North Korean hackers posed as Meta recruiter on LinkedIn

A North Korean cyberespionage operation targeted employees of an aerospace company in Spain using a previously unreported backdoor and a creative phishing campaign featuring a phony Silicon Valley recruiter, demonstrating a “significant advancement in malicious capabilities,” researchers with the cybersecurity firm ESET said Friday.
Hackers linked with North Korea’s Lazarus Group — an umbrella term for a collection of North Korean cyber units — posed as a recruiter for Meta and contacted employees of the unnamed company via LinkedIn and sent two coding challenges supposedly part of the hiring process but which were in fact laced with malware, Peter Kálnai, an ESET researcher, wrote in a report published Friday.
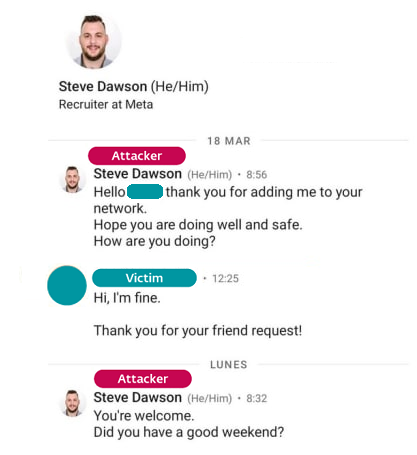
The operation, carried out some time last year, is just the latest example of North Korean-linked cyber operations using phony job opportunities to target various professionals, including journalists, security researchers and software developers, among others.
The ostensible coding challenges were contained in malicious files named “Quiz1.exe” and “Quiz2.exe” and when downloaded and executed on a company device delivered a remote access trojan ESET dubbed “LightlessCan.”
The malware mimicked a “wide range of native Windows commands,” Kálnai said, and enabled “discreet execution within the RAT itself instead of noisy console executions.”
The “strategic shift enhances stealth, making detecting and analyzing the attacker’s motives more challenging,” he said. The malware was also set to decrypt only on an intended target’s machine, “effectively preventing decryption on unintended machines, such as those of security researchers.”
LightlessCan has support for up to 68 distinct commands, he added, but only 43 are implemented in the current version of the malware with some functionality, suggesting the potential for ongoing development and refinement.






