changed some of my behavior, especially while abroad. But I did not contact any government agency,” Williams said of his reaction to the Shadow Brokers’ past tweets. “Their Twitter is being monitored by law enforcement.”
Other similar accusations have been false, though. For example, earlier this year the Shadow Brokers alluded to the fact that Comae Technologies’ founder Matthieu Suiche was a member of the Equation Group. Suiche, a French citizen, says he has never worked for the NSA in any capacity.
“Theshadowbrokers is including mystery gift. Mystery gift is mystery to theshadowbrokers as well,” the group wrote in broken English. “But be enjoying at own risk. Smelling hidden service FBI hackish.”
Experts say the group writes in broken English as a way to obfuscate members’ identity.
Last summer, when the Shadow Brokers posted their first message online, the prominent theory was that a mysterious collective of hackers had somehow broken into a poorly configured NSA staging server, which stored sensitive hacking tools intended for a cyberattack. The thinking at the time was that these leaks would be limited to data tied to a faulty attack server.
However, there’s evidence that contradicts that theory.
In January, CyberScoop reported that a subsequent release of NSA-linked Microsoft exploits published by the group appeared to have instead come from removable media, like an operational disk, which would traditionally reside within a classified and secure environment.
In April, the Shadow Brokers published an internal Microsoft Powerpoint presentation of an NSA mission focused on the Middle East. A Powerpoint presentation would not be stored on a staging server that sits off premise, former intelligence officials say.
Both the Washington Post and New York Times have previously pointed to the source of the Shadow Brokers’ leaks as veteran intelligence community contractor, Harold T. Martin, who once held a high-level clearance and for some period of time worked closely with the NSA’s Tailored Access Operations.
A federal investigation into the Shadow Brokers is ongoing, although the NSA has never publicly acknowledged that agency’s tools were openly published in recent months.
The Shadow Brokers is expected to begin sharing yet another cache of NSA software exploits on July 1.





