Hackers posed as Amnesty International, promising anti-spyware tool that actually collects passwords

Fraudsters are posing as human rights group Amnesty International to trick individuals into downloading malicious software, researchers at Cisco’s threat intelligence unit Talos report.
Masquerading as the human rights group, hackers registered multiple domains using variations on the Amnesty name to advertise a demo for “Amnesty Anti Pegasus” software that could allegedly scan devices for the NSO Group spyware, which Amnesty has closely examined. The malware had a realistic-looking “Anti Pegasus” user interface. In fact, victims downloaded Sarwent, a malicious software that gives attackers a backdoor to a victim’s machine.
Hackers can use that access to download and execute other malicious tools as well as exfiltrate data such as passwords.
The campaign preys on growing concerns around the threat of spyware. Human rights advocates have long criticized the NSO Group for the use of its technology by governments to spy on activists, dissidents and journalists. A sweeping July report by Amnesty International and partners revealed that the spyware was using a vulnerability in the previous version of iOS to target more than three dozen victims. Apple patched against the vulnerabilities in September.
In light of the growing number of victims, groups including the United Nations have called for a moratorium on spyware technology until it meets international human rights standards.
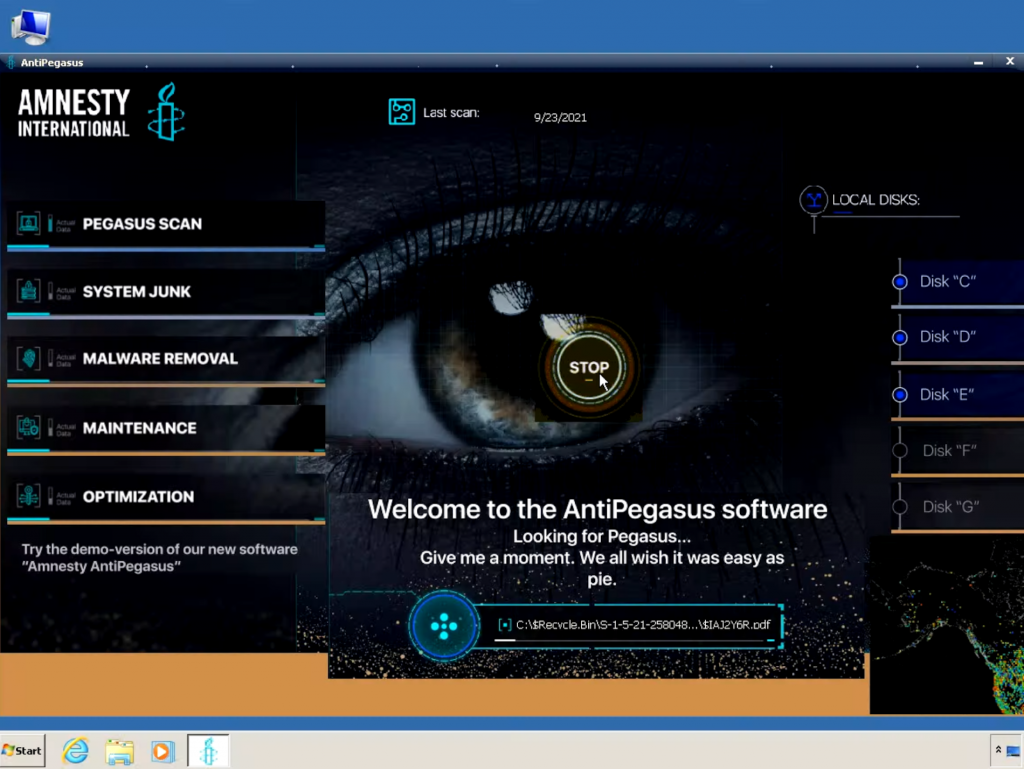
Fake anti-virus software (courtesy Talos).
The hacking campaign revealed by Talos targeted individuals who may be worried about Pegasus spyware, such as activists and journalists, raising the possibility that the campaign has ties to a state actor. However, researchers were unable to determine if a government was involved in the effort, and say it’s possible that the hackers may be leveraging a major news story for a financially motivated scam. Researchers say that some of the URLs flagged in the report are still live.
Researchers expressed high confidence that the actor behind the campaign is based in Russia and has ran similar campaigns since January. Two of the domains associated with the Amnesty campaign were registered to addresses in Ukraine.
What’s still unclear is how the group is spreading the fake domains. While Talos observed the lure domains being accessed globally — primarily across Eastern Europe and North America – there’s no indication the traffic came from search engine matches or an email campaign.
A spokesperson for Talos said the security firm has reported its findings to Amnesty. CyberScoop reached out to Amnesty International for comment.






