A zombie game with 50,000 Play Store downloads was pulling sensitive data from Gmail

An Android game with more than 50,000 downloads from the Google Play Store attempted to collect scores of data from users’ Google accounts — including Gmail usernames and passwords — alongside other dubious behaviors, according to forthcoming research provided exclusively to CyberScoop.
Researchers from the mobile security company Wandera identified the app, called “Scary Granny ZOMBY Mod: The Horror Game 2019,” as a malicious program that launched persistent full-screen advertisements on users’ phones, and asks some to enter their Google credentials. Google removed the app from the Play Store following the publication of an earlier version of this story.
Upon receiving a victim’s username and password, the program automatically logged into users’ Google accounts and collected personal data for a purpose that was not immediately clear, according to Michael Covington, vice president of product at Wandera.
“There is no doubt in my mind that this app is malicious and puts private user data at risk,” he said before the program was scrubbed from the Play Store. “It’s logging into the profile section of your Gmail and going through tab by tab and taking screenshots of your personal information. It’s taking all of that data and sending it somewhere.”
The app did not appear to act in malicious ways on newer phones, but did seek the credentials of people who accessed it on Android devices running operating systems released prior to Oreo, Wandera found. This research is scheduled to be published in full Friday.
“Scary Granny ZOMBY Mod: The Horror Game 2019” appeared to be a ripoff of “Granny,” a similar puzzle game with more than 100 million downloads.
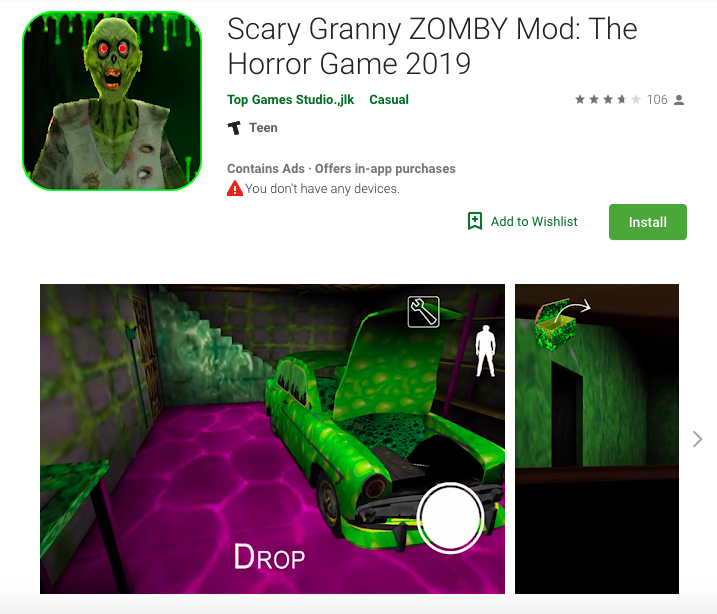
A screenshot of the now-defunct Google Play Store page listing “Scary Granny ZOMBY.”
It was only the latest example of a Play Store app that seemed legitimate but in fact leveraged its popularity to seek data in ways downloaders couldn’t have predicted. Researchers from Check Point and Avast in recent weeks have revealed that dozens of programs that masquerade as fitness, photo editing or other lifestyle apps that actually contain adware. Last month, BuzzFeed News revealed how one app that appeared to download YouTube videos actually subscribed people to paid services in secret.
Wandera reported its findings to Play Store security administrators earlier this week.
It’s not clear who was behind the app. The developer was listed only as Top Games Studio.,jlk, and “Scary Granny” was the only app affiliated with that name on the Play Store. The developer’s site directed to an unregistered domain, and the email address listed on the Play Store page appeared to be a fake.
How it worked
Players using the game appeared as a non-zombie trying to escape members of the living dead while earning points along the way. But the real challenge was getting to the game at all.
Upon loading the app, it broadcast full-screen ads and asks affected users to pay 18 pounds ($22) to access the game. While it was possible to navigate around the fee, the screen also automatically populated with information from a user’s mobile wallet when payment was requested.
