Unidentified attackers breach tens of thousands of Cisco devices

Tens of thousands of physical and virtual devices running Cisco networking software have been compromised as the result of a yet-unpatched vulnerability, according to multiple independent researchers.
Cisco issued a security advisory Monday warning of “active exploitation” of its IOS XE software but did not share details on the scale of the issue. Successful exploitation of the vulnerability would grant an attacker “full control of the compromised device” and allow “possible subsequent unauthorized activity,” the Cisco’s Talos threat intelligence group said in the alert.
The previously unknown vulnerability has been designated CVE-2023-20198.
By Tuesday, using indicators shared by Talos, researchers began to quantify the scale of compromised devices. Jacob Baines, the chief technical officer with VulnCheck, wrote that Cisco’s blog post “buried the lede by not mentioning thousands of internet-facing IOS XE web interfaces have been implanted.”
Later in the day, researchers with Censys reported observing 34,140 devices “that appear to have the backdoor installed.” Censys’ data pointed to tens of thousands of compromised devices around the world, the majority of which are in the U.S.
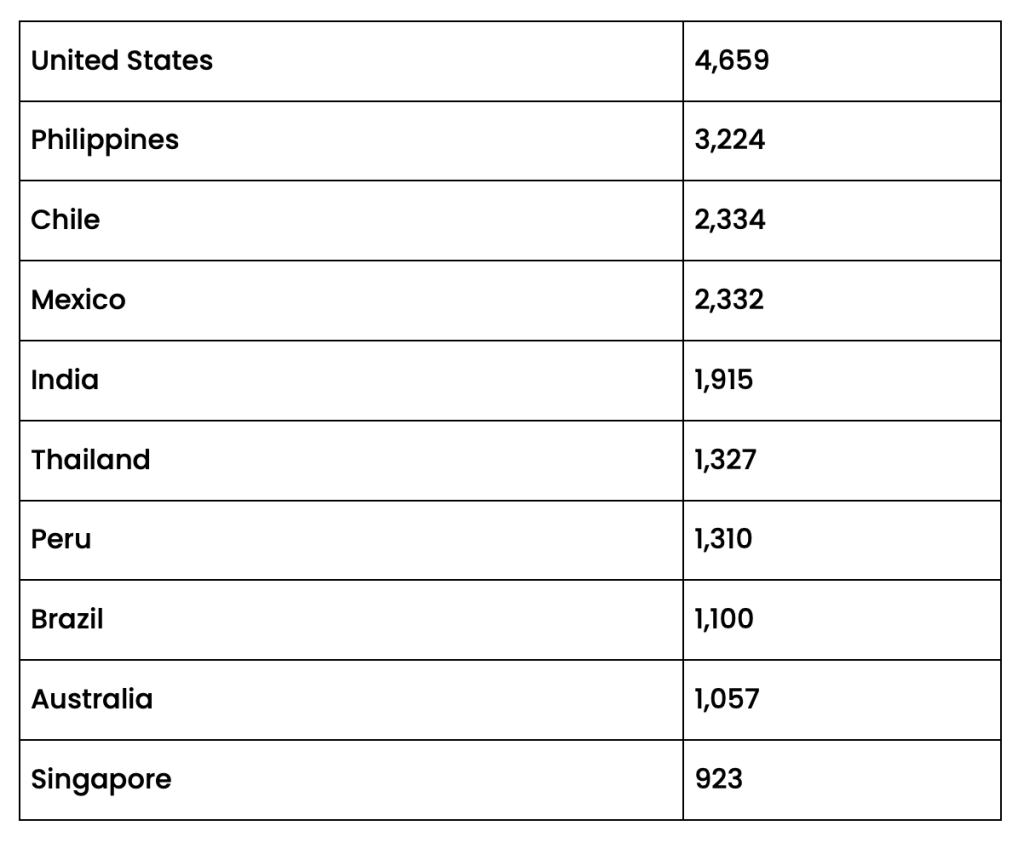
An analysis of the autonomous systems associated with the device IP addresses, which offers indications of the types of organizations involved, suggests “they predominantly represent telecommunications companies offering internet services to both households and businesses,” the Censys researchers reported.
A Cisco spokesperson told CyberScoop late Tuesday that the company is “working non-stop to provide a software fix and we strongly urge customers to take immediate action as outlined in the security advisory.”
Cisco became aware of the issue on Sept. 28, when it was reported to the company’s Technical Assistance Center, according to the Talos blog. An analysis showed that “related activity” began as early as September 18.
It’s not clear who is behind the compromises, but they “were likely carried out by the same actor,” the Talos blog read.
The attackers leveraged a previous vulnerability, CVE-2021-1435, which Cisco patched in 2021, to install the implant after gaining access to the device, according to Talos. “We have also seen devices fully patched against CVE-2021-1435 getting the implant successfully installed through an as of yet undetermined mechanism.”
U.S. government and cybersecurity industry officials have in recent months warned that advanced hacking groups are increasingly targeting so-called edge computing devices, like routers and firewalls. Targeting edge devices allows attackers of all kinds to gain access on systems that defenders have limited visibility into, Francisco Donoso, the chief technical officer of the cybersecurity firm Lodestone, told CyberScoop in an online chat Wednesday.
The vulnerable Cisco IOS XE firmware is used across a “fairly broad range of Cisco products including enterprise switches, wireless controllers, access points, industrial routers, virtual appliances, and other Cisco networking solutions,” Donoso said.
There is no easy way to validate the integrity of such devices, and most organizations likely don’t know their devices are internet-exposed, he added. And while the implant currently does not seem to survive a reboot, “these systems, particularly in telecom, remain online for significant amounts of time (sometimes years),” he said.
Now that this campaign has been exposed, attackers could potentially be mass spraying the exploit and implant in an attempt to gain initial access to as many organizations as possible and “will then triage which orgs are of value for further attack activity once the implant is deployed as widely as possible,” Donoso added.
Updated, Oct. 18, 2023: This article has been updated with additional comment from Francisco Donoso.





