Microsoft seizes hundreds of phishing sites tied to massive credential theft operation
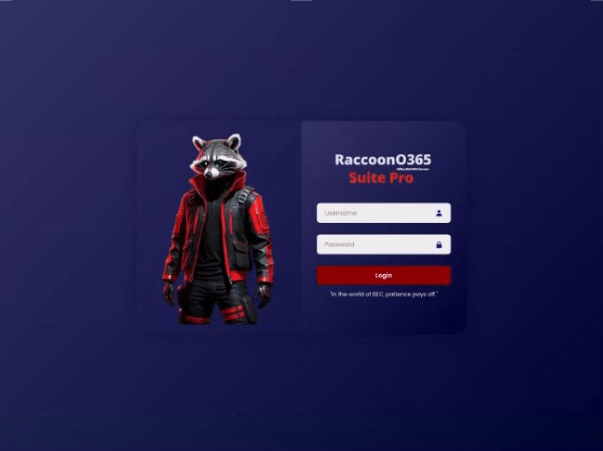
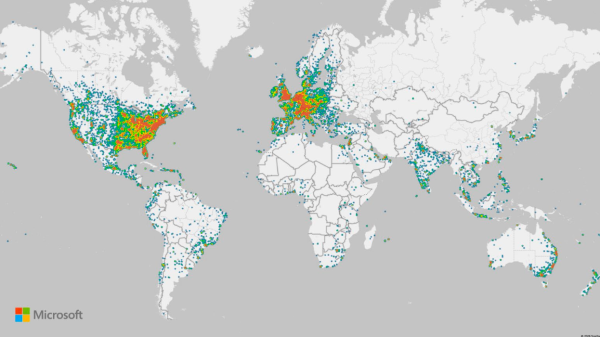
Microsoft’s Digital Crimes Unit coordinated the seizure of 338 domains used by RaccoonO365, a financially motivated threat group that developed and sold phishing kits that have been used to steal more than 5,000 Microsoft credentials since July 2024, the company said Tuesday.
The threat group, which Microsoft tracks as Storm-2246, enabled cybercriminals to steal credentials from organizations spanning 94 countries, making it the “fastest-growing tool used by cybercriminals to steal Microsoft 365 usernames and passwords,” Steven Masada, assistant general counsel at Microsoft’s DCU said in a blog post.
RaccoonO365 services were used indiscriminately to target more than 2,300 U.S. organizations in a tax-themed phishing campaign earlier this year. Its kits, which use Microsoft branding for fraudulent emails, attachments and websites, have also been used against at least 20 U.S. health care organizations, according to Microsoft.
“The rapid development, marketing, and accessibility of services like RaccoonO365 indicate that we are entering a troubling new phase of cybercrime where scams and threats are likely to multiply exponentially,” Masada said.
Microsoft, acting on a court order granted by the U.S. District Court for the Southern District of New York, worked with Cloudflare to seize and take down RaccoonO365’s infrastructure. The company also worked with Chainalysis to trace the threat group’s cryptocurrency transactions, allowing it to attribute malicious online activity to real identities.
Microsoft accuses Joshua Ogundipe of Nigeria of running the criminal enterprise, which sold phishing kits to a community base of more than 850 members on Telegram. Ogundipe and his associates have received at least $100,000 in cryptocurrency payments, reflecting an estimate of up to 200 subscriptions.
“During the investigation, the DCU engaged directly with the threat actor without disclosing our identity to acquire the phishing kits,” Maurice Mason, principal cybercrime investigator at Microsoft’s DCU, said in a Q&A with Chainalysis.
In a separate purchase, the alleged cybercriminal inadvertently shared a cryptocurrency wallet address for payment that allowed investigators to trace the funds to a wallet hosted on a Nigeria-based cryptocurrency exchange previously linked to Ogundipe, Mason added.
Microsoft said Ogundipe has a background in computer programming and accused him of writing the majority
of the code for the subscription-based phishing service, which allows cybercriminals to send up to 9,000 phishing emails per day. Investigators said RaccoonO365 may have facilitated the transmission of hundreds of millions of malicious emails.
Microsoft, which sent a criminal referral for Ogundipe to international law enforcement, also addressed continued discontent with persisting legal challenges.
“Today’s patchwork of international laws remains a major obstacle and cybercriminals exploit these gaps,” Masada said. “Governments must work together to align their cybercrime laws, speed up cross-border prosecutions and close the loopholes that let criminals operate with impunity.”
RaccoonO365’s kits sent emails to victims with malicious attachments, links or QR codes that redirected users to a fake Microsoft O365 login page to harvest credentials, Cloudflare researchers said in a blog post. When victims entered credentials, the kit allowed attackers to capture the password and resulting session cookie, bypassing multifactor authentication.
The codebase included functions for anti-analysis and evasion, user-agent filtering, security vendor evasion, network-level blocking and dynamic traffic routing, according to Cloudflare.
The phishing emails were often a precursor to malware and ransomware, yet not every stolen credential led to compromised networks or fraud, according to Microsoft. The company said it always expects cybercriminals to try to rebuild operations after a takedown and pledged to take additional steps to dismantle any new or reemerging infrastructure.