Major Iranian IT vendor paying large ransom to resolve recent cyberattack

An Iranian IT vendor that works with many of the nation’s top banks and some of its government entities suffered a severe cyberattack and is in the process of paying a ransom in installments, according to emails and blockchain data reviewed by CyberScoop, contrary to claims from the Iranian government that a hack never occurred.
The company, Tosan, provides IT services to 45% of the country’s banks, serving 27 million Iranians, according to the company’s website. The attack gave hackers access to data belonging to at least 20 of Iran’s 29 active credit institutions, including those with government clients, according to Politico Europe, which first reported the news Wednesday.
IRLeaks, the group that claimed responsibility for the attack, wrote in a since-deleted Aug. 9 post on its Telegram channel that if a deal was not reached, the group would put the data it obtained up for sale. The data included “complete details of several million bank customers,” according to the message, including account numbers, full names, dates of birth, nationalities, addresses, “precise” transaction details and more. The impact of the attack is unclear.
The group did not respond to a request for comment sent to the email address listed in the since-deleted message. The company also did not respond to a request for comment.
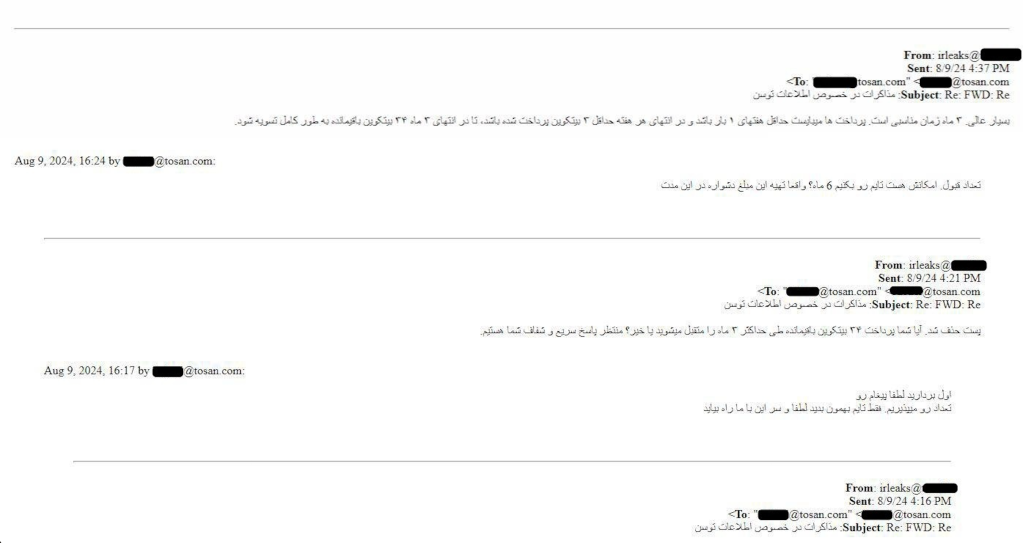
Emails between IRLeaks and Tosan CEO Arash Babaei — obtained by a third party, shared with CyberScoop and verified by a separate source familiar with the matter — show the two sides negotiating payment beginning Aug. 8. After Tosan asked IRLeaks to remove the Aug. 9 Telegram message, which the group did, Tosan sent 1 bitcoin to an address provided by IRLeaks, and IRLeaks acknowledged receipt.
The two sides agreed to an initial payment of 1 bitcoin followed by a payment schedule of 3 bitcoin per week until a total of 35 bitcoin is paid. The wallet has so far received roughly 10 bitcoin worth about $561,000.
Jackie Burns Koven, head of cyber threat intelligence at Chainalysis, told CyberScoop that the wallet in question has received payments from at least two different Iranian exchanges, “which could be consistent with payments from Iranian victims.”
The wallet had received $1.1 million in total between Sept. 3, 2023 and Sept. 2, 2024 across 60 deposits. The wallet was also used to purchase IT infrastructure, including domains and hosting services, Koven said. IRLeaks, which has nearly 19,000 subscribers on Telegram, has claimed attacks on various other Iranian government targets since first emerging online in July 2023.
Iran International, a London-based news organization often critical of the Iranian government, said in an Aug. 14 post on X that a “major cyberattack has targeted the Central Bank of Iran (CBI),” adding that “initial assessments indicate this could be one of the largest cyberattacks ever against Iranian state infrastructure.”
The Mehr News Agency, based in Tehran, reported the same day that the Central Bank of Iran said that “no system in the Central Bank and the banking system in general has been hacked,” and that “hostile media are trying to disturb the mental peace of the society by publishing fake news about the hacking of the central bank system,” according to a Google translation.
The Iranian government has suffered a series of significant cyberattacks over the past couple of years. In May 2023, for instance, a person calling themselves GhyamSarnegouni — roughly translated to “uprising until overthrow” — began posting documents they claimed they obtained by compromising “the entire highly protected internal network of the executioner’s presidential institution,” referring to then-Iranian President Ebrahim Raisi.
That group first emerged in January 2022 with the hacking and disruption of Iran’s national broadcast service. Other attacks tied to the group include the June 2022 hack of more than 5,000 municipal CCTV cameras in Tehran, and an early May 2023 hack of the Iranian ministry of foreign affairs, which included more than 200 defaced websites and the publication of a trove of sensitive internal government files.
The group continues to post internal Iranian government documents almost daily.
Other personas have similarly taken their own shots at Iranian government targets, including Black Reward, Tapandegan and Lab Dookhtegan. Another group, known as Predatory Sparrow, which has possible ties to Israel, targeted steel mills it said were tied to the Islamic Revolutionary Guard Corps (IRGC), posting a video after the apparent breach showing what appeared to be the inside of an industrial facility.




