Hackers expect replies, not rewards, for finding bugs

More than 9 in 10 cybersecurity researchers who find software vulnerabilities generally let the makers know and coordinate their disclosure, according to a new survey from a Commerce Department working group published Thursday.
Only 1 in 6 (15 percent) expect any kind of reward, but nearly three-quarters (70 percent) expect to be engaged by the maker. It’s frustration around unmet communications expectations that’s most often the cause of unilateral disclosure, according to the survey report Vulnerability Disclosure Attitudes and Actions published by the National Telecommunications and Information Administration.
The survey was conducted as part of the agency’s multi-stakeholder engagement process on the issue of vulnerability handling and disclosure, which it launched in September last year. It was one of three publications from that process Thursday.
The disclosure issue is a vital one for cybersecurity. Hackers, including especially the “white hats” often referred to as security researchers, are inveterate tinkerers, and most vulnerabilities in software products are discovered independently rather than by the companies that make and sell them. Increasingly, tech giants like Microsoft and Google have teams of researchers looking for vulnerabilities in software throughout the Internet ecosystem, not just in their own product lines. Platforms like Bugcrowd are crowdsourcing the security audit process.
The importance of the disclosure issue was underlined in 2014 by the discovery of the Heartbleed vulnerability in OpenSSL — a piece of open source cryptographic software used in the large majority of secure websites across the globe. The scale on which OpenSSL was deployed made it impossible to alert everyone who depended upon it before the vulnerability was disclosed and malicious actors could start exploiting it.
The three working groups leading the NTIA multi-stakeholder process all published different reports Thursday.
The survey results were collected and analyzed by the Awareness and Adoption Group, which is looking at how to increase the understanding and use of best practices. Responsible disclosure usually means approaching the manufacturer or vendor of the software about the vulnerability first — and not disclosing it until they have fixed it. On the other hand, researchers argue, the threat of public disclosure is sometimes the only reason a bug gets fixed.
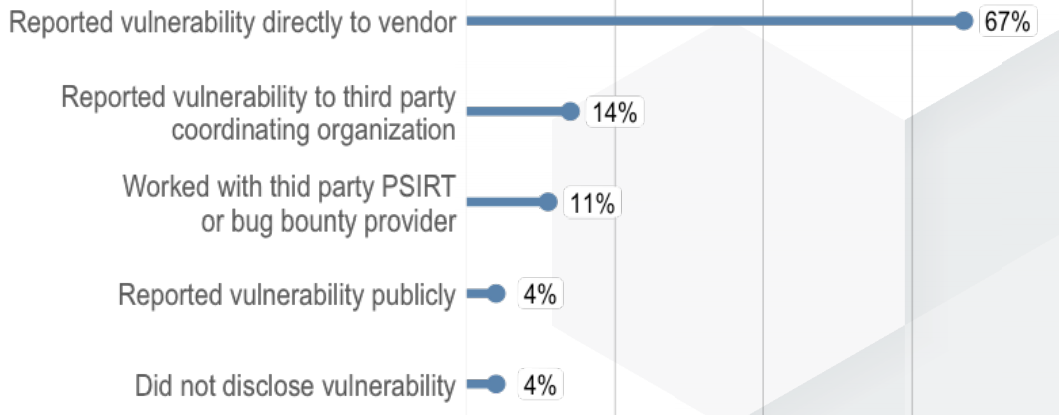
How researchers report vulnerabilities (Source NTIA)
The survey questioned a worldwide sample of 414 researchers and 285 vendors. Just over half of the researcher respondents (210) were from the U.S., with the remainder hailing from 50 other countries. The largest group of researchers, just over half, worked independently (50.6 percent), while the next-largest group worked for a for-profit organization (42 percent). In addition, 17.2 percent of respondents described themselves as “accidental finders,” and 8.6 percent reported researching on behalf of a not-for-proft organization.
Of the 285 vendors, a large majority (180) were from the U.S., with the remainder from 29 other countries, including, in order of significance: Canada, Germany, Japan, the United Kingdom, France and Australia. One-hundred sixty of the vendor respondents were from companies with fewer than 1,000 employees, and 125 were from large companies (with 1,000 or more employees).
The second working group addressed one of the more complex challenges researchers face: How do you practice responsible disclosure when a vulnerability affects multiple parties — much as Heartbleed did — on such a huge scale?
This working group brought together NTIA stakeholders and members of the Forum of Incident Response and Security Teams, or FIRST, an international group that helps expert IT teams better respond to security incidents. Guidelines and Practices for Multi-party Vulnerability Coordination describes different scenarios and the patterns of communication that correspond to them — from simple cases to more complex ones involving supply chains or shared open-source libraries, or instances where vulnerabilities are made public before some stakeholders are ready.
The third working group focused on vulnerability disclosures in safety critical industries where the potential for harm goes beyond data breaches to directly impact human safety. According to a blog post from NTIA Deputy Assistant Secretary for Communications and Information Angela Simpson, the group felt that these industries, unlike traditional software or IT vendors, will be relatively unfamiliar with security vulnerability disclosure best practices — and so produced a disclosure 101-type document, Coordinated Vulnerability Disclosure “Early Stage” Template. This document “reviews key issues for companies to consider when designing a vulnerability-disclosure policy,” wrote Simpson, “including how to scope a policy, and how such policies might evolve over time.”





