New OWASP Top 10 includes Apache Struts-type vulns, XXE and poor logging

The latest draft of the Open Web Application Security Project’s list of Top 10 software vulnerabilities, a replacement for the draft that caused such pushback earlier this year, includes three new categories of security flaws.
The three new vulnerability categories are:
- XML External Entity (XXE), the kind of vulnerability that powered the Billion Laughs attack
- Insecure Deserialization, like the Apache Struts vulnerability that was left unpatched at Equifax, enabling the massive data breach there over the summer
- Insufficient logging and monitoring
The new categories were derived from more than 40 vulnerability datasets submitted in response to an OWASP data call; and from 515 responses to a questionnaire emailed to members of the security community.
The top two on the canonical list — injection vulnerabilities, like those found in SQL databases and broken authentication and session management — remain unchanged from the last version, published in 2013.
Sensitive data exposure moves up from sixth to third, and cross site scripting (XSS) falls from third to seventh.
Two vulnerabilities — insecure direct object references (fourth) and missing function level access control (seventh) — have been merged into broken access control (fifth).
Another two have fallen off the top ten altogether:
- Cross-site request forgery, eighth in 2013, is only present in fewer than 5 percent of the new data set the authors collected. It fell to thirteeth.
- Unvalidated redirects and forwards was tenth in 2013, but was detected in less than 1 percent of the new data set. It fell to twenty-fifth.
The draft replaces one that provoked a firestorm of protest when it was issued in May, with people accusing the authors of nepotism and corruption on social media. Those authors subsequently resigned and handed the update task to a new team.
The list was first released in 2003 and has been updated roughly every three or four years.
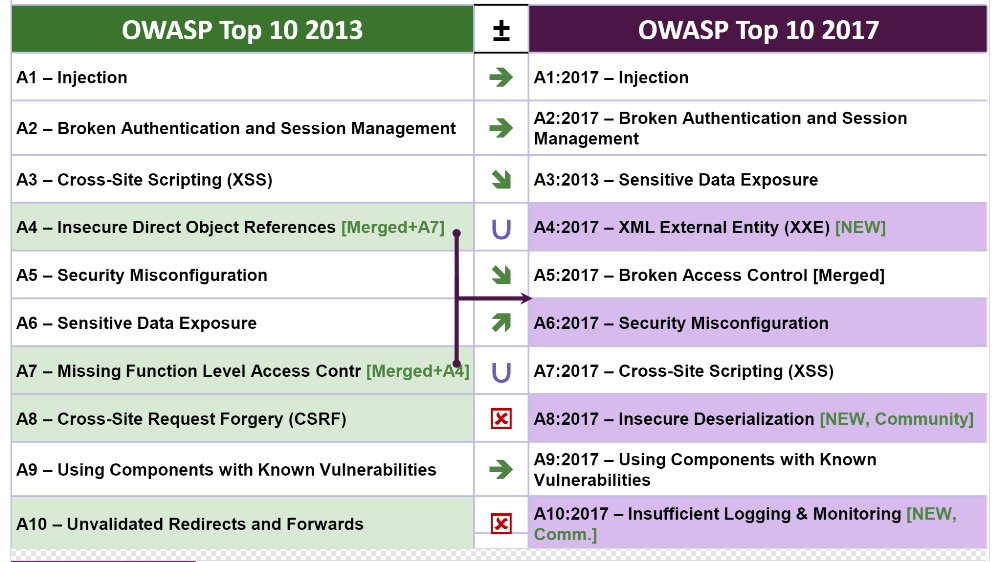
OWASP Top Ten, existing (2013) and proposed (2017).
The list is the most downloaded document on their website, the organization says.