North Korean hackers came close to hacking Hillary Clinton’s presidential campaign
As part of a cyber-espionage operation against Hillary Clinton’s 2016 presidential campaign, North Korean hackers compromised email accounts belonging to individuals involved with an East Asia-focused foreign policy advisory group, multiple people familiar with the incident told CyberScoop.
The North Koreans sought to acquire policy documents and other relevant information that may have affected the regime if Clinton were to become president, the sources said. The advisory group’s job was to craft such policies.
The hackers were able to break into the email accounts of employees of at least one prominent D.C.-based think tank; some of them were involved with the East Asia foreign policy advisory group. These individuals occasionally communicated with staff of the Democratic candidate’s official Hillary for America (HFA) campaign, based on an incident response report obtained by CyberScoop and authored by security experts who worked for the presidential campaign.
The attackers used their access to apparently draft convincing spearphishing emails that were then sent to other associates of the campaign. In addition, the North Korean hackers sent phishing emails from random email accounts which were made to look as if they had come from an authentic and familiar address used by one campaign official.
The East Asia foreign policy advisory group was made up of volunteers and organized outside of the campaign; members were not campaign employees, nor did they rely on campaign computer systems.
No internal Hillary for America (@HillaryClinton.com) email accounts were breached as part of this specific North Korean phishing activity, according to multiple people familiar with the matter. The evidence obtained by CyberScoop does not show that the campaign itself was hacked, but rather that an outside group of advisors was heavily targeted and in some cases their emails accounts were compromised.
In at least one known case, the attackers spoofed a Clinton campaign official’s email address in order to send a highly targeted phishing email to a veteran Senate Foreign Relations Committee staffer, the internal security report notes.
Spoofing an email account typically involves using a known, legitimate contact address in a forged email header so that the message appears to have originated from someone other than the actual source. A spoofed email account does not mean an account was breached.
Clinton campaign staffers became widely aware of the North Korean operation around February 2016, after the aforementioned security document was circulated inside the organization. This report, which details the hacking effort, was completed one month before the widely publicized hack of a private email account used by top Clinton adviser John Podesta.
The North Korean hackers targeted the foreign policy advisory group, which was largely made of employees of D.C.-based think tanks, by using a popular email phishing technique. A variation of this same technique was also employed by Russian hackers against Podesta to steal his Gmail login information.
There is no evidence to suggest the North Korean campaign is in any way tied to the now infamous Russian cyberattacks that targeted the Democratic National Committee and Democratic Congressional Campaign Committee.
A group of private sector cybersecurity analysts, in addition to in-house security experts and U.S. law enforcement officials, attributed the February 2016 operation to North Korea’s Reconnaissance General Bureau, or RGB, a former U.S. official told CyberScoop.
The government official, like other sources CyberScoop spoke to for this story, spoke on condition of anonymity to discuss a sensitive investigation that until today had remained secret.
“This phishing attack fits a pattern of previous successful attacks against [non-governmental organizations] and U.S. government-based entities which align to an Asian nexus. We are highly confident this is North Korea’s RGB, focusing on intelligence gathering,” the former U.S. official said.
While Clinton’s cybersecurity team quickly responded to this threat and took steps to mitigate any subsequent risks to campaign staff, the timing and source of these cyberattacks highlights the contemporary cybersecurity challenges facing major political campaigns.
Additionally, it shows some Clinton staffers were aware that the campaign was in the crosshairs of hackers backed by nation-states prior to the public learning of Russia’s efforts to meddle in the U.S. election.
The RGB sought to acquire information about policies that may have been instituted by a Clinton administration, the former U.S. official said. CyberScoop obtained a copy of this security report and a sample of one phishing email sent to East Asia policy team members. CyberScoop is not publishing the full report or phishing email because it contains names and personal contact information of possible victims.
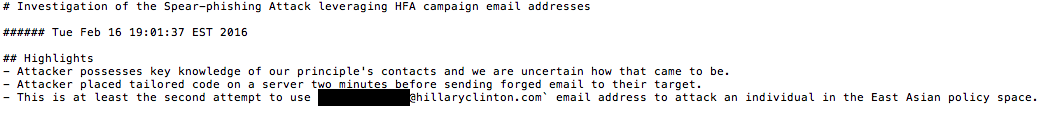
An excerpt from a campaign incident response report – screenshot by CyberScoop
The report itself mentioned evidence of a spoofed Hillary for America account sending out stealthy phishing emails. Cybersecurity experts hired by the campaign were aware of these phishing attempts and moved swiftly to warn both campaign staff and external advisers.
