Bank heist with FIN7 traits went down while leaders were on the run, research suggests

Digital thieves who spent more than two months lurking inside the networks of an Eastern European bank last year used the same techniques as the infamous cybercriminal gang known as FIN7 or Carbanak, according to new research.
Romanian security vendor Bitdefender said Tuesday its researchers have uncovered new details about a bank heist in which hackers patiently collected employee credentials and other data meant to help them access banking data and control ATM networks. These findings coincide with previous researchers’ suggestion that FIN7 is a relatively large group made of perhaps a dozen individuals who have been able to weather law enforcement pressure while updating their hacking tactics.
The 2018 breach at the bank, which Bitdefender declined to identify, occurred as international authorities were taking action against alleged members of FIN7, an organized crime group that threat intelligence researchers may have stolen $1 billion. The group carried out the attack detailed in the new Bitdefender research while international law enforcement was pursuing its suspected leaders.
The U.S. Department of Justice announced last year that two accused FIN7 leaders were apprehended in January, while a third was caught in June. FIN7 is typically associated with malware known as Carbanak, but Bitdefender’s report labels the group itself as Carbanak, and a researcher says the cybersecurity company uses the names interchangeably.
The attack detailed in Bitdefender’s research Tuesday began with phishing emails sent on March 7 and ended in May, when the attackers deleted the evidence they collected documents relating to a banking application. They relied on the Cobalt Strike Beacon malware to access the victim’s systems, then collected employee usernames and passwords, and ultimately sensitive documents about banking protocols that would be useful for later attacks, said Liviu Arsene, a senior cybersecurity analyst.
“They were looking for specific documents related to internal banking procedures, internal applications and how those work,” he said. “They then stockpiled them in just an archive. They were critical documents about the way some applications need to interact with each other, and it had to do with who would vet transactions.”
It’s not clear how much money the hackers stole in this case.
Use of Cobalt Strike Beacon has become commonplace, researchers previously told CyberScoop, but the speed with which the hackers in this case moved through victim networks suggested a rare expertise, according to Arsene.
After the first bank employee clicked on a phishing email, it took no more than two hours for the hackers to “access almost everything,” Arsene said, pointing to a professional job. The hackers also selected single workstations as central hubs for storing the information they collected, a move that minimized the amount of evidence.
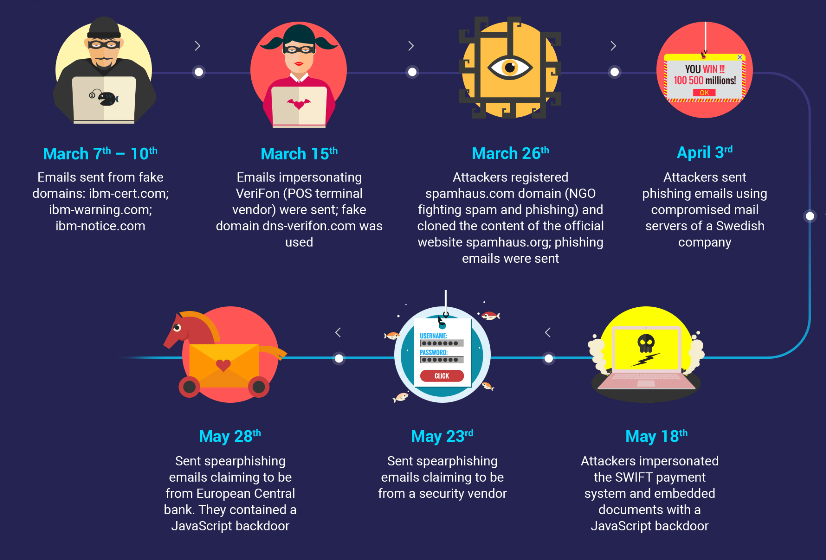
A graphic from Bitdefender’s research provides a timeline of a hack on an Eastern European bank.
“They tried to access the ATM network, which is standard [modus operandi] for Carbanak,” Arsene said. “They interact the ATM network to send out cash at a specific time through their diagnostic mode, and tell a mule to stand in front of it at that time. Or, they use a specific credit card and deactivate the controls around that card so they can take out money.”
Researchers have tied other recent hacking activity to the collective since the Justice Department announced the three suspects had been apprehended. Researchers from the threat intelligence provider Flashpoint in March said they found evidence FIN7’s infrastructure had started to reappear in the form of SQLRat, a malware strain spread via phishing emails.
Andrii Kolpakov, the Ukrainian man accused of working as the group’s hacking director, was extradited from Spain and appeared in U.S. court for the first time Monday, according to the Justice Department.





