How phishing emails sent by Russian hackers produce propaganda

In late 2015, former Director of National Intelligence James Clapper famously warned of a future where adversaries will often “change or manipulate electronic information in order to compromise its integrity” rather than simply steal data. Since then, the world has watched the Kremlin carry out Clapper’s prediction, interfering in democratic processes around the world.
A new report released this week by the Citizen Lab at the University of Toronto’s Munk School of Global Affairs shows how Russia has made Clapper’s prediction a reality. The research gives a new view on how hackers with suspected ties to the Russian government play a vital part in international disinformation campaigns aimed to discredit enemies of the state and sow discord.
The report, “Tainted Leaks: Disinformation and Phishing With a Russian Nexus,” underscores how offensive cybersecurity operations have become a critical tool used by governments to weaponize information and affect public opinion.
Hackers acting in the apparent interest of the Russian government are actively sending phishing emails, and manipulating leaked information in some cases, in more than 28 countries, Citizen Lab found. At least 200 individuals living across the globe, including a former Russian prime minister and Ukrainian military official, were identified as being sent related booby-trapped emails.

Targeting information obtained by Citizen Lab
This campaign has already targeted a variety of victims and sectors, including governments, industry, military, media and civil society groups. The approach and techniques used in the operation appear similar to recent digital attacks on French President Emmanuel Macron’s campaign, according to data collected by Citizen Lab.
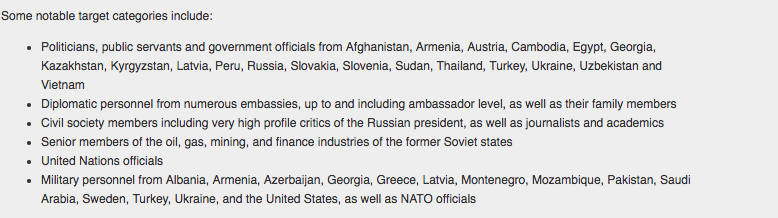
targeting information obtained by Citizen Lab
In one case, a prominent journalist working to expose corruption in the Russian government was successfully targeted, hacked and had his emails leaked. Notably, some of these documents contained falsified information mixed with authentic messages. The result played out in state-owned media, where some Russian news outlets selectively reported on certain information supposedly taken from the inbox of David Satter, a renowned journalist and author.
Satter originally received a nondescript phishing email last October, which researchers now believe effectively served as the first step in a complex and expansive propaganda effort.
Central to the Satter incident is this group CyberBerkut, an entity shrouded in mystery that has been actively involved in a cross-border information operation aimed at shifting public opinion cornering Russian occupation in Ukraine.
One email shared by CyberBerkut described a conspiracy by Satter to plant misleading and scandalous news articles in local publications that opposed the Russian government. The email proved to be fake, Citizen Lab found. RIA Novosti and Sputnik Radio picked up the story and reported the leaked email showed a CIA plot to discredit Russian officials.
The report also notes digital evidence linking CyberBerkut to APT28, or Fancy Bear, an infamous hacking group that became well known last year after breaking into the files of the Democratic National Committee. By analyzing a URL shortening service used by both threat actors named tiny.cc, researchers found a series of commonalities tied to a single user. One of the URLs created by this single user was used in phishing emails sent to journalists working for independent news outlet Bellingcat.
While the evidence is inconclusive, the research adds to a mountain of information published in recent months by a cohort of other security researchers that detail the known activities and tools commonly employed by Russian hackers.
“We have no conclusive evidence that links these operations to a particular Russian government agency; however, there is clear overlap between our evidence and that presented by numerous industry and government reports concerning Russian-affiliated threat actors,” the report reads.





