DHS cyber incubator graduates malware ‘playback’ tech

A software package that records and “replays” the operation of malware is the latest technology to graduate from a Department of Homeland Security cybersecurity incubator.
The technology, REnigma, allows network defenders to quickly see exactly how an attack unfolded and work out how best to recover, DHS official Nadia Carlsten told CyberScoop.
“It’s all about getting the analysts the facts as fast as possible — and as accurately as possible,” she said.
The software was developed at the John Hopkins University Applied Physics Laboratory and will be licensed to Deterministic Security LLC — a startup founded by the two scientists who wrote it.
The Oregon-based company becomes the 15th successful graduate from the DHS Transition To Practice (TTP) incubator, said Carlsten, the program’s manager.
“The developers wanted to take their technology into the marketplace themselves,” she said.
Run in the Cyber Security Division of DHS’s Science and Technology Directorate, TTP selects candidate technologies from federal laboratories or university affiliated research centers like JHU-APL in the hope of preparing them for the commercial marketplace within three years.
REnigma, which was recruited just last year, has graduated ahead of schedule, Carlsten said, becoming the first spinoff from JHU-APL and the first commercial graduate from the 2016 cohort.
The REnigma program runs malware on a virtual machine, much like a conventional sandbox — an isolated system on which malicious code can safely be “detonated,” to find out what it does.
But unlike a regular sandbox, REnigma uses “Record and Replay” technology to precisely and completely record the execution of malicious code, so that cyberdefenders can play it back and analyze the execution in detail.
“The difference is … you can replay exactly what the malware does,” Carlsten said.
The technology “provides many powerful techniques for malware analysis that are not possible today because it enables the … analyst to ‘rewind’ to any previous state in the system,” reads a description of REnigma in the TTP catalogue. “For example, if a malicious code sample outputs encrypted data on the network, an analyst can use REnigma to backtrack to the plaintext data in memory or recover the encryption key used for exfiltration.”
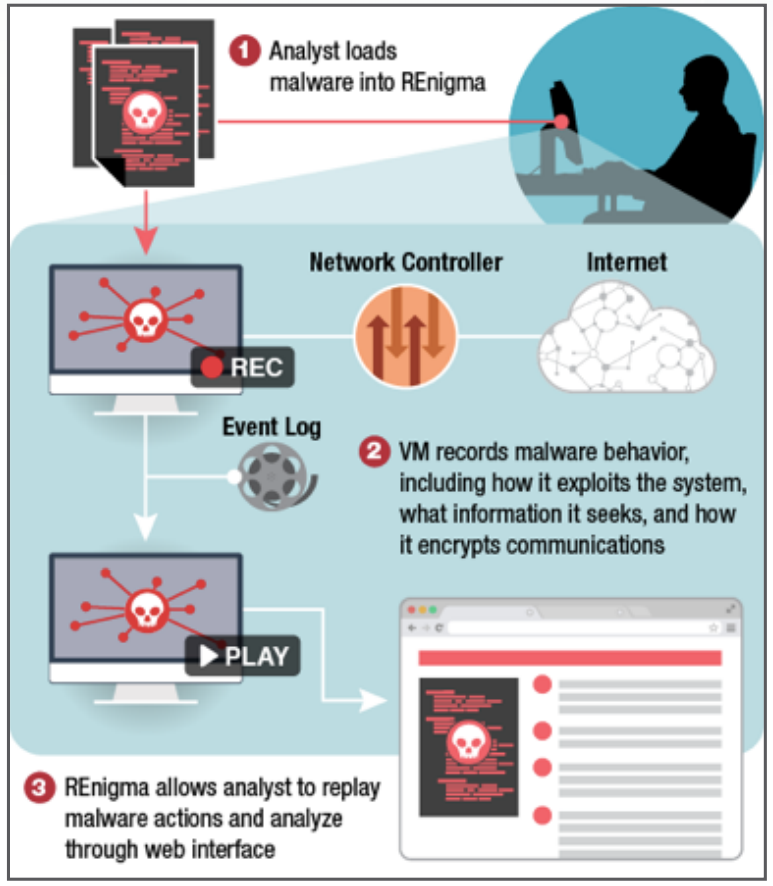
The three stages of REnigma malware analysis (Source: DHS)
The co-founders “plan to bootstrap it for the first couple of years,” Carlsten said, meaning they don’t plan to seek venture capital backing immediately. “They want to run a couple of pilots, probably with large commercial enterprises or government agencies” to demonstrate the value of the product, before seeking funding, she added.
TTP is one of the Science and Technology programs slated for closure under the Trump administration’s budget plan, but Carlsten said that would not impact any of the technologies the program was already working on. “We will continue working to graduate these technologies,” she said of the 40 TTP-backed efforts.
“The success of the program speaks for itself,” she said, declining to comment on the budget issue. “No one has questioned how well the program has gone or the value of the work we’re doing.”
Nadia Carlsten spoke with CyberScoop at the 2017 RSA Conference about how DHS is funding cybersecurity startups:



