Iranian hacking group expands focus to US politicians, critical infrastructure, researchers find
An Iranian hacking group previously thought to mainly focus on compromising academics, journalists and human rights workers now appears to have included U.S. politicians, critical infrastructure and medical researchers to its target list, according to the cybersecurity firm Proofpoint.
The group known as TA453 has quietly added “outlier” attacks to its portfolio over the past two years, seemingly working more closely with Iranian state actors to carry out their bidding, researchers said in a report issued Wednesday.
“We believe that this activity reflects the group’s flexible mandate and possible ad hoc support to hostile operations by Iranian state actors, including the Islamic Revolutionary Guard Corps,” said Sherrod DeGrippo, VP of threat research and detection at Proofpoint.
The group has been quite busy over the past couple of years, she noted. “In 2022 alone, our researchers have observed this group using a social engineering technique we’ve dubbed Multi-Persona Impersonation, and now we’re sharing our observations on anomalous campaigns in which TA453 has deviated from its standard phishing techniques and target victimology.”
The researchers’ additional findings indicate that TA453, which is also known as Charming Kitten, Phosphorous and APT42, may be more worrisome than previously thought, and becoming an important tool for the Iranian government to carry out digital espionage campaigns in support of other operations.
“Adjusting its approaches likely in response to ever changing and expanding priorities, the Proofpoint-observed outlier campaigns are likely to continue and reflect IRGC intelligence collection requirements, including possible support for hostile, and even kinetic, operations,” researchers said.
The “outlier” attacks that Proofpoint has attributed to TA453 include campaigns to target medical researchers, travel agencies, an aerospace engineer, and a realtor involved in the sale of multiple homes near the headquarters of U.S. Central Command in Tampa, Fla.
Proofpoint also tied malware exclusively used by TA453 to target an unnamed “close affiliate” of former National Security Adviser John Bolton, who was the subject of an Islamic Revolutionary Guard Corps death plot beginning in October 2021, according to the U.S. Department of Justice.
The group is also focused on Iranian targets such as the country’s fledgling space program, travel agencies, as well as scholars studying women’s and gender studies in North American universities.
The techniques and tactics used in the outlier campaigns also caught the researchers’ eyes. In one 2021 case, after a U.S. government official commented on the Joint Comprehensive Plan of Action nuclear negotiations, the group targeted the official’s press secretary using a compromised email account belonging to an unnamed local reporter.
Another noteworthy tactic involved the group using the name “Samantha Wolf,” a persona the group uses in social engineering campaigns. The Wolf persona has been used at least three times in 2022, the researchers said, starting in February or March with benign conversation emails sent to an unnamed Middle Eastern energy company.
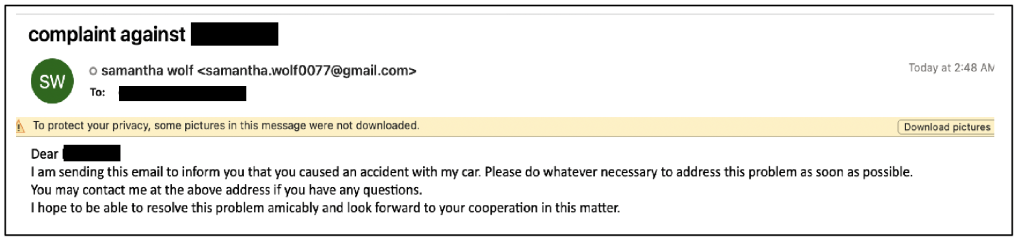
In late April, “Samantha pivoted to target a US-based academic Proofpoint previously observed targeted by multiple Iranian intrusion sets, including traditional approaches by TA453,” the researchers said. “This lure broke the typical TA453 mold and used confrontational tactics to increase the urgency behind the lure.”
By late 2022, the researchers observed multiple other “complaint-themed benign conversation emails” sent to senior U.S. and European government officials. “Samantha’s confrontational lures demonstrate an interesting attempt to generate engagement with targets not seen from other TA453 accounts,” the researchers found.





