OAuth-based phishing campaign gives Gmail users a scare

An immense phishing campaign targeting Google accounts hit a wide array of journalists, government employees, academics and private company email accounts.
This is what the attack looks like:
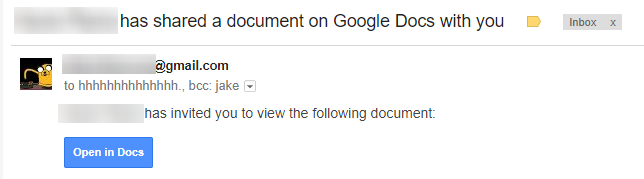
The email has been landed in newsrooms from BuzzFeed to ABC, at universities and reportedly from addresses within the Chicago city government.
The “Open in Docs” link redirects to the OAUTH2 service on accounts.google.com, according to researcher Bojan Zdrnja, where it asks for full access to the GMail account and all contacts from an application deceptively named “Google Docs.” Once access is granted, the attacker uses that account to send phishing emails to every contact in the victim’s contact list.
OAuth is a mechanism companies like Google use that allows users to authorize apps and websites to access account information without giving away a password. For example, a third-party email app will want access to your GMail and will ask for permission through OAuth.
Google promptly pulled the application’s OAuth page a few hours after learning about the campaign.
The attack is extremely similar to last year’s phishing campaign by APT28, suspected of being a Russian intelligence operation, against U.S. political targets and others. Cybersecurity firm Trend Micro described that campaign in a recent report.
“Once OAuth access has been authorized, the target account can be accessed until the user or the provider revokes the token,” Trend Micro researchers wrote. “If the target changes his password, the actor can still use the OAuth token to access the mailbox. In this case the target might have a false sense of security.
According to security researchers, the following domains are included:
googledocs[.]docscloud.download
googledocs[.]docscloud.info
googledocs[.]docscloud.win
googledocs[.]g-cloud.pro
googledocs[.]g-cloud.win
googledocs[.]g-docs.pro
googledocs[.]g-docs.win
googledocs[.]gdocs.download
googledocs[.]gdocs.pro
googledocs[.]gdocs.win
Victims of the attack can’t simply change their passwords. Victims have to log into their Google accounts and remove permissions for the rogue application named “Google Docs.”



