Hottest trend for phishing scammers: Buying web domains instead of hacking them
Hackers are increasingly abusing the highly decentralized web domain-name registration system to buy internet addresses they can use in phishing attacks, a new report says.
The scams use legitimately acquired addresses to set up webpages that mimic bank or other e-commerce sites with the intention of tricking consumers into giving over login details and passwords. Such abuse of the domain-name registration system is not new, but it more than trebled last year, according to the Anti-Phishing Working Group’s 2016 Global Phishing Survey, released last week.
The report documents in detail more than a quarter-million individual phishing sites that mimicked the web presence of nearly 700 genuine banks or other financial, e-commerce or social media companies and attracted potential victims through links in spam email or other messages.
Those 255,056 phishing sites were hosted on nearly 200,000 domains (some domains had multiple sites on them), almost half of which, or 95,424, were registered by hackers through the legitimate domain registration system, overseen by the global non-profit Internet Corporation for Assigned Names and Numbers, or ICANN.
That number represents a three-fold rise over 2015, the report states, and the largest number ever recorded since the working group began keeping statistics in 2007. It is still only a tiny proportion of the 329.3 million domain addresses registered as of the end of 2016.
The remaining 100,000 or so phishing sites the working group catalogued were set up without the knowledge or consent of the genuine domain owner — usually through hacking.
Malicious registrations are designed to facilitate domain impersonation — a .cc site masquerading as a .com site, for example, or a misspelling of a brand name with a normal-looking .com at the end. More than three quarters (78 percent) of all the malicious registrations were in just four Top Level Domains or TLDs — .com, .cc, .pw and .tk. The largest TLD of all, .com, hosts the massive lion’s share of 58 percent of maliciously registered domains, while .cc is home to 14 percent and the remaining 6 percent is split equally between .pw and .tk.
The prevalence of the country code TLDs for the tiny Pacific island nations of Cocos (.cc), Palau (.pw) and Tokelau (.tk) is no coincidence. All three nations have delegated the authority to register web names within their domain to commercial registrars, who sell or give away the registrations to people or companies completely unconnected with the islands — in some cases with little scrutiny.
Despite fears that the proliferation of new TLDs orchestrated by ICANN starting in 2014 would be a boon for phishers and other cybercriminals, the figures appear to show otherwise. TLDs such as .sex and .bank were added with hundreds of others, creating multiple new possibilities for domain impersonation.
“Phishing in the new TLDs is rising, but is not yet as pervasive as it is in the domain space as a whole,” according to the report. However, 86 percent of the phishing sites on new TLDs were registered and not hacked, compared to less than 50 percent for the web as a whole.
Almost half of all malicious registrations were attributable to phishing gangs targeting Chinese banks or other brands, according to the report, representing almost a quarter of phishing attacks worldwide. This was down steeply from prior years, when up to 80 percent or more of malicious registrations were targeting Chinese sites. “There was a huge rise in malicious domains used to target non-Chinese targets,” states the report.
“It was disheartening to see the registration of so many malicious domain names to mount attacks, after all the great work that’s been done to curtail phishers in recent years,” said Rod Rasmussen, Founder of R2 Cyber and a co-author of the APWG study. “This should be a wake-up call for the domain name industry.”
