Ransomware group claims 2.5 terabytes of stolen data less than a month after emerging online

A ransomware group has emerged in recent weeks and has already listed four victims including three in the U.S. on its leak site, researchers with the cybersecurity firm Cisco Talos said Monday.
The group that calls itself “RA GROUP” is just the latest entity to use the Babuk ransomware source code, which a developer leaked in September 2021 on a Russian-language forum. Just two months later Talos identified a group called “Tortillia” using the code to target Microsoft Exchange servers in multiple countries. And on Thursday, researchers with SentinelLabs reported identifying 10 distinct ransomware families deploying VMware ESXi hypervisor lockers based on the leaked Babuk code.
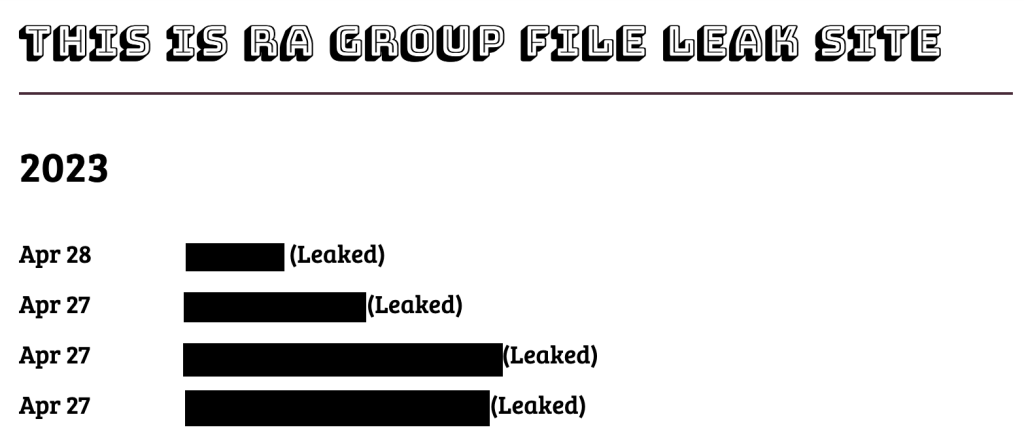
Despite having emerged online on April 22, RA GROUP has already claimed to have stolen nearly 2.5 terabytes of data across just four victims, three in the U.S. and one in South Korea. Three of the victims were posted April 27 and the next on April 28. The American targets include a smaller company in the insurance industry and two larger companies in financial services and an electronics supplier servicing the computer, communication, aerospace, marine and military industries.
The RA GROUP website has undergone cosmetic changes since it was first published, the Talos researchers noted, “confirming they are in the early stages of their operation.”
The group uses custom ransom notes for each victim that informs them they have three days to pay before a sample is published, and seven days before the full set is published, according to ransom notes obtained by Talos. Victim entity names are also hardcoded into the executable files, a characteristic the researchers describe as “unusual” for ransomware groups.





