North Korea’s ‘state-run syndicate’ looks at cyber operations as a survival mechanism

Over the past few years, cybersecurity experts have increasingly said that nation-state operatives and cybercriminals often blur the boundaries between geopolitical and financial motivations. A new report released Wednesday shows how North Korea has flipped that idea on its head.
North Korea has silently forged a global cyber operation that experts now liken to a mafia syndicate, with tactics and organization far removed from other nation-state actors, according to a comprehensive new report released by DTEX Systems.
The study — based on years of investigations, technical analysis, and work with other open-source intelligence analysts — pulls back the curtain on a highly adaptive regime that has built its cyber capabilities on a survivalist, profit-driven approach. It reveals a hierarchy blending criminality, espionage, and front-line IT work, coordinated by an authoritarian government that rewards loyalty and secrecy while punishing failure.
Awareness of North Korea’s goals has risen in the past year as many cybersecurity companies have uncovered the depths of the scheme. Mandiant Consulting CTO Charles Carmakal told an audience at the 2025 RSAC Conference that North Korean nationals had attempted to obtain a job at every Fortune 500 company, with “hundreds” successfully finding remote work. The Department of Justice and U.S. Treasury have respectively issued indictments and sanctioned people and entities allegedly involved in North Korea’s effort to take advantage of the link between remote work and specialized technical professionals.
While DTEX’s report has a wealth of technical information, it also sheds light on the country’s cyber hierarchy, its covert talent pipeline, and the motivations that have driven members of the country’s population to enlist in the scheme. It lists details on North Korea’s “Research Center 227,” North Korea’s AI-driven cyber warfare unit, as well as hundreds of email addresses that operatives have used to obtain employment.
“This is less a typical state actor and more akin to a globally dispersed, mafia-style network, where motivations are driven not just by political power, but by a survival mentality rooted in deep economic hardship and familial obligations,” said Michael Barnhart, DTEX principal i3 insider risk investigator and lead author of the report. “Our goal is to expose the human and organizational factors critical to anticipating their next move.”
Two actors highlighted in the report include the personas “Naoki Murano” and “Jenson Collins,” who researchers say have worked in areas like Laos and Russia, and are linked to Chinyong IT Cooperation Company, an outfit that has been on the U.S. sanctions list since 2023. Murano, in particular, has been directly connected with the $6 million heist targeting DeltaPrime, a cryptocurrency platform.
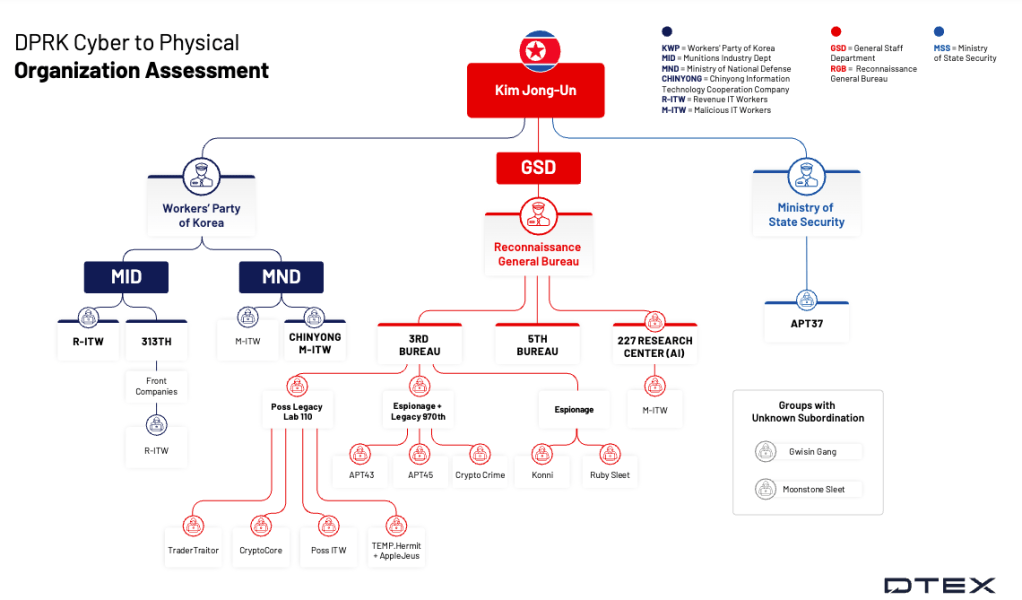
DTEX frames those personas as an example of how North Korea has used false identities to cover for a sophisticated — and often rigid — organizational structure. The report details real administrative listings of North Korean IT workers, working for different arms of the North Korean government: the 313th General Bureau, which is part of the country’s Ministry of Munitions Industry (MID), North Korea’s Department of Education, and the Reconnaissance General Bureau (RGB), the country’s primary intelligence service.