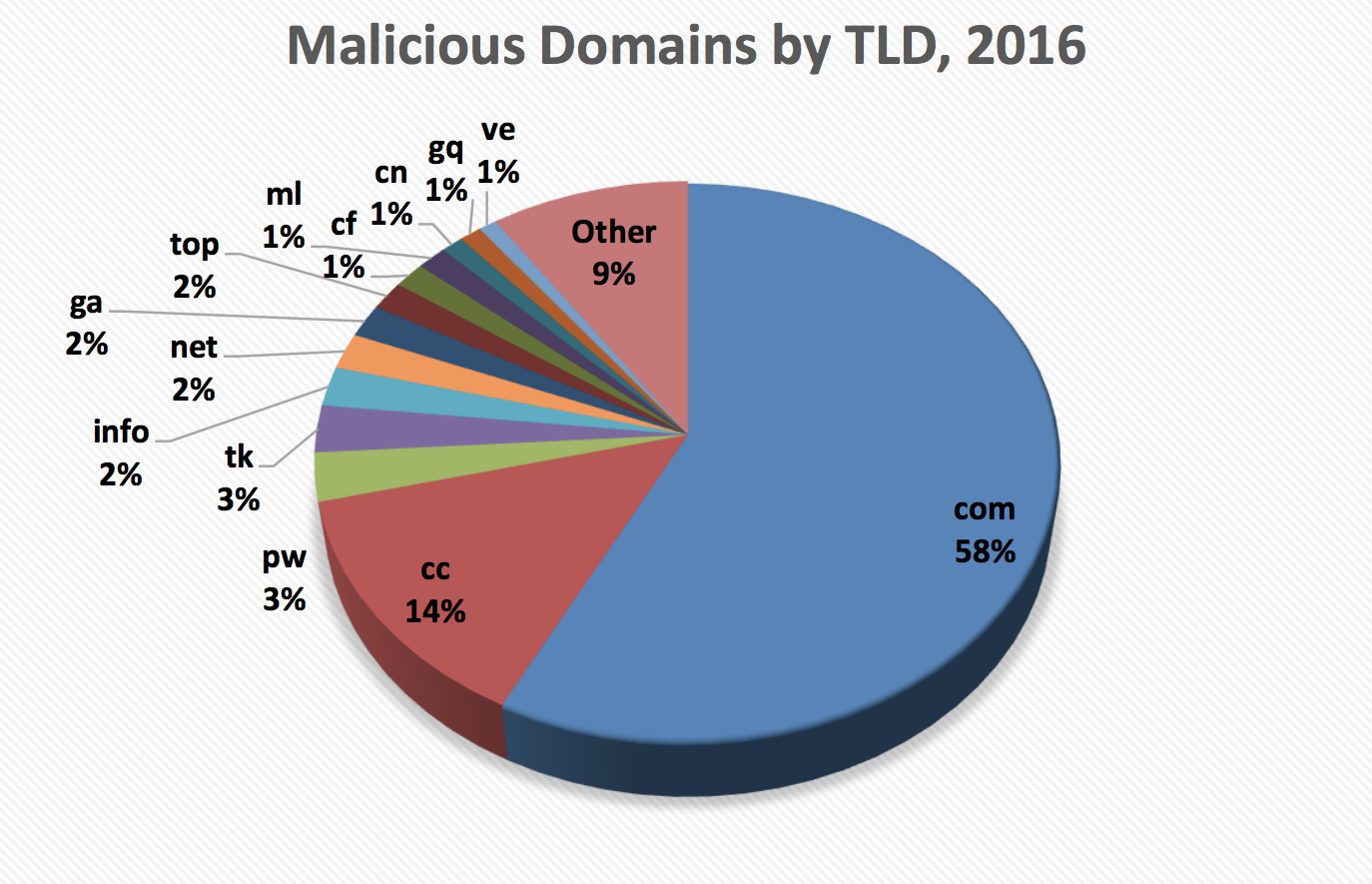
Malicious domain registrations in 2016 by Top-Level Domain (Source: APWG)
Fifty-two percent of the 195,475 unique domain names used by phishers in their attacks were employed without the domain owner’s consent — usually by hacking or other compromise of the server hosting the site, or of the domain owner’s registration account.
Finding, or better still preventing, such attacks is a challenge for many large enterprises, explained Scott Gordon of RiskIQ, a cybersecurity outfit that provides what it calls a “complete digital footprint” for customer companies.
“When you’re talking large enterprises, with multiple different [departments] … cataloguing all your public-facing assets … gets to be a very complex mess, if you try to do it manually,” said Gordon.
Such a complete map of internet assets would be useful in combatting a new form of website compromise noted by the APWG report, known as “domain shadowing.”
Domain shadowing is a “hybrid attack” in which hackers take over a legitimate website’s Domain Name System or DNS control portal, in order to set up new subdomains that point to the phishers’ fake sites. DNS is the traffic system of the internet — the distributed database which translates the written web address starting www. into the numeric IP location which takes web browsers to the correct server, hosting the website they are trying to visit.
The DNS portal of Example Company, for instance, with genuine domains www.examplecompany.com and mail.examplecompany.com, could be hacked to create subdomains like customerservice.examplecompany.com or accounts.examplecompany.com. Because they control the DNS portal, the hackers can set their own IP location as the numeric translation of these subdomains. If they don’t interfere with the real domains being used by the company, it’s unlikely anyone there will ever notice the malicious subdomain.
Overall, the number of phishing sites was up more than 10 percent since the previous year, the report found.


