Meet the French researcher the Shadow Brokers keep calling out

The Shadow Brokers appear to be obsessed with Matthieu Suiche.
A bevy of security researchers have spent time studying the mysterious group of hackers best known for leaking a cache of National Security Agency hacking tools. But Suiche is one of few analysts to have been called out by the Shadow Brokers multiple times, with the acknowledgement straddling the line between begrudging respect and reverent admiration.
No one, even Suiche, understands why.
A 29-year-old French security researcher and entrepreneur, Suiche is one of the foremost experts when it comes to the peculiar group. In an effort to understand why and who The Shadow Brokers — an entity still at the center of an expansive federal counterintelligence investigation — are so enamored by his work, it’s important to understand how Suiche’s background led to this point in time.
In late July, Suiche spoke at the large Vegas-based cybersecurity conference known as BlackHat about The Shadow Brokers’ saga. His presentation was apparently noticed.
“Hello Matt Suiche, The ShadowBrokers is sorry TheShadowBrokers is missing you at theblackhats or maybe not,” the group’s most recent public message posted in early October reads. “TheShadowBrokers is being sures you understanding, law enforcements, not being friendly fans of TSB. Maybe someday. Dude?”
Most BlackHat speeches are available on YouTube. The group wouldn’t have necessarily needed to attend the conference to see Suiche’s talk.
Another note by the group several weeks prior, which was also aimed at Suiche, blankly stated: “looks like such a fun guy.”
Suiche told CyberScoop he never met anyone who claimed to be affiliated with The Shadow Brokers during the week he spent in Las Vegas attending two popular security conferences, BlackHat and DefCon. He also said he was not approached by law enforcement, although he expected an encounter given his interest in the group.
Over the last year, the Shadow Brokers have made a name for themselves by releasing software exploits and other sensitive U.S. government material, announcing their leaks in a series of cryptic blog posts.
A federal investigation into how The Shadow Brokers acquired classified material is ongoing, individuals familiar with the effort previously told CyberScoop.
Former U.S. intelligence officials told CyberScoop some of the material posted by The Shadow Brokers was likely used at one point by Tailored Access Operations, the elite offensive hacking group inside the NSA.
The visible impact of the group’s actions — as well as their apparent access to the U.S. intelligence community — adds to their mystery and amplifies the question of why they’ve seemingly sought contact specifically with Suiche.
Occasionally on social media and within the group’s blog posts, The Shadow Brokers will randomly mention Suiche before then insulting a variety of U.S. companies, information security professionals and prominent politicians. Their messages are written in broken English and laced with epithets and explicit language. Common references include the U.S. intelligence community, law enforcement, White House, Russia, bitcoin, Edward Snowden and the U.S. technology sector.
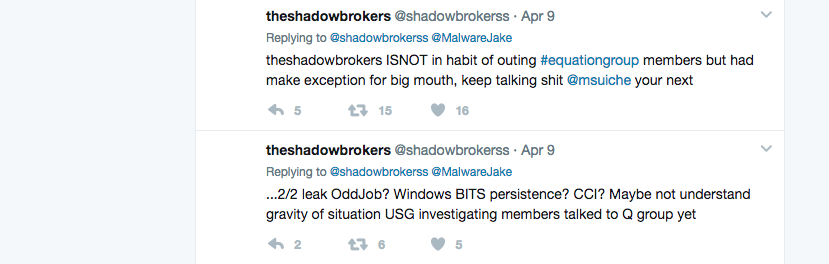
“Suiche could never be Equation Group, not U.S. born citizen,” The Shadow Brokers said in June, seemingly hoping to defend and partially clarify their prior writings regarding an internal NSA unit. “Those crazy shadow brokers, I’m about as Equation Group as Matt Suiche or similar but he did not, not single denial.”
One theory Suiche offered for the interest shown by the group is that he had tagged them on Twitter multiple times in order to get their attention.
Another possibility is that some of Suiche’s more prominent research — some of which looked at unique malware that covertly writes to computer memory like that allegedly used by the NSA — was once relevant to the group even before August 2016 when their original blog post was published.
The impact of each Shadow Brokers release has been felt globally, as other hackers have been quick to adopt the high-quality toolset to launch their own attacks. Since April alone, the leaks have contributed to intrusions that resulted in well over $300 million dollars worth of damages, based on financial disclosures by victim organizations including FedEx, Maersk and Merck.
“Another global cyber attack is fitting end for first month of theshadowbrokers dump service,” the Shadow Brokers wrote in June. “Don’t be let company fall victim to next cyber attack, maybe losing big bonus or maybe price on stock options be going down after attack.”
