New DHS Russian hacking report was designed for RSA crowds
The Homeland Security Department quietly released a second technical report on Friday about Russian hacking, adding significant detail to a Dec. 29 document that private-sector security experts had criticized for lacking actionable information.
“We know this new one is a significant improvement over the last one,” said John Felker, Director of the National Cybersecurity and Communications Integration Center, of the new report released Feb. 10. “There’s a lot more guts in there that cyber defenders can actually use. So we wanted to get it out so people could ask us questions here, at RSA.”

DHS’ new report
Titled “Enhanced Analysis of GRIZZLY STEPPE Activity,” the newly published 119-page DHS report provides insight into the hacking tools, techniques and processes deployed by APT28 and APT29 — two hacking groups with reported ties to Russia’s Federal Security Service, or FSB, and military intelligence service unit, GRU.
In order to publish the enhanced report, DHS completed a lengthy equities review process that ended last week and involved multiple U.S. intelligence and law enforcement, explained Felker. “When you have ongoing law enforcement investigation or an ongoing intelligence operation you don’t want to piss that away,” he said.
Amid criticism of the original Grizzly Steppe analysis, the enhanced report’s delayed release also followed a multi-agency White House meeting between different intelligence community leaders. That meeting streamlined cooperation and led ultimately to Friday’s product, Felker said.
“We know there were problems with the IP list [in the first report] and so we clarified some of that … we were always going to do an update,” said Felker, “there are like 12 or 13 YARA rules in there, there’s context that surrounds the stuff we found that was suspect, so that people can understand how [APT28 and 29] are doing it, how does it impact there mission when they plug it into their system for defensive purposes. And they can be looking for that stuff too now.”
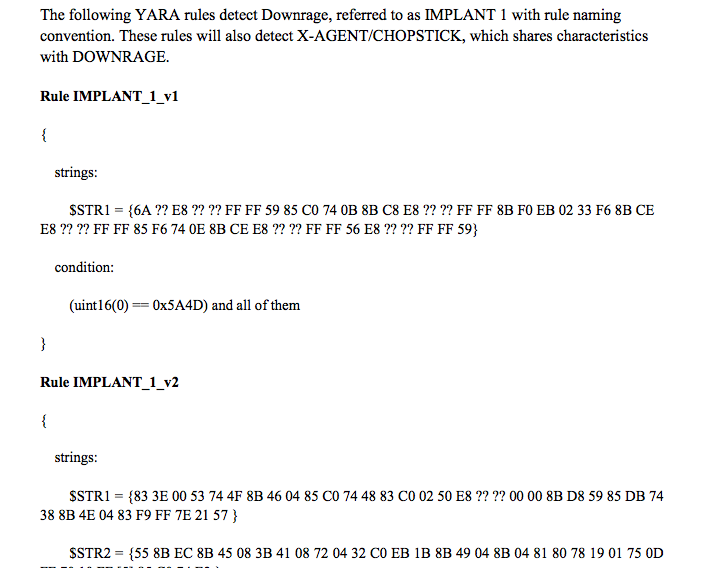
Example of YARA rule authored by DHS for network defenders
Unlike its predecessor, the newer version is largely focused on APT28 and APT29’s cyber kill chain — a term used to broadly describe the actor’s known activity organized by objective, including reconnaissance, exploitation and installation.
“This report is different from the first and should not be seen as an update but, rather a companion,” Dragos Director of Threat Intelligence Sergio Caltagirone told CyberScoop.
The original Grizzly Steppe report contained incomplete forensic data, experts previously told CyberScoop, which led some to question the document’s legitimacy and also the department’s capability to conduct such an extensive cybersecurity review. The added, newly published material, however, fills some of the blanks, said Caltagirone, and provides defensive recommendations to specifically defend against the two APT groups.
“The initial release was plagued with issues because it tried to be all things to all people mixing geopolitical topics with technical details. This report does not suffer from the same flaw targeting network defenders specifically; using a layout and language common to that community,” said Caltagirone. “The quality of this report is much higher potentially illustrating more care and learning the lessons from the first reports. Second, it does not suffer from the same overbearing editing and which was evident in the prior release.”
The team that developed both reports at DHS may look to publishing a third installation, again specific to APT28 and APT29 activity, in the future dependent on ongoing intelligence operations. But Felker said he does “not expect” additional material to come out anytime soon.
Before it was publicly published the “Enhanced Analysis of GRIZZLY STEPPE Activity” was shared with a group of European allies, multiple information sharing and analysis organizations and centers, and industry partners.






