Grand jury indicts Ukrainian for role in vast Raccoon Infostealer cybercrime operation

The Justice Department on Tuesday unsealed charges against a Ukrainian national for his role in the Raccoon Infostealer malware-as-a-service operation, which U.S. law enforcement officials blamed for infecting millions of computers around the world to steal personal data.
Raccoon Infostealer sold its malware on the for $75 per week or $200 per month, but reportedly claimed it shut down in March after one of its developers died in the Russian invasion of Ukraine, Bleeping Computer reported at the time.
Tuesday’s DOJ announcement said Mark Sokolovsky, believed to be one of the key figures behind Raccoon Infostealer, was arrested by Dutch authorities in March. At the same time, the FBI and law enforcement partners in Italy and the Netherlands “dismantled the digital infrastructure supporting the Raccoon Infostealer, taking its then existing version offline.”
By June, however, a new version of Raccoon Stealer was up and running, according to Bleeping Computer.
Sokolovsky — also known as “Photix,” “raccoonstealer,” and “black21jack77777” — faces charges of conspiracy to commit fraud and related activity in connection with computers, conspiracy to commit wire fraud, conspiracy to commit money laundering and aggravated identity theft, according to the indictment which was originally filed Nov. 2, 2021.
A court in Amsterdam approved his extradition to the U.S. He’s facing a maximum of more than 25 years in prison if convicted, the DOJ said.

The operation “infected computers in many countries” between 2018 through early 2022, the DOJ said, calling Sokolovsky “one of the key administrators.” The FBI had identified more than 50 million unique credentials and forms of identification — emails, bank accounts, cryptocurrency addresses, credit card numbers — “from what appears to be millions of potential victims around the world,” the DOJ said.
“The United States does not believe it is in possession of all the data stolen by Raccoon Infostealer and continues to investigate,” the statement said.
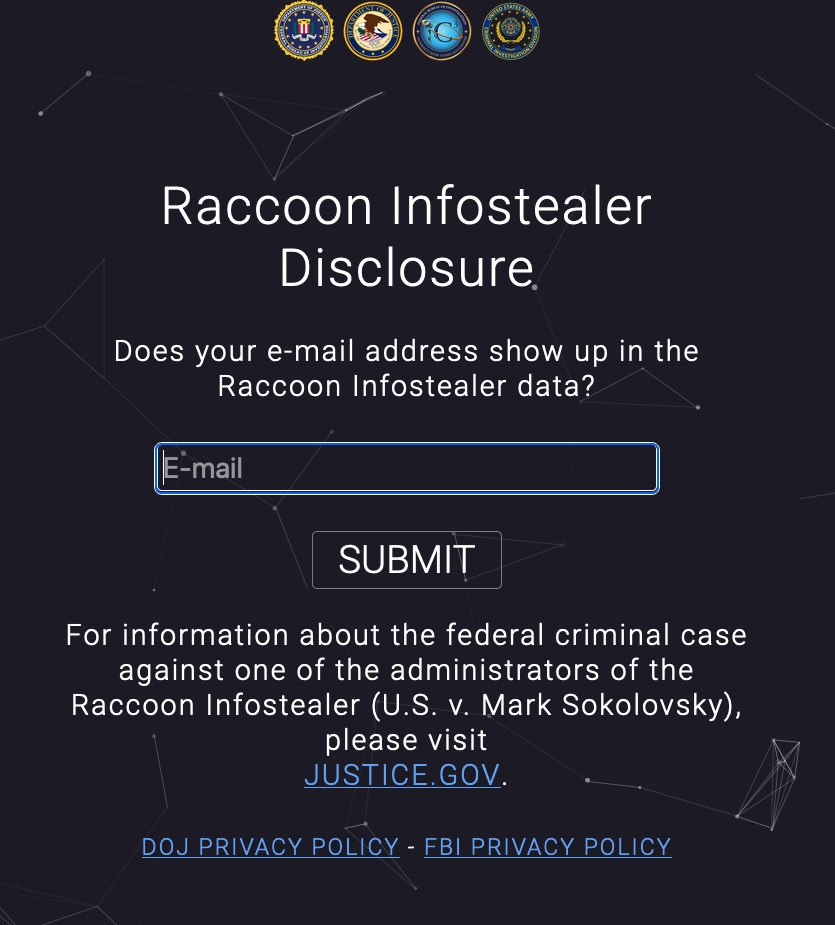
The government launched a page on the FBI’s Internet Crime Complaint Center site for people to search whether their email address had been stolen. The FBI will send an email to that address if it appears in the dataset.
The page was intermittently unavailable shortly after the DOJ announcement.
According to the grand jury indictment, Sokolovsky received a copy of the data stolen by people who leased access to the malware and “stored millions of stolen log-in credentials and financial information records in an online drive.”
“This case highlights the importance of the international cooperation that the Department of Justice and our partners use to dismantle modern cyber threats,” Deputy Attorney General Lisa O. Monaco said in a statement. “As reflected in the number of potential victims and global breadth of this attack, cyber threats do not respect borders, which makes international cooperation all the more critical. I urge anyone who thinks they could be a victim to follow the FBI’s guidance on how to report your potential exposure.”