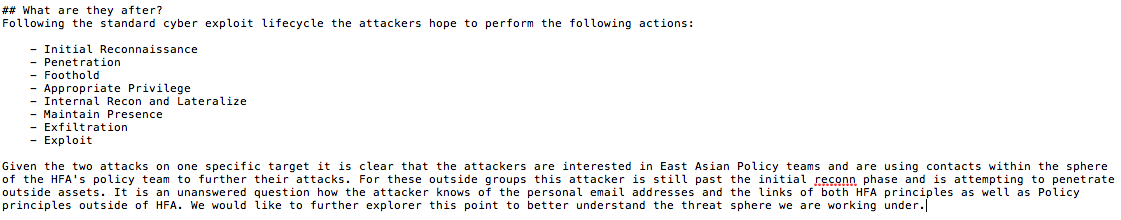
An excerpt from a campaign incident response report – screenshot by CyberScoop
An individual who received one of these phishing emails told CyberScoop that hackers were familiar with past email correspondence and the topics discussed between members of the external foreign policy-focused group. The attackers possessed knowledge of principal campaign contacts, language style, job titles and concurrent projects — which indicated the hackers likely conducted some sort of surveillance beforehand.
“It sort of became really obvious, really quickly that this wasn’t just someone spoofing sender information and sending us a computer virus,” said one former campaign associate. “It seemed much more coordinated. They knew who everyone was and at least broadly, what we were talking about … I think they probably took advantage of that.”
The phishing emails tied to this operation, some of which were reviewed by CyberScoop, did not contain malware, but rather relied on a social engineering scheme. When recipients opened one of these phishing emails, they would be asked to access a document via a link. That link would lead to a fake Google Login image, where the target would then be again asked to input credentials to access the apparent document or presentation. This phishing technique is now fairly well known.
By structuring the email-based attacks in such a manner, the North Korean hackers were able to gather email passwords without deploying malware that could be detected by an antivirus product.
“You could basically set your watch for it”
Beyond the East Asia policy group-focused attacks, the same North Korean hackers were also sending other phishing emails to Clinton campaign staffers, a person with knowledge of the operation told CyberScoop. The volume of these attempted intrusions spiked whenever a major news development occurred concerning North Korea.
“Whenever they would launch a missile, you know do a test or something, you could basically set your watch for it. After a few hours, you would see their emails start to roll in,” the source said. In most cases, those phishing emails carried an attachment or link to a news article about the missile launch.
It’s not clear how much intelligence North Korea gathered from the Clinton campaign or its associates as part of this operation.
In May 2016, then-Director of National Intelligence James Clapper said, during a public event in Washington, D.C., that the U.S. intelligence community had seen “indications” of hackers targeting U.S. presidential campaigns. He did not elaborate further at the time. The FBI is the lead agency that would handle such incidents.
The FBI declined to comment for this story.
Nothing new
Experts say that North Korea’s ongoing phishing attempts are just a continuation of a more than decade-long effort by foreign powers from across the globe to hack into and steal information from U.S. political campaigns.
In 2008, a group of hackers believed to be linked to China spied on Democrat Barack Obama’s and Republican John McCain’s presidential campaigns. In a similar vein, the Chinese hackers were also focused on acquiring policy papers.
Although this sort of hacking activity is not new, as political campaigns have long been a target for cybercriminals and nation states alike, these types of attacks are becoming more frequent, said Jake Braun, a former White House Liaison to the Department of Homeland Security during the Obama administration.
“In terms of volume, I think yes we’re definitely seeing more of it. Nation states realize that basic techniques work against political campaigns,” Braun said. “Phishing emails are popular because they offer the path of least resistance. They’re effective.”
North Korea’s RGB has been extremely active in the cybersecurity realm over the past few years. Earlier this year, the United Nations announced it was looking into Malaysian-based businesses that possibly served as RGB fronts in efforts to shirk economic sanctions.
The RGB has also been tied to The Lazarus Group, which stole $81 million from the central bank of Bangladesh in a heist that ran through the Federal Reserve Bank of New York.






