Private firm puts $500K bounty on Signal, WhatsApp zero-day vulnerabilities

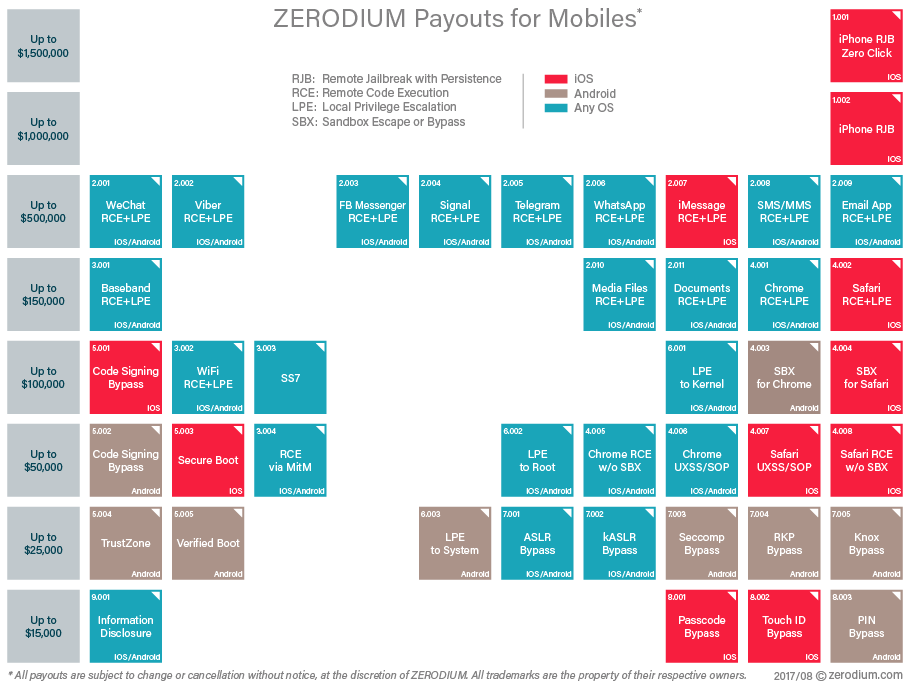
Zero-day vulnerabilities targeting popular secure messenger applications, like Signal, Telegram and WhatsApp, can fetch payments of up to $500,000 from Zerodium, a buyer and seller of zero-day research, based on a newly released list of available awards offered by the U.S. firm.
The market for zero-day vulnerabilities — an undisclosed software security hole that can be exploited by hackers — is notoriously rich and murky. Traders tend to operate away from public scrutiny for a number of reasons that make it difficult to learn about the market.
Although Zerodium isn’t known for the transparency of its business, the company’s listings for vulnerabilities provides a window into the supply and demand behind the vulnerability resale industry.
Information concerning software flaws that allow for remote code execution and privilege escalation within Signal, and other secure messenger applications, are currently worth $500,000 a piece. These applications are used by billions of people around the world including, as Zerodium founder Chaouki Bekrar notes, criminals; causing the vulnerabilities to be in potential high demand from some government clients.
The high price for zero-days impacting secure messenging applications is surpassed only by remote jailbreaks for iPhone’s iOS operating system. The high price point is widely seen as both an endorsement of the security chops of theses software products and proof of the evident high demand by clients to break into them.
“The price that Zerodium puts on a product is always an indication of the security of that product, the higher the price, the better is the security of that product,” Bekrar told CyberScoop. “The prices result from both a high demand and a small attack surface in these apps which makes the discovery and exploitation of critical bugs very challenging for security researchers.”
He added, “the high value for zero-day exploits affecting such apps comes mostly from the smaller attack surface that is available in these apps compared to other software such as web browsers or file readers, which makes the discovery and exploitation of critical vulnerabilities in these messaging apps very challenging for security researchers.”
The price of zero-day vulnerabilities for in-demand targets is rising, researchers say, as money pours into the market on the private and public sector fronts. The number of zero-day exploits found in the wild fell in 2016 for the third year in a row but as supply drops, demand rises and the price jumps upward with it.
“If [attackers] find something exploitable, there is now more value,” Symanetc’s Kevin Haley told CyberScoop.
In the past, Zerodium paid out roughly $600,000 per month for undisclosed vulnerabilities, according to a 2015 interview with Bekrar. Although he declined to give specifics, the number is now up to “millions of dollars every year,” Bekrar told CyberScoop on Wednesday.
Zerodium’s current payout chart for mobile vulnerabilities is below:
(Zerodium)
Chris Bing contributed to this report.






