Deep dive into hack against Iranian state TV yields wiper malware, other custom tools
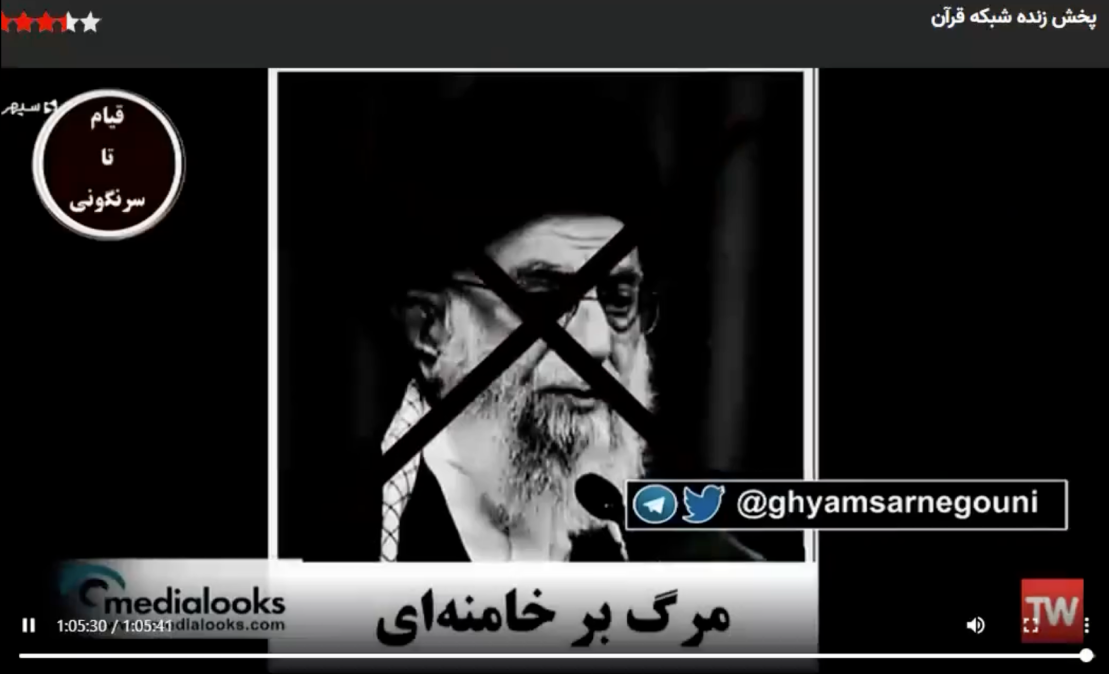
The Jan. 27 hack of Iranian state broadcaster IRIB — which ran a message of support for opposition leaders and called for the assassination of Iran’s supreme leader — came with previously unidentified wiper malware, according to research that suggests the incident was more destructive than initially assumed.
Researchers with Check Point, a Tel Aviv-based cybersecurity company, published the findings Friday based on what it said were files and other forensic evidence connected to the hack. Iranian officials acknowledged the attack at the time, saying that “disruptions” also occurred on another television channel and two radio stations, and called the hack “complex.” The breach occurred the day before Iran began its multi-day celebration of the 1979 revolution.
“We could not find any evidence that these tools were used previously, or attribute them to a specific threat actor,” the researchers wrote.
The files found and analyzed by Check Point include the wiper; the software used to play the video; malware that takes screenshots of target screens; evidence of custom-made backdoors; and files for installing and configuring malicious executables. Check Point didn’t speculate on what else those tools might have been used for, or how the hackers gained initial access to the networks.
The Jan. 27 hack was just one in a series of incidents that seemed designed to embarrass the Iranian government. The intrusions date at least to July 2021 — when the national railway services were disrupted — and continued until at least Feb. 7 of this year. The consequences have included the release of camera footage from a prison in Tehran, as well as disruptions to the electronic payment system used by the general public to pay for government-subsidized gasoline.
Some experts saw the attacks as part of an ongoing cyber tit-for-tat between the governments of Iran and Israel, even as a group calling itself “Predatory Sparrow” claimed responsibility without claiming any nation-state sponsor. Iranian officials blamed the MEK — a long-running Iranian opposition group — but the group denied involvement, and said they found out about it when it happened.
A few days after the Jan. 27 television disruption, the state broadcaster was hacked again — during the middle of a live broadcast of an Iran-UAE international soccer match — with a message urging citizens to rise up against the government. In that case a group called Edalat-e Ali claimed responsibility.
Check Point researchers note that Predatory Sparrow — which had also claimed, without proof, responsibility for the railway services hack, another on the transportation ministry, and the incident against Iranian gas stations — posted a message to its Telegram channel telling followers to “Wait for the good news from our team.” Later that day, it posted a video played on one of the hacked TV channels.
The researchers note that there remains no technical proof of the group’s involvement, and that the video it put into its Telegram channel was posted by another Telegram account.
In its analysis, Check Point to compared the Jan. 27 wiper with previously identified malware from a group calling itself Indra — another self-styled hacktivist group that was known to be actively targeting entities in the region, specifically Syria, dating back to 2019. The two wipers are coded and behave differently, Check Point said, but some similarities suggest that the Jan. 27 tooling was perhaps inspired by Indra.
In both cases, the researchers wrote, the attackers had capabilities that may not be fully known, and managed to pull off complicated operations.
“On the other hand, the attackers’ tools are of relatively low quality and sophistication, and are laundered by clumsy and sometimes buggy 3-line batch scripts,” they wrote. This suggests the attackers “might have had help from inside IRIB, or indicate a yet unknown collaboration between different groups with different skills.”






