GitHub disables pro-Russian hacktivist DDoS pages

GitHub on Tuesday disabled accounts on the platform belonging to a pro-Russian hacktivist group linked to attacks on entities in NATO countries, including efforts to disrupt the websites of Denmark’s central bank and other financial institutions in the country, GitHub confirmed to CyberScoop.
The group, NoName057(16), used the software development platform to host its distributed denial of service (DDoS) tool website and code used in its attacks, researchers with SentinelOne said Thursday. The researchers reported the activity to Github, prompting the company to disable the group’s accounts earlier this week.
“We disabled the accounts in accordance with GitHub’s Acceptable Use Policies, which prohibit posting content that directly supports unlawful active attacks or uses GitHub as a means to deliver malicious executables,” a company spokesperson told CyberScoop.
While more obscure than other pro-Russian hacktivist groups, such as KillNet and Xaknet, pro-Russian hacking groups the U.S. government has described as threats to U.S. critical infrastructure, NoName057(16) distributes cryptocurrency to its top DDoS contributors. And while its DDoS attacks have been generally short-lived, the financial incentives offered by the group encourage “people to contribute more technical resources for a more powerful attack,” SentinelOne’s researchers note.
The group has shown a willingness to target a wide range of organizations across NATO, said Tom Hegel, a senior threat researcher with SentinelOne’s SentinelLabs. By offering a financial incentive, “individuals contributing to the attacks may have financial gain in mind, rather than politics—meaning there is a larger pool of potential contributors,” Hegel said.
While it is important to not overstate the impact of a fairly technically unsophisticated group like NoName057(16), the collective illustrates how Russia’s invasion of Ukraine has inspired hackers to act as its proxies.
“What this group represents is an increased interest in volunteer-fueled attacks, while now adding payments to its most impactful contributors,” Hegel and fellow researcher Aleksandar Milenkoski write in an analysis published Thursday. “We expect such groups to continue to thrive in today’s highly contentious political climate.”
NoName057(16) initially targeted Ukrainian news sites starting in March of this year but shifted to attacking various entities in NATO countries, in a bid to silence “what the group deems to be anti-Russian,” according to Hegel and Milenkoski.
The group tends to shift targets depending on current events, the researchers note. In December, for instance, the group disrupted websites in Poland shortly after lawmakers there recognized Russia as a state sponsor of terrorism. In January, the group targeted the cargo and shipping sectors in Lithuania, before turning to targets in Denmark.
The group relies on Telegram to communicate with its followers, where, on Wednesday, the group informed the more than 18,000 subscribers to its Russian-language channel (and the 300-some subscribers to its parallel English-language channel) that it had targeted the website belonging to a candidate in the upcoming Czech presidential election.
Attacking in retaliation for the Czech Republic’s role in training Ukrainian soldiers, NoName057(16) claimed to have taken down a website belonging to presidential candidate Tomas Zima.
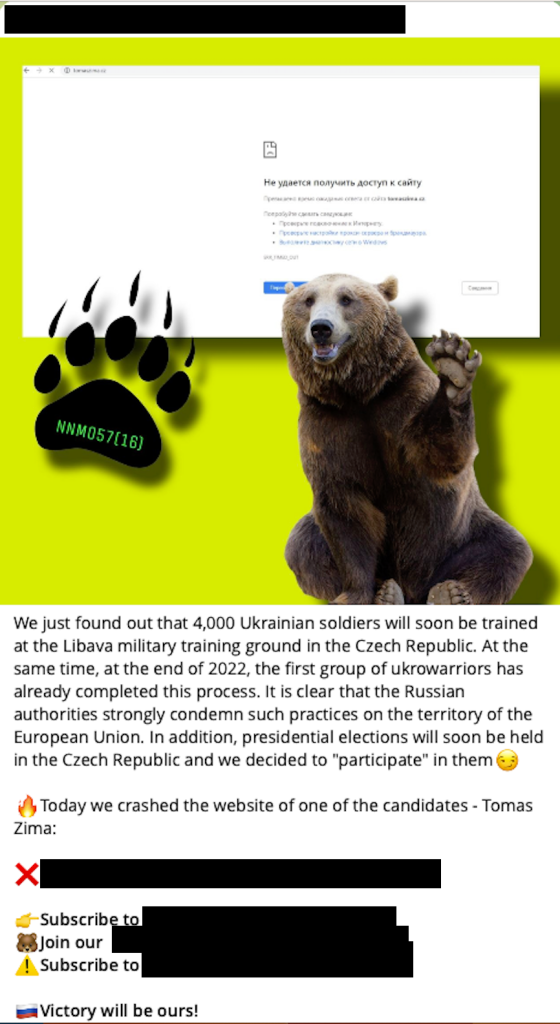
Commands sent from NoName057(16)’s command and control server make it clear the group has attacked websites belonging to other candidates in the Czech presidential election, Hegel said, rendering some of them intermittently available over the course of Wednesday.

This story was featured in CyberScoop Special Report: War in Ukraine


