Senators want spies to disclose more about secret zero-day policy

The Senate Intelligence Committee hopes to learn more about how American spies handle the disclosure of software vulnerabilities continuously discovered by federal agencies and occasionally used as weak points to hack into computer networks, according to the recently released 2018 Intelligence Authorization Act. While the law calls for greater transparency, former senior U.S. officials say it begs the wrong questions.
The specific provision, which is just one part of the Senate committee’s annual legislative agenda, comes in the aftermath of multiple leaks of classified information; providing in some cases the computer code behind a toolbox of outdated NSA and CIA hacking capabilities. These exposures have already led to the adoption of several different, U.S. government-linked hacking tools by cyber criminals and foreign spy powers. The proliferation of this code was responsible for a recent, global outbreak of ransomware that subsequently caused millions of dollars in business losses.
The central framework that guides each agency’s decision of whether or not to inform a technology vendor of a discovered software vulnerability is guided by a process known as the Vulnerabilities Equities Process, or VEP. Although there’s risk involved, there are cases when a spy agency may choose to keep a vulnerability hidden — thereby allowing for a software flaw to continue — because it allows them to collect intelligence on a specific target. These incidents are voluntarily submitted into the VEP as part of a formal process that includes a review board consisting of senior government officials from multiple federal agencies, like the Commerce Department and FBI.
While the VEP is an increasingly important rubric used to review the impact of certain digital espionage operations, the framework remains largely shrouded in secrecy. For example, the exact guidelines established by the VEP are unclear to the public as are the conversations between affected parties and the government.
Today, the intelligence community works in tandem with the Homeland Security Department to notify companies about software flaws processed through the VEP. For the most part, Congress is unconnected and uninformed on a majority of what goes into these considerations. But if the Senate’s intel authorization bill eventually passes then it would immediately change lawmakers’ understanding of the VEP by compelling spy agencies to provide reports about all vulnerabilities entered into the secretive process.
The 2018 Intelligence Authorization Act was quietly introduced last week. Emptywheel.net was the first to highlight the VEP-specific language in the bill.
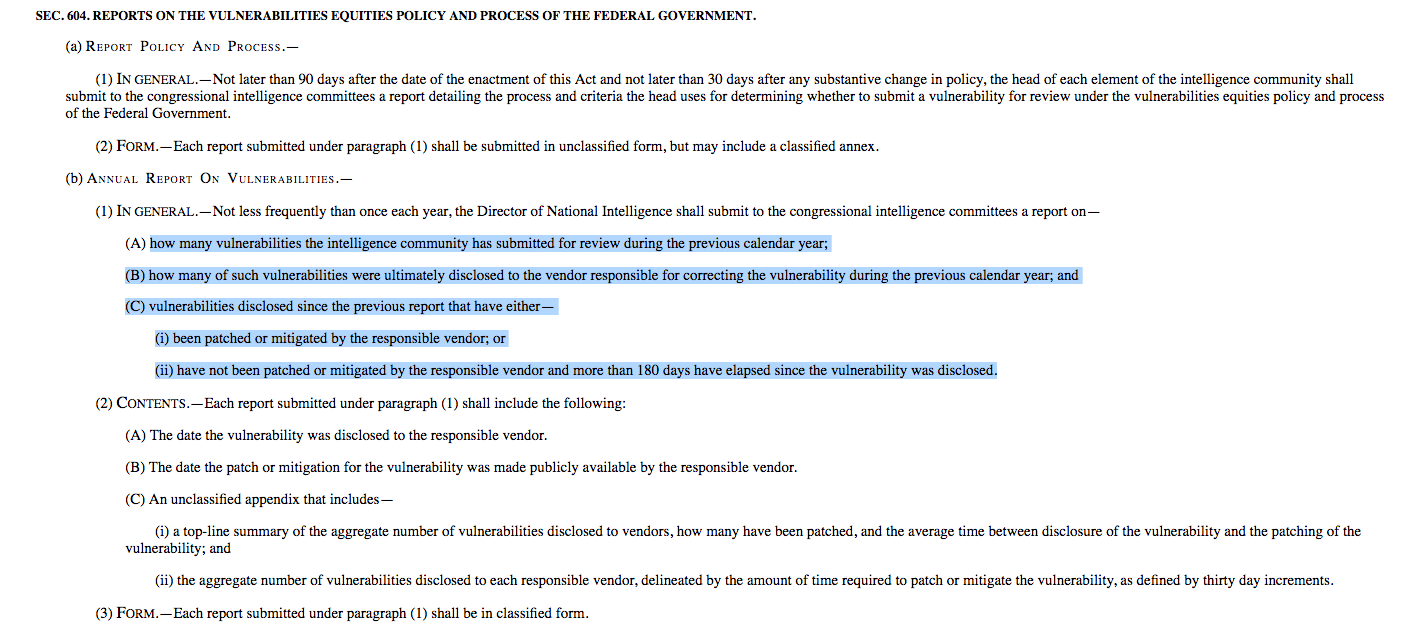
Section 604 of the Authorization Act requires the heads of the intelligence community to submit the congressional intelligence committees with an annual report detailing the VEP process and specific criteria employed by each agency. Based on how the requirements are currently written, the classified reports would contain highly sensitive material that must include not just a thorough explanation of the procedure itself but also the specific vulnerabilities entered into the process, companies affected, dates when disclosures occurred, a listing of the vulnerabilities eventually patched by the private sector and which software flaws were communicated but not fixed.
Screenshot of VEP provisions under 2018 Intel Auth bill
Experts say that if such a classified report were to leak it would be highly damaging to the government’s already strained relationship with Silicon Valley. In addition, the legislation misses the mark on some other points, according to Ari Schwartz, a former senior director for cybersecurity on the National Security Council at the White House.
“Congress would be better served focusing on the part of this legislation related to greater transparency of the aggregate number of vulnerabilities — how many were given to vendors and how many are kept and which agencies are involved,” said Schwartz, who is now a managing director of cybersecurity services with D.C. law firm Venable LLP. “This would provide much greater insight into how the VEP is working than what Congress has today. Focussing on individual vulnerabilities and/or whether they have been patched risks taking the IC away from its mission and calls into question Congress’ ability to protect this sensitive information.”
Beyond “The Gang of Eight,” the intelligence community holds longstanding reservations about Congress’ ability to protect sensitive material once it leaves a classified environment and arrives on Capitol Hill, insiders say.
Michael Sulmeyer, the former director of plans and operations for cyber policy in the Office of the Secretary of Defense, similarly described that while the effort may be a positive sign because Congress is now interested in the VEP, the bill falls short. He also questioned the underlying value of the VEP.
“I’m not a huge fan of the VEP,” said Sulmeyer
“You have to wonder, at the end of the day, how much security are we really getting in exchange for all the pain that goes into implementing this process? Is this one-by-one approach an effective way to improve defenses on a meaningful scale? That said, I am pleased the Intelligence Committee wants to learn more,” Sulmeyer said. “I might have posed an additional question for the intelligence community to discuss in the requested report: do we have any indication about the extent to which a patch was applied? An answer could inform if we risk neutralizing legitimate government tools in exchange for little or no defensive advantage.”
Privacy advocates told CyberScoop they were surprised by how far the bill went in requesting sensitive information from the intelligence community.
The Authorization Act was introduced on August 18. As is tradition, the Office of the Director of National Intelligence will provide Congress with a “views letter addressing specific provisions in the legislation,” an ODNI spokesperson told The Daily Beast. The next step for the legislation is for it to be presented for a Senate floor vote, before heading to the House and then President’s desk for signature.





