Apple thwarts Safari-based ransomware scheme with iOS 10.3 update

Apple’s newly released update to its mobile operating system fixes a crucial software bug in the Safari web browser that previously allowed scammers to spam users with JavaScript pop-ups, according to mobile security company Lookout.
An attacker could execute a ransomware-style attack in past versions of iOS by abusing the pop-up dialogs in Safari, thereby locking victims out from using their web browser until a payment is received. In this scenario, victims would be typically redirected to a malicious website, which is designed to appear like it belongs to a faux law enforcement agency, where a payment — in the form of iTunes gift cards — is demanded for a fake “fine.”
iOS 10.3 protects against this attack by making Safari run “on a per-tab basis so that if one tab is misbehaving, the user can close it out and/or move to another one,” a blog post by Lookout researchers Andrew Blaich and Jeremy Richards explains.
The flaw in Safari was discovered by Lookout after an iPhone owner, while using Safari, was redirected to pay-police[.]com. Other domains registered by the scammers include networksafetydept@usa[.]com and cybercrimegov@europe[.]com.
The ransomware targets individuals who download music online or visit pornography websites.
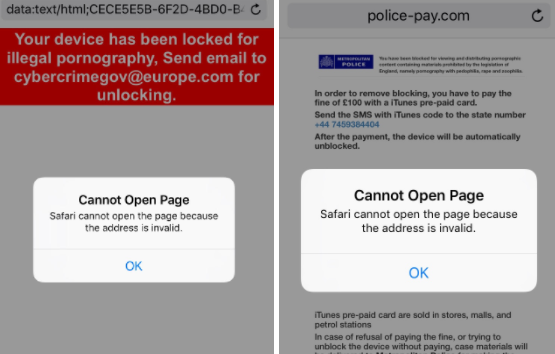
Image via LookOut
Typically victims lose control after being redirected from a website they were visiting to pay-police[dot]com domain, where an infinite loop of dialogue boxes quickly appear with the message “Cannot Open Page.” Pressing “Ok” on the dialogue box only resets the alert. It’s impossible to navigate to a different browser tab after the first box appears.
After a period of time the victim is prompted with a payment request and other warnings.
“Lookout found this attack in the wild last month, along with several related websites used in the campaign, discovered the root cause, and shared the details with Apple. As part of the iOS 10.3 patch released today, Apple closed the attack vector by changing how mobile Safari handles website pop-up dialogs, making them per-tab rather than taking over the entire app,” Blaich and Richards wrote.
The only available fix prior to Monday’s update required that users clear their Safari cache to regain control, effectively erasing web history and other temporary internet data would help stop the scammers.
The ransomware scheme carries no exploit code. It is contained within the app sandbox of the Safari browser itself, meaning that it cannot migrate into other applications or the iPhone’s larger software framework. Researchers believed the attack, which Lookout found previously on a Russian website, was originally developed to target iOS 8 but it remained functional until iOS 10.3.