Russian hackers reportedly breached telecom network months before attack

The Russian hackers that targeted Ukraine’s largest telecommunications provider in December, knocking out mobile phone and home internet service to roughly 24 million people, were in the company’s networks for months before wiping “almost everything,” a senior Ukrainian government official said in an interview published Thursday.
Illia Vitiuk, the head of the Security Service of Ukraine’s (SBU) cybersecurity department, told Reuters in late December that the attack was likely the work of the potent Russian military intelligence hacking unit known as “Sandworm,” and that the hackers had accessed Kyivstar’s network since May 2023 but perhaps even earlier.
Vitiuk also said during the interview, which was published Thursday, that the attack on the telecommunications firm caused “disastrous” destruction, wiping “almost everything,” including thousands of virtual servers and PCs belonging to the firm.
Vitiuk told Reuters that the attackers “would have been able to steal personal information, understand the locations of phones, intercept SMS-messages and perhaps steal Telegram accounts with the level of access they gained.”
Kyivstar said in a statement provided to CyberScoop on Thursday that it “does not confirm the information” regarding the length of time that the attackers had access to its networks. “The official investigation into the cyberattack on the Kyivstar network … is still ongoing and various versions are being considered, none of which is yet final,” the company said in the statement, adding that it has seen no evidence of any “leakage of personal data.”
The company did not respond to a follow-up question regarding the discrepancy between its version of events and Vitiuk’s.
The company said in a Dec. 13 message posted to Facebook that “the rumors about the destruction of our ‘computers and servers'” were “fake,” adding that subscriber data was safe.
Vitiuk said in a statement posted to the SBU’s website Thursday that the SBU helped fend off additional attacks against Kyivstar: “The enemy was hoping to strike several times in a row to keep people disconnected for as long as possible. In this case, other operators might not have been able to withstand the prolonged overload of their networks.”
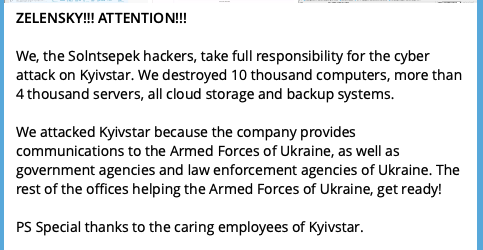
The attack, which took place on Dec. 12, knocked out service for the company’s customers for at least a day, and sometimes longer. A group calling itself “Solntsepek” took credit for the attack, and experts noted that the persona had previously claimed credit for attacks linked to Sandworm.
In a message directed to Ukrainian President Volodymyr Zelensky, the persona claimed to have inflicted widespread damage on Kyivstar and said the attack was the result of the company’s work supporting the Ukrainian military and law enforcement agencies.
Vitiuk told Reuters that the attack did not have a major impact on Ukrainian military operations.
Sandworm is among the Russian military’s most enduring and effective hacking units, and is known for information operations as well as multiple destructive attacks on Ukrainian critical infrastructure.
“This attack is a big message, a big warning, not only to Ukraine, but for the whole Western world to understand that no one is actually untouchable,” Vitiuk told Reuters.