The group’s continued online presence via blog posts has led to notable stress among current and former intelligence community leaders. In May, former NSA Director Michael Hayden criticized the spy agency, telling the New York Times “I cannot defend an agency having powerful tools if it cannot protect the tools and keep them in its own hands.”
In November 2016, three months after the Shadow Brokers originally appeared online, The Washington Post reported that then-Defense Secretary Ash Carter had recommended removing current NSA Director Michael Rogers from his position to former President Barack Obama. Carter reportedly made this suggestion due in part to “major compromises of sensitive hacking tools by personnel working at the NSA’s premier hacking unit: the Tailored Access Operations (TAO).”
Nothing Else To Do
Although Suiche is a well known figure, especially among cybersecurity professionals interested in Microsoft applications, his research began to receive mainstream press attention following The Shadow Brokers’ disclosures. His findings and commentary usually guide the news cycle each and every time the enigmatic group posts new material.
https://twitter.com/msuiche/status/819791987226251265
Born in a small town outside Paris in 1988, Suiche first became interested in programming during his early teenage years.
In 2007, he dropped out of high school and later decided to forego college in favor of entering the workforce early and to spend more time building software.
“It’s the classic story, you know. There was really nothing else to do where I grew up and so I tried to break things and that led to reverse engineering,” Suiche said during a phone interview. “In France, everyone is very focused on your diploma, on whether you went to university, it’s a requirement for a lot of jobs … I had to look outside the country for a job.”
While Suiche was still a teenager, he presented at several large international security conferences, including a Europol-sponsored event that eventually led him to employers. Suiche’s presentations were related to vulnerabilities and potentially exploitable features in Microsoft products.
His first internship out of school was with Airbus, a French aerospace and defense firm. Two years laters, he moved to The Hague after securing a research position with the Netherlands’ Forensic Institute (NFI), an agency under the country’s Ministry of Justice that helps law enforcement solve computer-related crimes.
Suiche currently works full-time, based in the United Arab Emirates. He frequently speaks at security conferences, giving talks on cloud computing, computer memory forensic tools and blockchain applications.
As the CEO of Comae Technologies, a four-person company he founded which is largely focused on computer memory forensic capabilities, Suiche guides the development of several products related to blockchain management, threat intelligence collection, penetration testing and application security.
In part, Comae Technologies’ self-described speciality of “in-memory malware detection” is one of the primary reasons for why Suiche has been able to quickly analyze and translate what the The Shadow Brokers have been leaking. While it remains relatively rare for malware to be configured in such a way that it works directly from memory, rather than on disk, there’s increasing evidence that nation-states and other advanced hacking groups leverage the technique.
“Purely memory-based malwares are not as common, but they are getting more and more common,” Suiche said. “DOUBLEPULSAR (one of the NSA-linked tools published by The Shadow Brokers) module injection was a nice display of the state of the art in that domain four years ago.”
The Grugq, a well-known security researcher who recently joined Comae, said he met Suiche more than five years ago. He described Suiche as “one of the best” Windows security researchers not currently employed by Microsoft.
“I’ve known Matt for years, almost a decade,” The Grugq said. “He’s well-respected in the community for his technical skills and well liked for his easygoing attitude. I can’t remember where or when I first met him, but it must have at an infosec conference. We met at a number of subsequent cons, as well as socially on occasion. He’s a smart, funny, guy … Matt is one of the best Windows internals guys outside of Microsoft.”
The Grugq, a popular commentator on international cybersecurity espionage developments, is a pseudonym used by the researcher in order to preserve his privacy.
Comae Technologies is the third company that Suiche helped launch.
His previous firm, CloudVolume, was sold to VMWare in 2014 for an undisclosed fee. The sale provided Suiche with money to invest in a small group of London-based tech startups in recent years. CloudVolumes, originally named SnapVolumes, sold a Windows-specific software product that allowed users to test and delivery applications within a container.
Prior to CloudVolumes, Suiche founded a small managed service firm named MoonSols while he lived abroad and traveled around the world. In most of these experience, Suiche and his colleagues worked remotely from different cities and countries. That continues to be the model with Comae.
Back to reality
August 2017 marked the one year anniversary of the Shadow Broker’s initial blog post. A March 2017 message was the last time the group released any sort of actionable information or sensitive material. Recent public announcements have provided little more than a reminder that some of the material taken by the group is still for sale.
Most of The Shadow Brokers tweets were scrubbed several months ago. And the group’s social media account is far less active than it once was.
For the moment, it appears to be a quiet period.
It’s not clear why The Shadow Brokers became interested in Suiche or when they first came to know he existed. While the saga has led to press attention, he isn’t phased by the group’s infatuation.
“I don’t know, life goes on. They don’t have any operational notes involving me so at the end of the day it doesn’t matter,” Suiche told CyberScoop.




