Hacking group targets organizations focused on North Korea’s missile program

Hackers using web infrastructure associated with a known North Korean threat group are behind a dormant phishing campaign that’s targeted the ministry of foreign affairs in at least three countries, as well as a number of research organizations, according to findings shared exclusively with CyberScoop before their publication Wednesday.
Researchers from Anomali, a threat intelligence company based in California, found a network of malicious websites that appear to be login portals for the French Ministry for Europe and Foreign Affairs, the Ministry of Foreign and European Affairs of the Slovak Republic, Stanford University, and a U.K. think tank, among other targets. Each of the targets has focused in some way on North Korea’s nuclear efforts, or the international sanctions issued as punishment for it.
By tricking diplomats or other victims into entering their credentials into a malicious website, the hackers behind this apparent espionage effort could then use that information to spy on the affected inbox. Exactly who is behind the operation was not immediately clear, though Anomali determined the attackers in this case used the same command-and-control server and the same IP address as the Kimsuky campaign, which Palo Alto Networks and others previously have associated with North Korea.
“The domain is openly reported on as being a domain used by North Korea,” said Sara Moore, a principal research analyst at Anomali. “This is very brazen. It’s almost like they tried to hide it, but only a little bit.”
Most of the domains outlined in this research were offline at press time, though Moore suggested that, because many were registered this year, they could be intended for use in future attacks.
There is no indication any organizations named in this research were breached, only that attackers set up phishing pages meant to look like each potential victim’s site. Prior to announcing these findings, Anomali “went through all recognized and correct disclosure and notification procedures,” the company said. Anomali also has submitted the phishing sites to Google Safebrowsing and Microsoft for blacklist consideration.
CyberScoop independently verified Anomali’s findings with two external researchers, who expressed caution about any definite attribution to the Democratic People’s Republic of North Korea.
However, some of this activity overlaps with “Kimsuky,” or Thallium, a hacking group that appears to be aligned with the North Korean military that for years has launched attacks against Western diplomatic and national security entities concerned with Pyongyang’s ambitions, according to a source who spoke on the condition of anonymity.
Palo Alto’s Unit 42 research team in February disclosed the BabyShark malware campaign, explaining how attackers used phishing emails that appeared to be from a nuclear security expert who works for the United States government. Unit 42 determined that hackers had targeted a U.S. university scheduled to discuss North Korea denuclearization at an upcoming conference, as well as a national security think tank based in the U.S. Researchers first observed BabyShark malware in November 2018, Palo Alto said, adding that all malicious documents “were related to Northeast Asia’s regional security issues.”
The security firm AlientVault tied BabyShark to the Kimsuky campaign.
Anomali researchers on Aug. 9 detected a login page masquerading as the French Ministry for Europe and Foreign Affairs portal. A closer inspection of that site revealed a suspicious subdomain which aimed to ensnare credentials from officials who worked at agencies including the Agency for French Education Abroad, the Agricultural Research Centre for International Development and Business France, a government entity dedicated to international investment, among others.
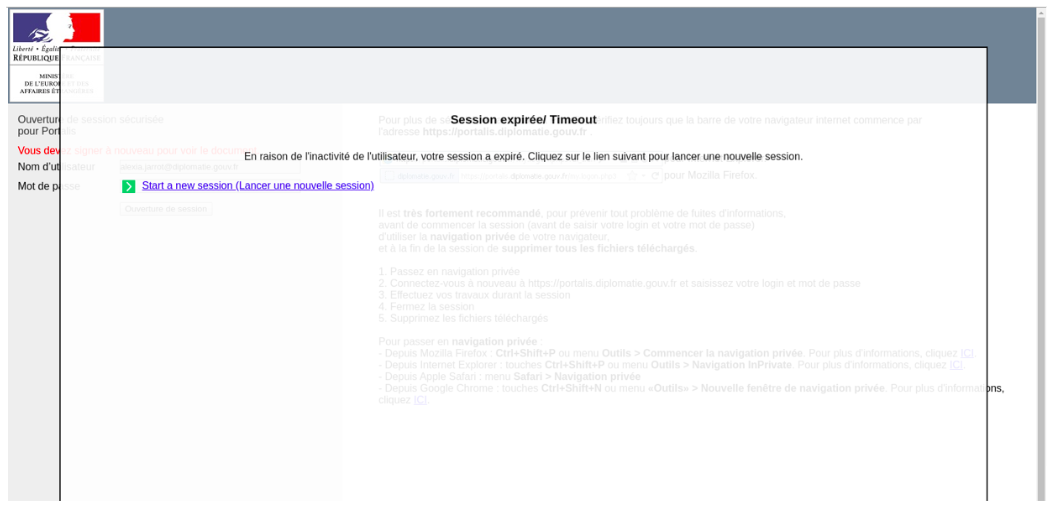
A phishing site meant to look like a legitimate login portal for France’s Ministry of Europe and Foreign Affairs (Anomali).
An Anomali analysis of the source code undergirding the phishing page detected a French email address belonging to a senior official assigned to the French Mission Team to the U.N. that researchers deemed likely to be the intended victim of the attack. The diplomat, whose name was withheld, works on a U.N. sanctions committee dedicated to disarmament and non-proliferation, specifically on Iran and North Korea.
Those domains all are hosted on the same IP address. When Anomali researchers further explored that IP address, they found a network of dozens of other malicious pages that misrepresented themselves as various sources.
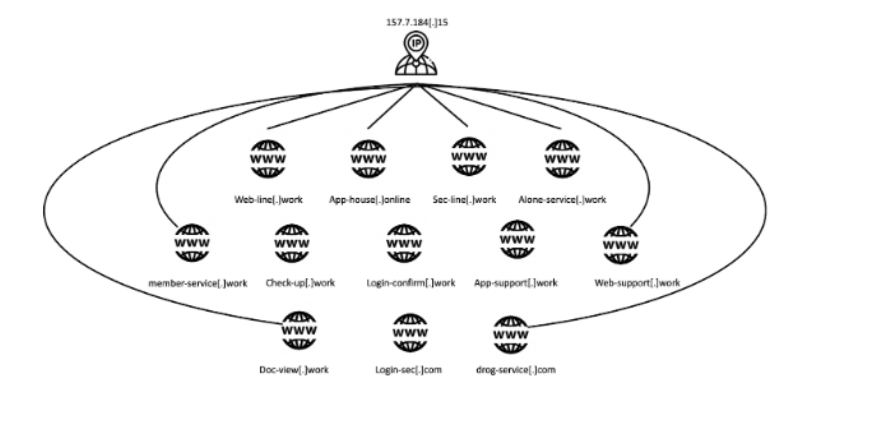
An Anomali rendering of the web infrastructure that made it possible for one IP address to host so many phishing sites.
Perhaps the most notable page appeared to be a Stanford University secure email service which encouraged faculty and students to use that portal to send “moderate or high risk data,” according to Anomali. Stanford is also home to the Center for Security and Cooperation and the Asia Pacific Research Center, which examine North Korea-related issues. School representatives did not return multiple requests for comment.
North Korea’s press agency earlier this month criticized France and other members of the U.N. Security Council for discussing Pyongyang’s recent missile tests in a closed-door meeting.
Other targets included the Chinese technology company Sina, the foreign ministry of the South African government, the U.K.’s Royal United Services Institute think tank and the Congressional Research Service, according to Anomali.
One phishing domain included in Anomali’s findings was a malicious variant that posed as a link from Gizmodo. The phishing page was offline, though, when asked whether hackers may have impersonated the media site, Moore said, “It’s hard to know the implication without a visual site.”





