Six big vendors dominate a fragmented federal cyber market, numbers show

Federal procurement of cybersecurity goods and services is highly fragmented, according to new research published this week, with more than 7,600 different companies winning U.S. government contracts during the past six years. But despite this long tail of small awards, the market space is dominated by a handful of familiar names.
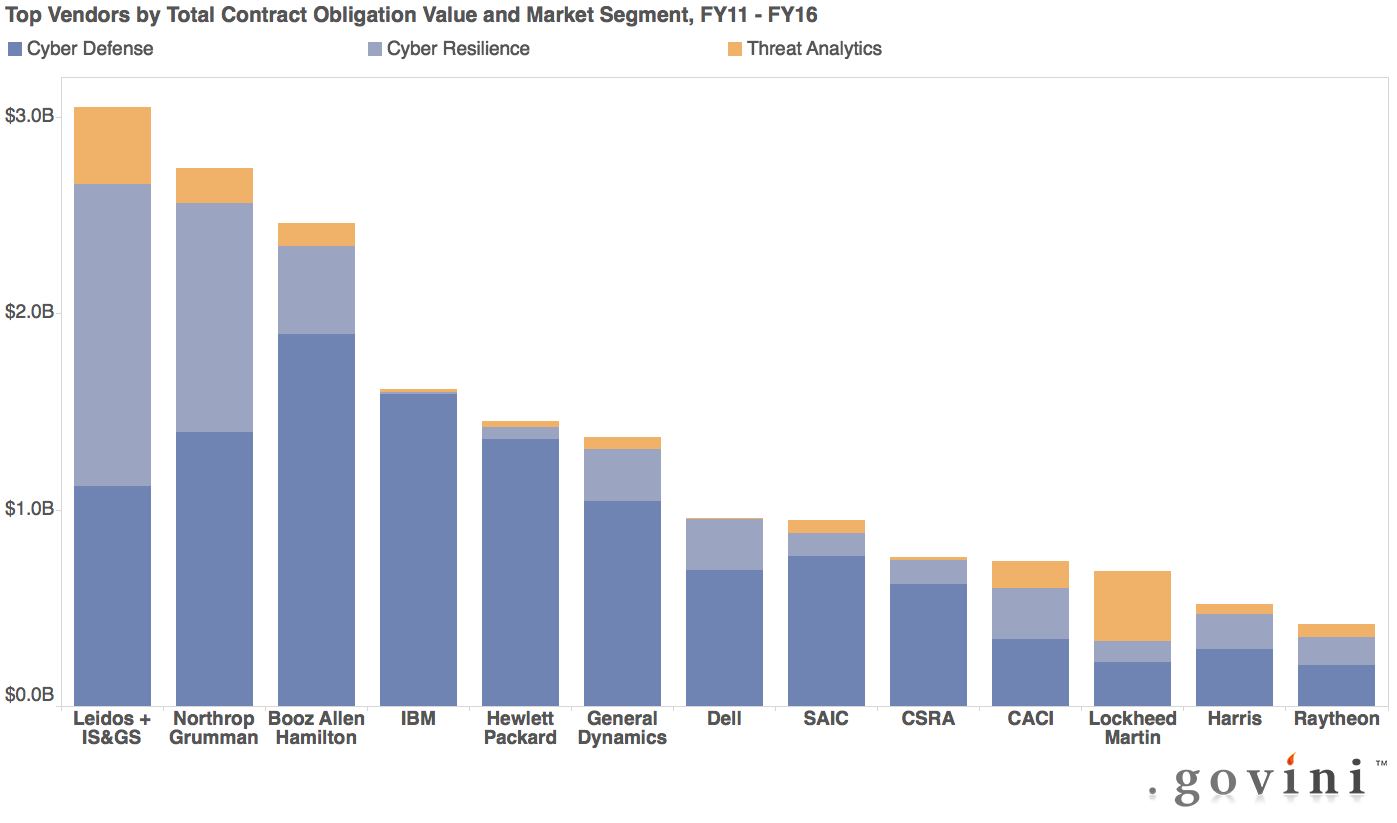
Only six contractors — Leidos, Northrup Grumman, Booz Allen Hamilton, IBM, Hewlett Packard and General Dynamics — earned a billion dollars or more in cyber contracts from the U.S. government in fiscal 2011-16, according to the new report from Govini, a consultancy that crunches procurement numbers.
A handful more — Dell, SAIC, CSRA, CACI, Lockheed Martin, Harris and Raytheon — earned hundreds of millions from the $45.9 billion obligated between 2011-2016 in three categories of federal cybersecurity spending: defense, resilience and threat analytics.
“Acquisition of cybersecurity solutions is highly fragmented now,” Arun Sankaran, Govini’s director of professional services and the report’s lead author told CyberScoop.
The report also shows that federal spending in those three categories rose significantly after 2013, from an average of $6.3 billion a year in 2011-2013, to around $9 billion a year 2014-2016.
