Clop is back to wreak havoc via vulnerable file-transfer software

In what we can assure you is a new cybersecurity incident despite sounding incredibly similar to incidents of past notoriety: threat actors tied to a notorious ransomware and extortion group have exploited file-transfer software to carry out attacks.
Clop has claimed responsibility for attacks tied to vulnerabilities in software made by Cleo, an Illinois-based IT company that sells various types of enterprise software. The vulnerabilities, which affected Cleo’s LexiCom, VLTrader, and Harmony products, have led to worries that sensitive data across various industries could be swiped by the group in a repeat of some of the most damaging security incidents of the past few years.
The cybersecurity community was first alerted of the threat earlier this month when Huntress Labs identified that threat actors were exploiting Cleo’s software en masse. The flaw, catalogued as CVE-2024-50623, is an unrestricted file upload and download vulnerability that could lead to remote code execution. Cleo originally released fixes for CVE-2024-50623 in October, but the company issued another patch last week to further fix the issue.
Shortly thereafter, a new critical vulnerability was identified (CVE-2024-55956), allowing unauthenticated users to execute code through the Autorun directory. Cleo quickly issued another patch.
While the exact number of exploited systems remains unclear, cybersecurity firm Rapid7 cited a discernible uptick in compromised endpoints received via its customer telemetry..Huntress said in its initial research blog that approximately 10 businesses were attacked via the vulnerability, notably impacting sectors such as consumer products, food, and shipping.
According to Shodan, a search engine that scans IP addresses to find and access devices and systems connected to the internet, there were 390 exposed systems with the affected Cleo software as of this article’s publication. Cleo’s customer base spans around 4,200 organizations.
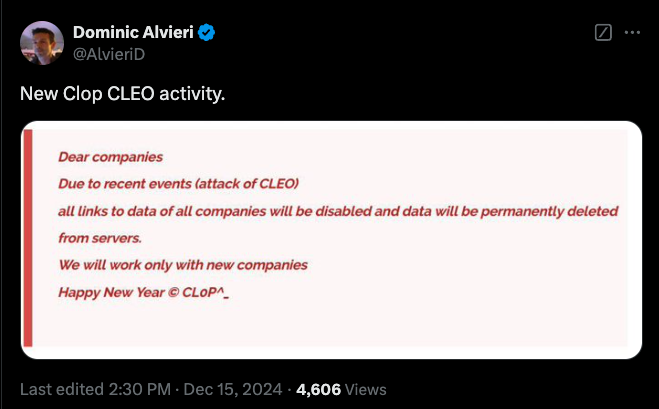
Last weekend, Clop published a blog post on its data leak site claiming responsibility for the attacks.
Clop has made a name for itself via vulnerabilities in this particular type of software, most notably related to the MoveIT breach in 2023. In May 2023, hackers with Clop exploited a previously undetected vulnerability in MOVEit software, which the group used to attack “hundreds of companies” as “part of exceptional exploit.” The exploit, which allowed the group to steal data via supply chain attacks, affected thousands of companies. Some risk management firms have stated that the attack is estimated to have cost companies a combined $12.15 billion.
The hacking group was also responsible for attacks related to similar software, including Fortra’s GoAnywhere MFT and Accelion’s file-transfer software.
Several cybersecurity experts told CyberScoop that the activity tied to Cleo’s software is the first time the group has surfaced since the MOVEit breach, indicating that Clop has been squarely focused on finding vulnerabilities in file-transfer software.
“It is plausible that Clop had prior knowledge of several vulnerabilities in the CLEO platform, enabling the group to breach and extract data from victim organizations systematically long before the vendor issued any public security advisory,” said a spokesperson for Intel471, a Texas-based threat intelligence company. “By timing their public disclosures and media engagement, the group likely intends to maximize the pressure on victims and amplify the overall impact of these attacks.”
Kimberly Goody, head of cyber crime analysis for Mandiant Google Cloud, told CyberScoop it is possible that the Cleo incidents show the threat actors, which the company tracks as FIN11, may have learned from the MOVEit breach and refined their techniques.
“Current evidence suggests that this may not have been a smash-and-grab as we observed with the MoveIt attack,” Goody said. “The targeting of these systems in the past has often not resulted in additional post-compromise activity other than the data theft and extortion; however, we have observed beacon deployment which could signal that the threat actors may have intended to also deploy ransomware.”
The Cybersecurity and Infrastructure Agency added one of the Cleo vulnerabilities to its Known Exploited Vulnerabilities list Tuesday, stating the addition is “based on evidence of active exploitation.”






