‘Bring your own device’ policies poison most networks, report says

The IT departments of many major enterprises have no effective control of their networks because of the proliferation of personal smartphones and other connected devices, according to a new survey.
Only just under half of 800 IT security professionals surveyed said they could be certain how many connected devices their colleagues bring into work, according to the Internet of Evil Things report from network security specialists Pwnie Express.
“It starts with BYOD [Bring Your Own Device],” Pwnie Express CEO Paul Paget told CyberScoop, “Then [employees] start bringing other [connected] things like Fitbits,” other Internet devices that connect via Bluetooth.
“One day, all of a sudden, IT has completely lost control of the network,” Paget said.
“These are not your devices,” said Paget. “And they talk to devices you can’t see. They live in the cesspool that’s out there, they are subject to cross-pollination” and infection on the open Internet and public Wi-Fi points.
Forty-one percent of respondents had no BYOD policy, while nearly a third of those with a policy have no way of enforcing it.
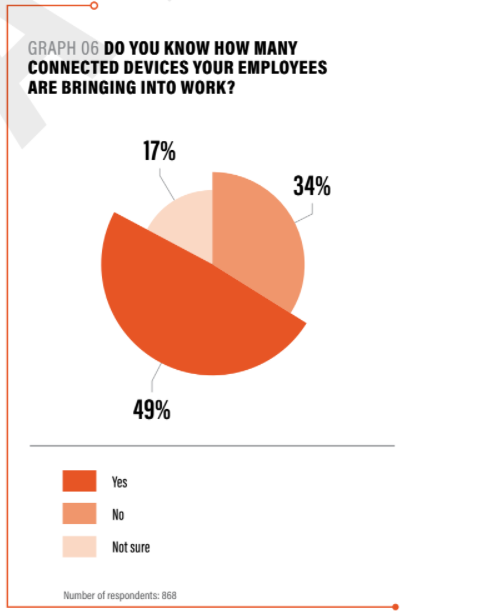
Source: Pwnie Express “Internet of Evil Things” report
Network visibility varies depending on the connection, Paget explained
“The traditional attitude of IT security is: ‘I own these devices. I patch them, I configure them, I control them.'”
But as more and more employee-owned devices enter the workplace, “The footprint of things [the IT department] controls is getting smaller and smaller,” he said.

Source: Pwnie Express “Internet of Evil Things” report
“Insider threats aren’t necessarily malicious,” said Paget, adding that “hard-working, well-meaning employees,” were bringing these connected devices into the workplace. “They’re trying to increase their productivity.”
IT security professionals need to wise up, explained Pwnie’s Jayson Str
“They need to defend the network as it really is, not as it’s depicted on their network diagram,” he said. “They need to know what devices are out there and know who they’re talking to.”