Beneath these layers of organization lies a well-defined management hierarchy that mirrors elements of both a state bureaucracy and a criminal syndicate. Many of the original members from other North Korean hacking groups, such as Lazarus Group, have risen through the ranks to become managers and group leaders, responsible for training, overseeing, and deploying new cohorts of cyber operatives. New operatives move between “traditional” APT hacking groups, freelance IT work, and managerial or advisory roles as needed by the regime’s shifting priorities.
Knowledge and techniques are shared both formally and through familial or school-based networks. The internal competition for favor, resources, and advancement is intense, and advancement often depends as much on family or political connections as technical skill. This carefully orchestrated career and management system ensures that even as operatives rotate or change specialties, the regime retains institutional memory and operational continuity in its cyber campaigns.
Barnhart told CyberScoop that while this grand scheme run by North Korea may mirror the organizational prowess of more developed countries, the commitment to standing up a slice of society dedicated to cybercrime is unlike anything experts have ever seen.
“It does on the surface resemble how a cyber program would support any nation-state element. That societal part I think is key because seeing that same structure and how DPRK specifically uses it is the unique part,” he said. “Things like the shift in the model where money flows upwards versus downwards wouldn’t appear on an organizational chart but may be one of the oddest frames for a government. Not just from this lens but looking back at other efforts such as the fake pharmaceuticals from the 90s and other physical schemes they have run in the past to generate revenue. This technological angle they’re playing in the modern tech world is just easier than [North Korea’s past] historic efforts.”
The regime is also trying to keep its talent on the cutting edge through the establishment of Research Center 227. Unlike prior North Korean cyber units, this center, staffed by 90 people, operates 24/7 and supports not only ongoing cyberattacks but also the rapid implementation of intelligence gathered by hacking groups overseas. The report says the center focuses on AI-powered tools, from generating realistic phishing documents and fake identities to developing highly automated exploits for a wide range of the country’s targets.
Research Center 227 also signals a broader shift in the regime’s thinking: recognizing the need for domestic AI capability amid fears that global sanctions could one day cut Pyongyang off from foreign technology. The center’s rapid development coincides with the public launch of AI-equipped suicide drones and increasing integration of AI in non-cyber operations, providing North Korea with new avenues to threaten adversaries.
Even with the heightened scrutiny of the past year, DTEX’s investigation found traditional law enforcement and corporate vetting often falls short in finding these operatives; many companies do not realize they have North Koreans on staff or on contract.
The company also urged security leaders to rethink everything from hiring practices and remote onboarding to technical threat detection. DTEX says beyond technical measures, behavioral red flags are disconnected digital communication, anti-screen-locking software, and suspiciously long work hours.
“Every business leader and security professional needs to recognize the risks of accommodating remote workers,” said Kevin Mandia, founder of Mandiant and a member of DTEX’s advisory board. “To empower companies to trust their remote resources is paramount — especially with North Korea leveraging the opportunity to fund its weapons program.”
You can read the full report on DTEX’s website.