Then, for a fraction of users, the app displayed a “Sing In” page meant to look like a Google “Sign In” portal. It remains unclear why the “Sing In” page was activated for some users and not others. Users who did meet the elusive criteria were asked repeatedly to enter their information until they abide by that request.
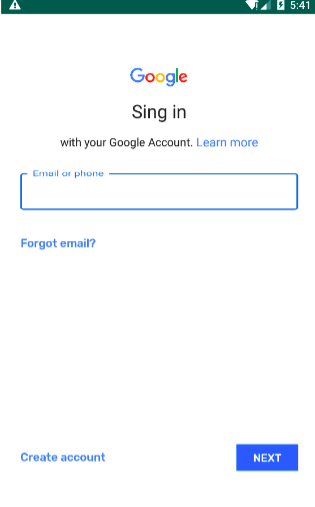
A screenshot of the phishing page that appears for some “Scary Granny ZOMBY” players (Wandera).
It also was not immediately clear how many of the more than 50,000 users who had the app have entered their information into the page.
“Let’s say a third of those people fell victim to that scheme — that’s still thousands of people,” Covington said.
A previous iteration of “Scary Granny” frequently would crash after users logged in, though an updated version made available on June 11 in the Play Store seemed to function without interruption.
“I think what we’re seeing is an evolution of an attack tool that started as proof-of-concept that’s now been refined,” he said before the app was removed.
While the gameplay was underway, the app surreptitiously connected to a legitimate Google server, where it used the stolen credentials to log in to a user’s Gmail account to collect information including their recovery email address, recovery phone numbers, birth date, verification codes, as well as some cookies and tokens. The credentials were sent through an unencrypted connection then exfiltrated somewhere, Wandera found.
“I haven’t been able to come up with any other [motive] than to steal credentials, but it’s doing this in a really elegant way,” Covington added.
Unchecked capabilities
The app also contained one file flagged by Virus Total that could have given “Scary Granny” more permission than users realized. Specifically, the file was been identified as containing the hacking tool Trojan.AndroidOS.Agent, a form of adware that seeks root privilege to the operating system. Whether the app was abusing that access remains unclear (Wandera said it didn’t notice that happening).
Meanwhile, the app also appeared to be facilitating malicious advertisements. During one Wandera test, an ad triggered a network redirection that was blocked by Google’s Safe Browsing service, researchers said. That means at least one malicious ad, perhaps to another phishing service, that came up during gameplay was blocked by Google.
Finally, “Scary Granny” was able to disguise its activity from users who might actively try to determine if it was misbehaving. The app was capable of activating itself after a phone reboots, and demonstrated that it could serve full-screen ads without appearing in a device’s list of running applications, Wandera found. It’s unusual for apps without administrative priveleges on a phone to launch themselves without any user interaction.
The behavior seemed to be a clear violation of Google’s rules around Privacy, Security and Deception, which require developers to be transparent in ways they collect and use data. A link to the privacy policy on the “Scary Granny” app page leads to a travel blog.
But users certainly were aware of the game. “Scary Granny” held a 3.7 rating on the Play Store based on 27 reviews, with opinions split mostly between one and five stars. Most of the content in the five-star reviews appeared to be the result of bot traffic, with typical reviews containing descriptions like “granny zombie great game,” “granny zombie mod” and “Very good and Horrrrrror [sic] game. I liked it.”
The one-star reviews were much less forgiving. The language in some of those also was nonsense, but a small handful appeared to be from real people. “Had to buy a new phone. Do not download,” said another with 62 upvotes.
Another reviewer put it more succinctly: “Do not get this.”
UPDATE, June 25, 3:30pm EDT: This story has been updated to reflect that Google removed the “Scary Granny ZOMBY Mod: The Horror Game 2019” app following publication of an initial version of this story. The company did not immediately respond to followup questions about the game or its existence on the Play Store.





