Researchers warn of critical vulnerability in GE anesthesia machines
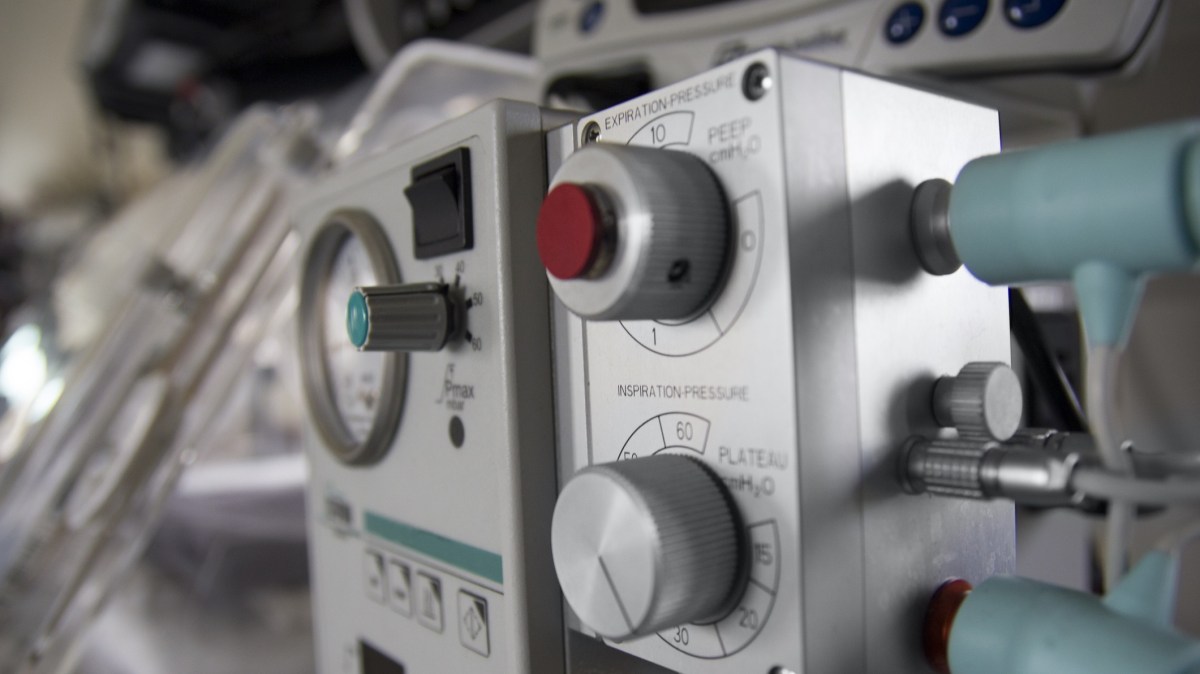
A flaw in the firmware of anesthesia and respiratory devices made by General Electric could allow a hacker to change the composition of gases dispensed by the equipment, putting patients at risk, cybersecurity researchers warned Tuesday.
“If exploited, this vulnerability could directly impact the confidentiality, integrity and availability of device components,” CyberMDX, the health care security company that discovered the issue, said in a statement.
For the vulnerability to be exploited, a hacker would need access to a hospital’s network and for the machines to be connected to a terminal server, or one that allows enterprises to connect to multiple systems, according to CyberMDX. But with that access, an attacker could not only alter gas composition, the researchers said, but also silence alarms on the equipment and change dates and timestamps that document a patient’s surgery.
“Once the integrity of time and date settings has been compromised, you no longer have reliable audit trails,” said Elad Luz, head of research at CyberMDX. “That’s a very serious problem for any medical center.”
The vulnerability is in versions 7100 and 7900 of GE’s Aestiva and Aespire anesthesia devices.
The Department of Homeland Security amplified the warning in a separate advisory on Tuesday that encouraged users to report any malicious activity related to the vulnerability.
A spokesperson for GE’s health care unit said that the company had investigated and found that the scenario described in the research “does not introduce clinical hazard or direct patient risk, and there is no vulnerability with the anesthesia device itself.”
While declining to say how many of the affected devices are in the field, the spokesperson said systems sold after 2009 no longer include the ability to modify gas parameters.
The research points to a broader problem with firmware insecurity in medical devices, Luz told CyberScoop. “Lack of user authentication is a common problem in the design of medical devices and must be addressed,” he said in an email.
CyberMDX first reported the vulnerability to GE in October. Luz lamented the long vulnerability disclosure process in the medical-device industry, which typically involves extensive testing and delicate discussions of when security issues can be made public.
“It should not have taken nine months for publication,” Luz said.






