Political fallout in cybercrime circles upping the threat to Western targets

The Russian war on Ukraine’s impact on the cybercrime underground is starting to become clearer, with the fallout having significant implications for cyberattack targeting and an increased threat to Western nations’ critical infrastructure, according to new research.
The findings, published Monday by Accenture’s Cyber Threat Intelligence team, document how “previously coexisting, financially motivated threat actors [are dividing] along ideological factions.” Some of those splits have resulted in high-profile developments, such as a Ukrainian cybersecurity researcher with access to the Conti ransomware group’s inner workings publishing years of the group’s internal chats, code, and other materials.
“This divide has led to pro-Russian actors galvanizing against Western targets, especially in the resources, government, media, financial and insurance industries.”
Accenture Cyber Threat Intelligence team
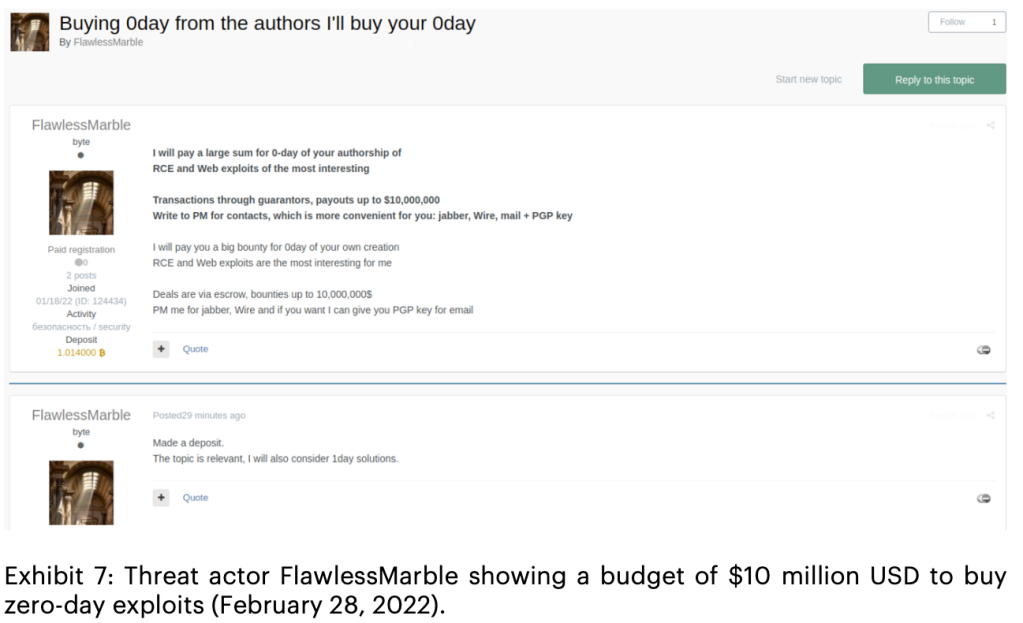
But Accenture notes that other, more subtle reflections of the fallout from Russian President Vladimir Putin’s decision to attack Ukraine are just as serious and, in some ways, more worrying for the threat landscape. The mostly financial motives of the past are, in some cases, giving way to political motivations, with prolific cybercrime actors pushing for more access to critical infrastructure targets by offering up to $500,000 for network access, and up to $10 million for zero-day exploits.
“This divide has led to pro-Russian actors galvanizing against Western targets, especially in the resources, government, media, financial and insurance industries,” the Accenture researchers note.
In some cases, network access brokers — cybercriminals who sell credentials and other access to potential target networks, serving as a key part of the ransomware chain — are exclusively selling to or offering discounts to pro-Russian sources, while declining to sell access to attackers who want to target Russian entities.
Political motivations, rather than financial motives, increase the threat to Western organizations, according to the Accenture researchers.
Hacktivists often target Western organizations, the researchers note, but those attackers typically employ cheap or free tools that rarely impact victim business operations significantly.
“On the contrary, ransomware collectives are well-funded, employ one-day or zero-day exploits, have elevated tradecraft and large budgets, and are organized, allowing them to disrupt businesses more efficiently and for prolonged periods,” the researchers wrote.
Accenture observed “some of the biggest and seemingly ever-rising budgets” for custom malware and exploits: One post from Feb. 22 offered $5 million to $10 million for remote-code execution and web exploits.
Another impact has been for cybercriminals calling on forum moderators to allow ransomware operators and affiliates back into the mainstream forums. In May 2021, after the DarkSide ransomware attack on Colonial Pipeline drew international heat and attention, administrators for the more mainstream cybercrime forums banned ransomware actors in hopes of avoiding scrutiny from international law enforcement.
Accenture notes that the ban didn’t cause ransomware actors to disappear, but it did complicate the ability to acquire tools, recruit affiliates, and gain exploits or access to target networks.
Letting them back into the forums will not only make it easier for attackers to target Western organizations more efficiently, “but also embolden them, as other underground actors would likely herald ransomware actors’ return and give those ransomware actors perceived moral reason to conduct attacks, especially against critical national infrastructure.”
On Thursday the U.S. Senate approved legislation that would require U.S. criticial infrastructure operators to report incidents and ransomware payments.
The shift from financial to political motivation “is unprecedented and may bring about far-reaching consequences,” the Accenture researchers wrote. Cybercriminals coming to the defense of Russia in the face of what they see as Western attacks on Russia “will ensure a prolonged, heightened threat to Western entities.”

This story was featured in CyberScoop Special Report: War in Ukraine