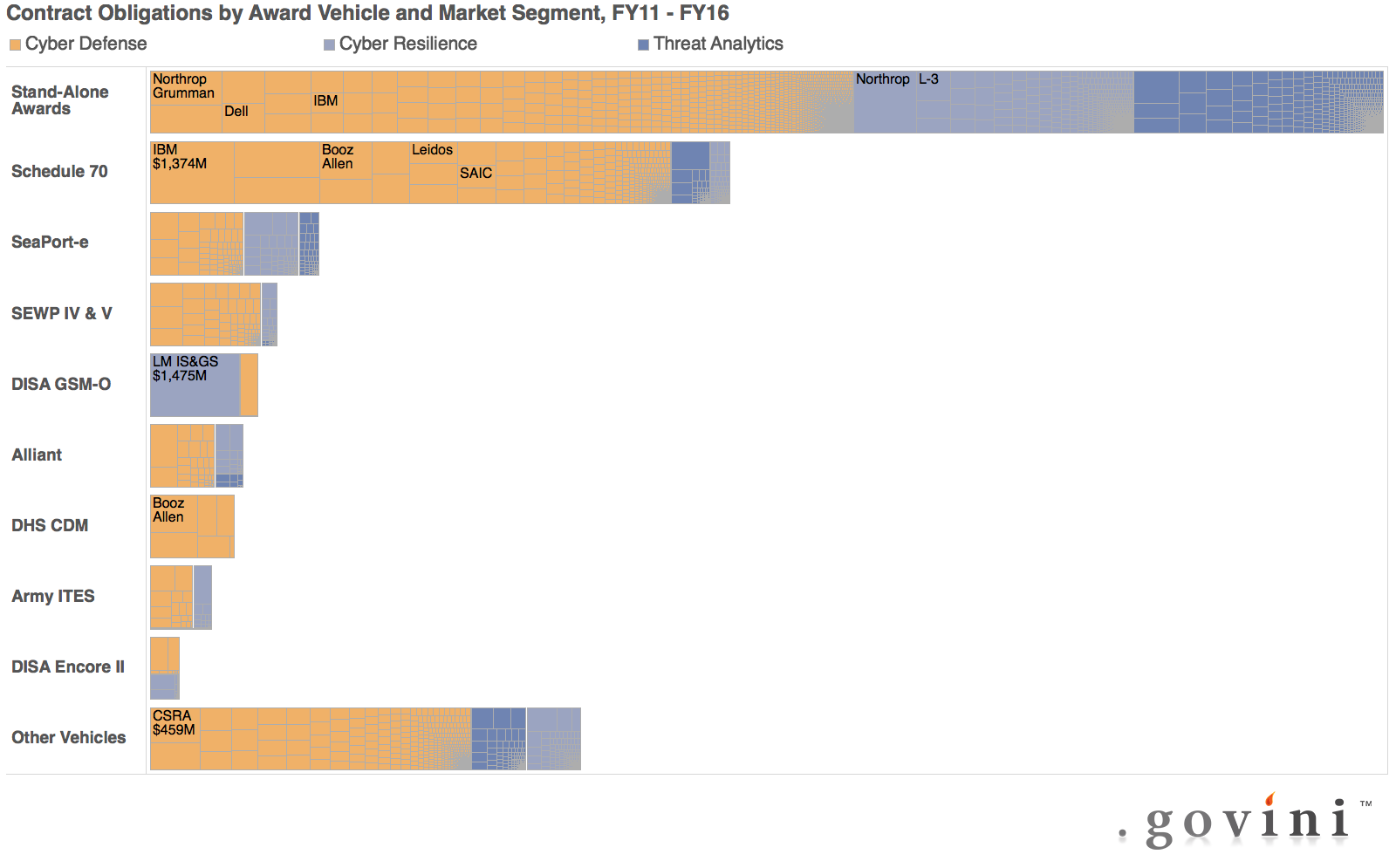
Sankaran pointed out that 42 percent of that money — $19.3 billion overall — was spent via single, stand-alone contracts, with only 58 percent going through large multi-award contract vehicles like the Department of Homeland Security’s Continuous Diagnostics and Monitoring program — which pays for the installation of cybersecurity tools on federal networks governmentwide — or the General Services Administration Schedule 70.
 The long tail of small players and the heavy reliance on stand-alone contracts are “symptomatic of the fragmented federal procurement process” for cybersecurity, Sankaran said.
The long tail of small players and the heavy reliance on stand-alone contracts are “symptomatic of the fragmented federal procurement process” for cybersecurity, Sankaran said.
The money is “peanut butter spread across this whole myriad of of contractors,” he added, meaning agencies “are not leveraging” the additional purchasing power offered by multi-award contract vehicles.
The cause of that fragmentation? Sankaran said civilian federal agencies have seen cybersecurity as an IT issue and dealt with it ad hoc, rather than as a core issue of mission effectiveness. That means “Agencies tend to cluster around their preferred providers, and they use whatever contracting mechanism is convenient.”
Partly as a result, cybersecurity is also “a services play, rather than a technology play in the federal government right now,” he said, meaning that “the big-time systems integrators who can supply a lot of bodies through contracts to agencies tend to dominate the market.”
 Also telling for Sankaran: the high proportion of cybersecurity dollars spent on “operations and maintenance” or O&M — that is, keeping existing systems running as opposed to procurement of new technology or research and development.
Also telling for Sankaran: the high proportion of cybersecurity dollars spent on “operations and maintenance” or O&M — that is, keeping existing systems running as opposed to procurement of new technology or research and development.
“That tells me … a lot of how we’re defending networks now is we’re patching them, we’re maintaining and repairing the existing infrastructure that’s out there … Not a lot of what’s being spent on cyber today is [spent on] developing the latest and greatest sophisticated technology… The bulk of the market is developing patchwork solutions for old networks through O&M,” he said.
He applauded the new administration’s apparent decision to emphasize IT modernization, shared services and enterprise-level risk management as the key to securing federal networks.
“If that gains momentum,” Sankaran predicted, “You’ll see an expansion in DHS’ role as leading efforts to make civilian government networks secure.” That in turn would lead to more larger, multi-award contract vehicles and “more consolidation of acquisition as DHS anoints certain companies.”




