Election workers in battleground states faced onslaught of malicious emails, researchers say

County election workers in Arizona and Pennsylvania were inundated with a “surge” in malicious emails ahead of those states’ August primaries, security researchers said Wednesday, highlighting the ongoing threat facing election officials weeks before contentious midterms.
The malicious activity, which included password theft attempts and efforts to deliver malware via poisoned links, is particularly concerning considering that county election workers are often “the least sophisticated actors in terms of cybersecurity postures, but the most critical in actual electoral engagement with voters,” researchers with cybersecurity firm Trellix’s Advanced Research Center said Wednesday.
Voting officials and poll workers nationwide have become much more security aware since the 2016 Russian election interference operations, but malicious activities remain a concern for all election workers who “have become targets of threats and intimidation in the physical realm,” the researchers said.
Poll workers around the country have faced a growing number of threats ahead of the 2020 election and in the months after. Now, officials in multiple states are reporting new pressures ahead of the midterms. Some state officials have reported a deluge of records requests from “self-styled fraud investigators,” The New York Times reported recently, while others have been offered training designed to prevent violence through de-escalation, CNN reported Sept. 30.
Lawmakers in California recently approved legislation that allowed election workers to keep some personal information private as part of a program originally designed for domestic violence survivors and people who work at abortion clinics. And 15 of the 30 election offices polled by Reuters recently reported enhancing physical security protections after 2020, including installing panic buttons to hiring extra security guards.
Given the growing hostility over elections, “the damage that can come from things like phishing has been elevated since 2020 because of the extremely corrupted information environment that we’re in,” said Eddie Perez, an election administration expert and a board member at the OSET Institute, a nonprofit organization that promotes open-source election technology.
“Whether there is real technological damage from phishing or from an infiltration, it doesn’t really matter anymore,” Perez said. “Because there is such skepticism and so much disinformation that the possibilities of a perception hack have really been elevated.”
Data from Trellix shows that the number of detected malicious emails targeting Arizona county election officials more than tripled from 617 in the first quarter of 2022 to 2,246 the third quarter. The activity peaked around Arizona’s Aug. 2 primary, researchers said.
A similar trend played out in Pennsylvania. According to the company’s data, around that state’s May 17 primary, the number of malicious emails increased from 1,168 in the fourth quarter of 2021 to 4,460 in the first quarter of 2022. That’s a 382% increase. The following quarter, the number of harmful emails increased another 169%.
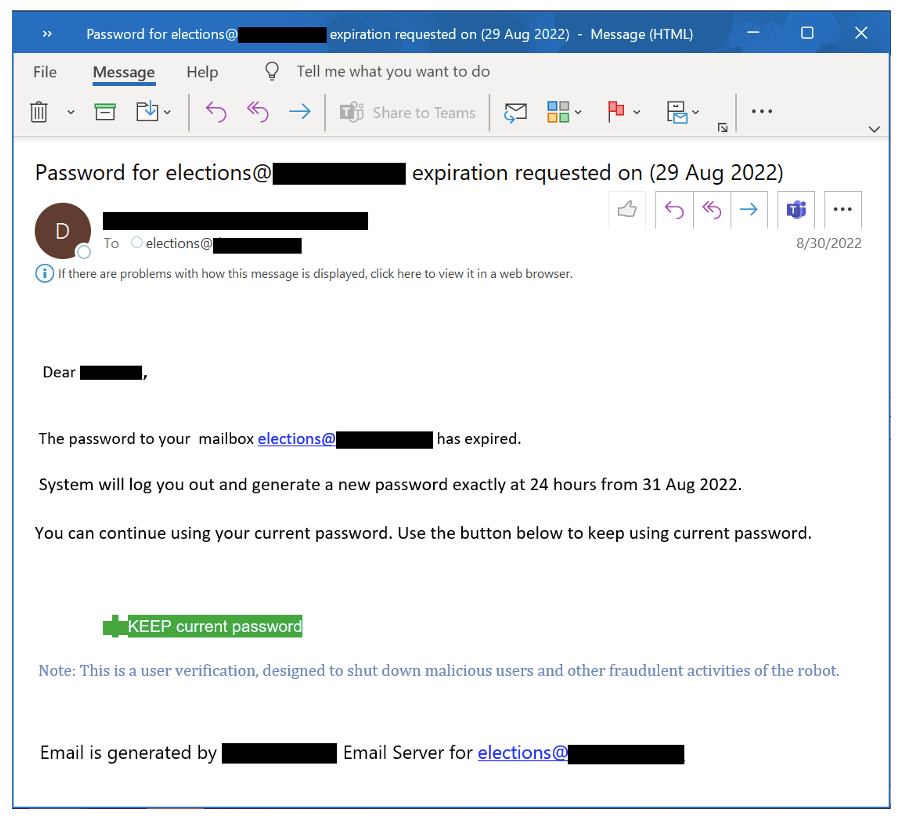
In one example, election workers received an email notifying them that their email password was set to expire. A malicious link would direct the recipient to either confirm their current password or create a new one, handing the credentials to the attackers, the researchers said.
In another scenario, attackers used a hijacked email thread between a county election worker and a contractor tasked with distributing and collecting absentee ballot applications. The compromised thread dated to 2018 and involved discussion of the application language and an attachment. The more recent email, sent to the unnamed elections office in February 2022, tried to get the worker to download “receipts” from a Microsoft OneDrive URL that the Trellix researchers said was “poisoned with malware capable of infecting the election employee’s system and perhaps gaining access to other systems across his organization’s networks.”
The malware variant is not identified, and the researchers said they don’t know whether the hijacked thread was the result of a breach or a “clever forgery.” This particular email was blocked through the detection of the malware, they added.
Nevertheless, the episode shows how this scenario is using established connections to get malware delivered to an election worker’s machine. Multiple examples of thread hijacking have been seen over the years, and it’s a tactic that works.
“Ultimately, this phishing scheme plays on the election worker’s professional and moral commitment to help a trusted contractor struggling to register people to vote,” the researchers said. “It relies on the election officials’ willingness to perhaps step outside an established submission process and click on the attacker’s poisonous link to access the voter applications.”
Attackers using contractor relationships to target election officials have been seen in the past, as well. In 2016, hackers later linked to the Russian government sent an email to multiple election officials posing as an elections equipment vendor sharing instructions for its various products.
On Oct. 4, the FBI and the Cybersecurity and Infrastructure Security Agency issued a joint announcement informing the public that attempted compromises of election infrastructure are “unlikely to result in large-scale disruptions or prevent voting,” and that the agencies were unaware of any cyber activity that had ever prevented “a registered voter from casting a ballot, compromised the integrity of any ballots cast, or affected the accuracy of voter registration information.”
The agencies warned officials to be wary of emails or phone calls from unfamiliar addresses, and to exercise caution with attachments or links sent via email. Trellix researchers offered similar advice, but added that emails with urgent calls to action, such as password changes, should be on the radar as well.





