Iranian hacking campaign that included former U.S. ambassador exposed

Hackers possibly affiliated with Iran have been running a spearphishing campaign targeting former Israeli officials, high-ranking military personnel, the head of a leading security think tank and former U.S. ambassador to Israel, researchers with cybersecurity firm Check Point said Tuesday.
The campaign includes spearphishing conducted through both hijacked legitimate and phony email accounts, a fake URL shortener, a credential-harvesting Yahoo-themed phishing page and the use of a legitimate document verification service to obtain targets’ ID or passport scans.
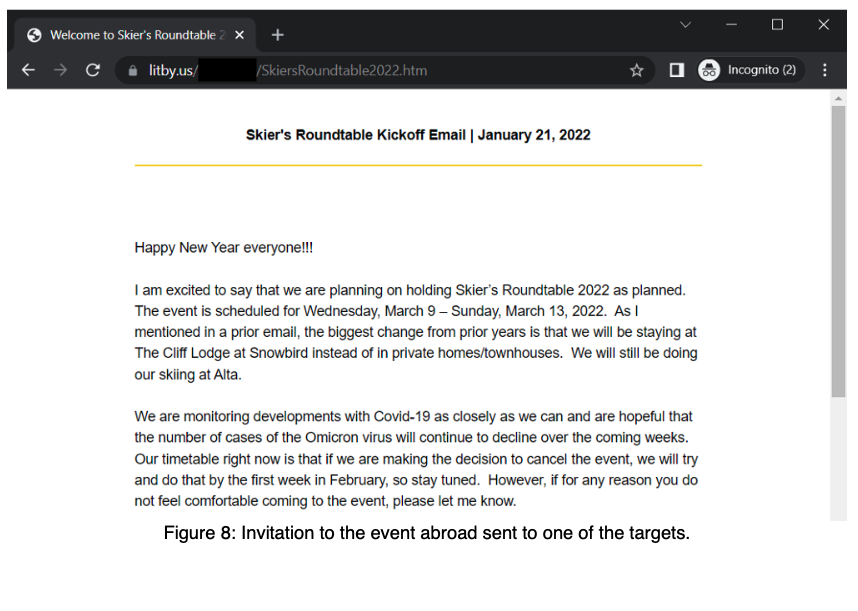
One part of the campaign included a credential-stealing page mocked up as an invite to a “Skier’s Roundtable.” It could have been merely a form designed to steal credentials, the researchers noted, or there’s a chance it was an example of an Iranian plot to lure Israeli targets to overseas events “in a suspected ploy to kidnap them.”
A similar Iranian operation was exposed last month by the Shin Bet, Israel’s security agency, according to the Jerusalem Post.
Researchers at Israel-based Check Point speculate that the campaign could be the work of Phosphorus, a prolific Iranian government-connected cyber-espionage group also known as APT35, Newscaster Team, Charming Kitten or Magic Hound. The partial attribution is based on the campaign’s prime targets, an Iranian-IP address in the source code of the Yahoo phishing page and old, commented-out code (code that’s there, but not being acted on or run) from a Phosphorus campaign analyzed by Microsoft in 2020.
“We have exposed Iranian phishing infrastructure that targets Israeli and US public sector executives, with the goal to steal their personal information, passport scans, and steal access to their mail accounts,” Sergey Shykevich, threat intelligence group manager at Check Point, said in a statement. The campaign dates at least to December 2021, but likely has been going on longer than that, he added.
“The most sophisticated part of the operation is the social engineering,” Shykevich said. “The attackers use real hijacked email chains, impersonations to well known contacts of the targets and specific lures for each target. The operation implements a very targeted phishing chain that is specifically crafted for each target. In addition, the aggressive email engagement of the nation state attacker with the targets is rarely seen in nation state cyber attacks.”
“The spearphishing infrastructure we exposed above puts special focus on high-ranking Israeli officials in the midst of escalating tensions between Israel and Iran.”
Check Point research
The campaign exposed in Tuesday’s research represents just the latest back and forth between Israel and Iran that has included real life assassinations and a host of tit-for-tat cyberattacks over the last few years.
The targets in this campaign included Tzipi Livni, a former Israeli foreign minister and deputy prime minister, an unnamed former Israeli major general who “served in a highly sensitive position in the Israeli Defense Forces,” a chair of one of Israel’s leading security think tanks, a senior executive in the Israeli defense industry, a former chair of a well known Middle East research center and an unnamed former U.S. ambassador to Israel.
The Iranian hackers apparently impersonated the former U.S. ambassador to target a leading think tank chairperson, the Check Point researchers wrote. The hackers managed to access one of the two targets’ email boxes — the research doesn’t identify which one — and then impersonate the U.S. ambassador by following on a genuine email thread the pair had two weeks prior.
“The spearphishing infrastructure we exposed above puts special focus on high-ranking Israeli officials in the midst of escalating tensions between Israel and Iran,” the researchers wrote. “With recent assassinations of Iranian officials (some affiliated with Israeli’s Mossad), and the thwarted attempts to kidnap Israeli citizens worldwide, we suspect that Phosphorus will continue with its ongoing efforts in the future.”






