Forget your fingerprint: New concept lets people pick their own two-factor token

Researchers at Florida International University have designed an app for Android phones that allows users to replace passwords with a photograph of an everyday object they own, like a watch, shoe or piece of jewelry.
The app, known as Pixie, is a “proof-of-concept” that shows how two-factor identification — something more than just a password — can be implemented without special hardware or biometrics. It was described by the researchers in an article in the peer-reviewed journal of the Association of Computing Machinery.
It works like this: The user takes a picture or pictures of some object they carry with them — the researchers call this object the “trinket.” These pictures form what’s called the reference image — the picture that the submitted image has to match for the user to successfully prove who they are. The user can then prove their identity and access an account by submitting another picture of the trinket.
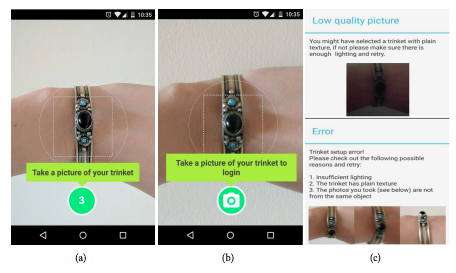
How Pixie works: The user takes pictures of some object they carry with them. These form the reference image. The user can them prove their identity and log in by submitting another picture of the object, which the authors call a “trinket.” (Source: ACM journal)
The article says the main challenge for the programmers was ensuring that the app would recognize the submitted photo if it was taken from a different angle or in different light.
They solved this a program they call ai.lock. That’s “a technique we developed to extract authentication credentials from images of arbitrary objects,” one of the authors, Bogdan Carbunar, explained to CyberScoop via email. “That is, given two images of the same object, ai.lock will extract a set of very similar values. However, given images of two different objects, ai.lock will extract sets of values that differ significantly with high probability. Pixie can use ai.lock to secure the storage and matching processes for the image passwords chosen by users.”
The researchers say on their website that Pixie is easier and quicker to use than a password, more secure than an SMS text message-based second factor, cheaper than a token-based authenticator like Yubikey and less risky and privacy-compromising than a biometric identifier like facial recognition or fingerprints.
When people use biometrics, Carbunar, “They need to use their own face or fingerprints. If an attacker gets access to these biometrics (e.g., by downloading photos posted by the victims on their Facebook page or by compromising existing fingerprint datasets, e.g., India’s Aadhaar database) the users will be vulnerable for a long time, as it is hard to change your face or fingerprints. With Pixie, changing the password is trivial, as you only have to pick a different trinket and take snapshots of it.”
The authors note that a physical token like a keystick or smartcard can cost up to several hundreds of dollars. “Contrary to other token-based authentication methods, Pixie does not require expensive, uncommon hardware to act as the second factor; that duty is assigned to the physical trinket, and the mobile device in Pixie is the primary device through which the user authenticates,” they write.
Moreover, because the device used to submit the photo only needs a camera and not a keyboard, it can be used by internet-connected wearables like smart watches or smart glasses, as well as older cellphones.
The news about Pixie was welcomed by the FIDO Alliance — an advocacy organization that promotes an open, secure standard for two-factor authentication. Most of the common token technologies use FIDO standards, and so could Pixie, Adam Powers, the alliance’s technical director told CyberScoop via email.
“Pixie is another example of an innovative user-verification method that could be used in a FIDO-compliant manner, following a pattern set by many biometric vendors who are plugging their solution into the FIDO protocol,” he said, adding that doing so allowed them to take advantage an already “deployed base of FIDO Certified servers.”
But to make Pixie FIDO-compliant on privacy, it would have to ensure it used “on device” matching — meaning that the authentication took place on the mobile device controlled by the user, not on a server or cloud setup controlled by the Pixie provider.
Powers said the on-device requirement was introduced for “several reasons: Helping ensure FIDO credentials are not vulnerable to scalable attacks such as spoofing or replay attacks following a credential data breach, both vulnerabilities that have plagued passwords.”
An important problem the Florida researchers admit they haven’t solved is what to do about users using ubiquitous objects — think a Coke can, for example. “We assume that users will choose common objects that make for weak passwords,” acknowledged Carbunar. While the app won’t let users submit “low quality and inconsistent images,” he went on, the designers expect that “in a real life use of Pixie, we would need to design filters that don’t allow users to choose common objects [either].
“However, this may impact the usability of Pixie, hence the need for further investigations,” he concluded.
One way around that issue would be to use “location-based authentication, where the user chooses as password an image of a unique scene at a frequented location (office, home, coffee shop), such as a section of book shelf, painting [or] desk clutter,” Carbunar said.
He added that the researchers had open-sourced the Pixie code through GitHub and had no plans to market it commercially.





