Chinese hackers found and repurposed elite NSA-linked tools

A hacking group with ties to Chinese intelligence has been using tools linked to the National Security Agency as far back as March 2016, according to research from security firm Symantec.
The tools include some released by the Shadow Brokers, a mysterious group that dumped computer exploits once used by the NSA on the open internet in April 2017. Symantec’s research suggests that the Chinese-linked group, which the company calls “Buckeye,” was using the same NSA-linked tools at least a year before they were publicly leaked.
According to Symantec, one of the tools used by Buckeye was DoublePulsar, a backdoor implant that allows attackers to stealthily collect information and run malicious code on a target’s machine. DoublePulsar was used in conjunction with another tool, which Symantec calls Trojan.Bemstour, that took advantage of various Microsoft Windows vulnerabilities in order to secretly siphon information off targeted computers.
The Trojan.Bemstour exploit allowed attackers to remotely manipulate a machine’s kernel, the core part of a computer’s operating system that manages resources such as memory. When put into action, the exploit can pull sensitive information from a targeted machine or can be combined in conjunction with other vulnerabilities to take control of the kernel.
One of the vulnerabilities was patched in March 2017. The other was reported by Symantec to Microsoft in September 2018 and patched in March 2019.
Buckeye used the tools in attacks that hit telecommunications companies, firms dedicated to scientific research and education institutions from March 2016 to the middle of 2017, according to Symantec. The group hit organizations in Belgium, Hong Kong, Luxembourg, the Philippines and Vietnam.
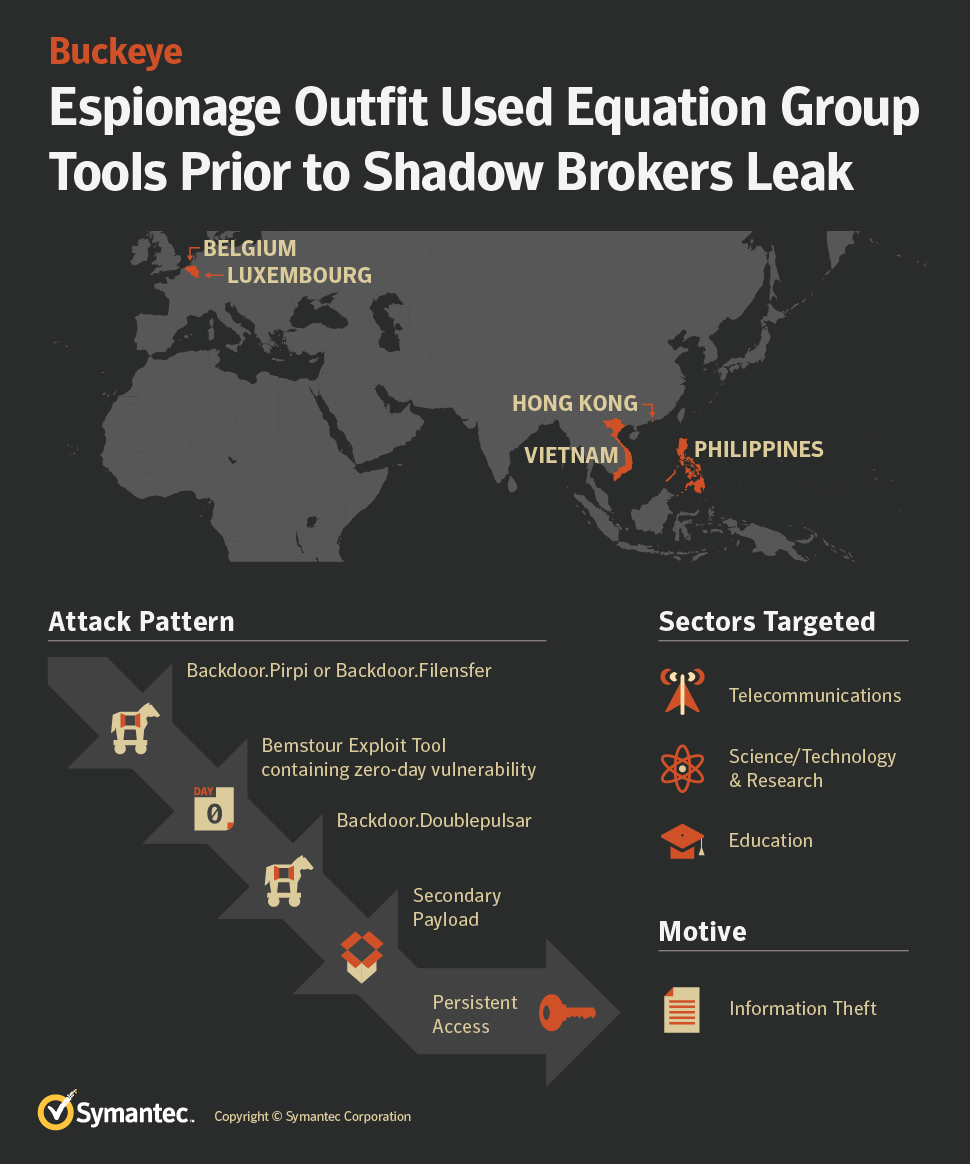
An inforgraphic that shows the timeline of Buckeye’s use of NSA tools. (Symantec)
DoublePulsar has been linked to the Equation Group, an elite hacking team that the cybersecurity community has long attached to the NSA. One of the vulnerabilities leveraged by Trojan.Bemstour was also used by two other Equation Group exploits — EternalRomance and EternalSynergy — that were included in the Shadow Brokers’ April 2017 dump.
“How Buckeye obtained Equation Group tools at least a year prior to the Shadow Brokers leak remains unknown,” a blog post from Symantec reads.
The company does state there’s a possibility that Buckeye may have developed its own version of the tools after possibly observing an Equation Group attack and reverse-engineering the malware it caught by monitoring network traffic.
Buckeye — also known as APT3, Boyusec or Gothic Panda — has not been active since 2017, researchers said. Symantec found, however, that development of Trojan.Bemstour continued into 2019. The company said the most recent version of the exploit was complied on March 23 — 11 days after Microsoft patched the last associated vulnerability. It is unclear who continued to use the tools in 2018 and 2019, according to Symantec.
Three alleged members of Buckeye were indicted in the U.S. in November 2017. At the time of the indictments, numerous cybersecurity researchers told CyberScoop there was a high probability that APT3 was linked with China’s Ministry of State Security (MSS). Serving as China’s civilian intelligence agency, analysts say the MSS has become Beijing’s preferred arm for conducting economic espionage.
The research comes days after the Department of Defense issued a report stating that China’s cyber-theft and cyber-espionage operations are accelerating to the point that they can “degrade core U.S. operational and technological advantages.”
“The threat and the challenge is persistent. The Chinese remain very aggressive in their use of cyber,” Assistant Secretary of Defense Randall G. Schriver said during a press briefing on the report.
The NSA did not return a request for comment.






