GAO: Pentagon hasn’t met conditions for separating NSA and Cyber Command

The Department of Defense has not finally decided whether to separate the leadership of the National Security Agency and U.S. Cyber Command and has not begun to meet the congressionally mandated conditions for doing so, the Government Accountability Office said in a report Tuesday.
A provision in last year’s National Defense Authorization Act required the Secretary of Defense and the chairman of the Joint Chiefs of Staff to jointly certify that ending the so-called dual-hat arrangement — under which the same four-star general is both NSA director and in charge of U.S. Cyber Command — will not pose risks to the command’s military effectiveness.
“As of April 2017, DOD’s senior leaders had not decided whether the dual-hat leadership should be ended,” states the GAO report, adding that department’s leaders were “reviewing the steps and funding necessary to meet the statutory requirements of Section 1642” but had not yet begun to do so.
The NDAA provision requires the department to assess Cyber Command’s operational dependence on NSA and evaluate each organization’s ability to carry out its roles and responsibilities once the leadership is separated. It further requires DOD to ascertain whether the following conditions have been met before deciding to end the dual-hat leadership arrangement:
- A robust operational infrastructure has been deployed that is sufficient to meet the unique cyber mission needs of both Cyber Command and NSA
- Robust command and control systems and processes have been established for planning, deconflicting, and executing military cyber operations
- The capabilities have been established to enable intelligence collection and operational preparation of the battlefield for cyber operations.
- The capabilities have been established to train cyber operations personnel, test cyber capabilities, and rehearse cyber missions.
- Cyber Mission Force Teams have achieved full operational capability.
The last condition is not expected to be met until September 2018.
In addition, another part of the NDAA requires DOD to elevate Cyber Command from a sub-unified command under U.S. Strategic Command to a unified combatant command. “If and when [Cyber Command] becomes a combatant command, it will have more ability to influence policy and operational planning, including by defining requirements within the cyber domain,” a staffer from the office of Sen. Mark Warner, D-Va., said, “It should also benefit from more people, better funding, and broader authorities.”
Among House Democrats, there was less patience. “Congress fully expects the Trump administration to comply with the law by updating the Unified Command Plan [to make Cyber Command a full-fledged combatant command], and is dismayed elevation has not yet occurred. Such a delay poses great risk to national security,” Rep. Adam Smith, the ranking Democrat on the House Armed Services Committee, told CyberScoop by email.
Tuesday’s GAO report was requested by Congress in the committee reports accompanying both the NDAA and the Intelligence Authorization Act last year.
The report also assesses the pros and cons of ending the dual-hat arrangement, which dates back to the stand-up of Cyber Command in 2010 — and outlines a series of actions that the department could take to mitigate any risks associated with the separation. One of them is elevating Cyber Command to unified combatant command status.
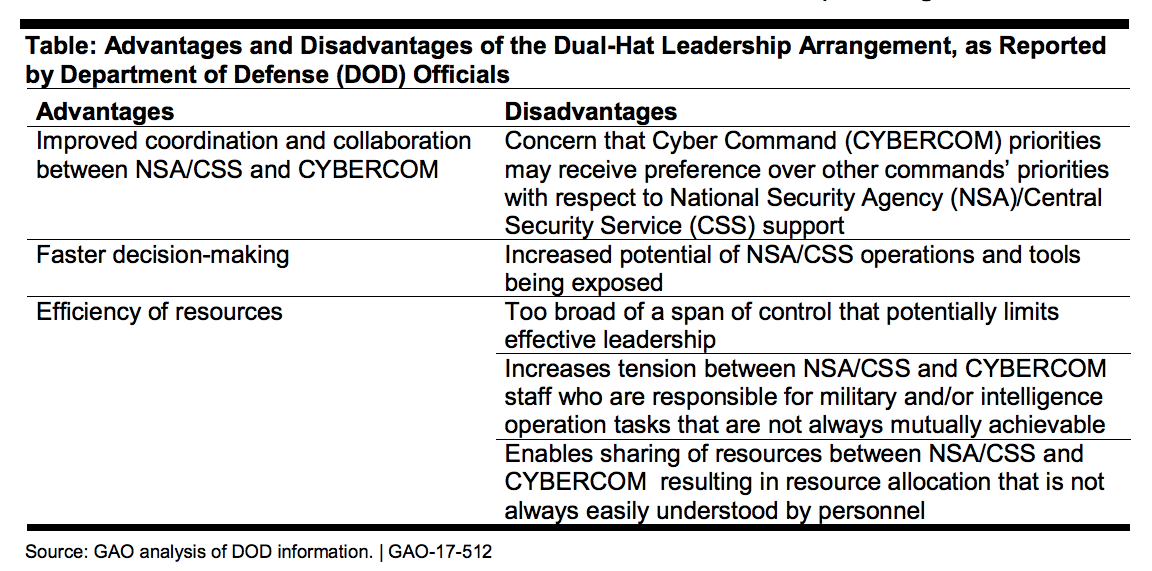
Other risk mitigation measures identified are:
- The formalization of agreements between NSA and the command “to ensure collaboration on key issues … officials told us there are advantages afforded to both organizations by the dual-hat leadership arrangement that they are working to formalize … an agreement has been drafted, but not approved.”
- The achievement of full operational capability for all 133 Cyber Mission Force Teams.
- The development of a persistent cyber training environment to provide a realistic, on-demand training capability.
The report also states that DOD has implemented just over half (15) of the 27 cybersecurity recommendations made by the GAO from 2011 to 2016. The 56 percent success rate is slightly lower than the 60 percent rate for GAO information security recommendations across the federal government as a whole, the report notes.





