Government’s software vulnerability repository is slow to add new cyberthreats, report says

There is a median lag time of approximately seven days between when someone discovers an exploitable software vulnerability and its eventual release on the National Vulnerability Database, or NVD, according to research conducted by U.S. cybersecurity and dark web intelligence firm Recorded Future.
The NVD, a public repository managed by the National Institute of Standards and Technology that contains data on known vulnerabilities, is one of the preeminent disclosure platforms for information about software flaws that can be exploited by hackers. Private companies and the government share access to it. Recorded Future cautioned companies and agencies against relying on it as the fastest way to learn about new risks to their network infrastructure, products, digital services and other business processes.
“While it’s tempting to think of the National Vulnerability Database as the central source for vulnerability information, the reality is that there is a vast amount of content about vulnerabilities already published prior to the NVD’s release of a vulnerability. The adversary community is monitoring and contributing to this space,” Recorded Future Chief Data Scientist Bill Ladd told CyberScoop.
For those adversaries, seven days can be plenty of time to wreak havoc by exploiting a vulnerability, even if a software patch is quickly issued.
Recorded Future’s findings underscore some of the challenges faced by the government’s current vulnerability information sharing model, which in the case of the NVD requires manual participation from interested parties.
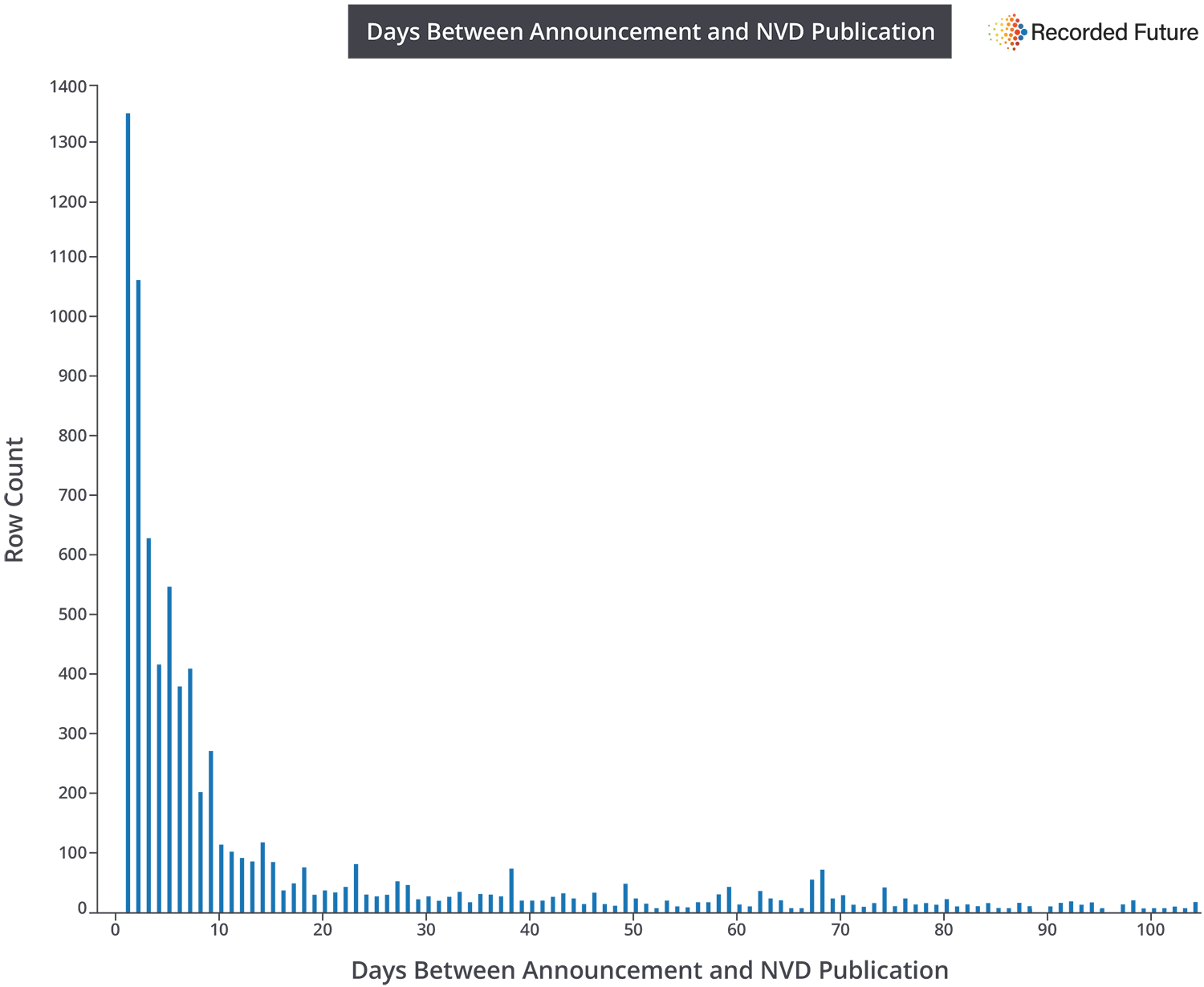
Image via RF
“This lack of speed — announcement to the NVD — is hurting companies,” Ladd said. “They need situational awareness across this entire space, as well as what is published on the NVD, to protect themselves. While there is a significant amount of information sharing occurring today, there is insufficient coordination of that content.”
The report notes that 75 percent of vulnerabilities recorded between 2016 and 2017 were disclosed elsewhere before being shared on the NVD.
While the existing gap between discovery and disclosure to NVD averages about seven days today, it is quickly increasing and can vary significantly, according to Recorded Future. Major vendors involved in the software vulnerability disclosure process include major technology brands like Google, Apple, Microsoft and Oracle, according to Recorded Future.
“Longer gaps are quite common with 25 percent of [software vulnerabilities] having at least 50-day gaps and 10 percent having gaps of over 170 days,” the report reads. “There are still over 500 CVEs that were first announced in 2016 that are still awaiting NVD release.”
Occasionally, some of these vulnerabilities are first discussed in hidden forums located in the dark recesses of the internet — where information about how to compromise specific systems is sometimes shared. About 5 percent of recorded vulnerabilities between 2016 and 2017 were detailed in the deep and dark web prior to NVD release, Recorded Future found.
“We often see reposts of researcher reports directly into deep and dark web sources. They may even be translated, for example, into Russian on Russian criminal forums. [Proof of Concept] code is discussed, posted, sold,” Ladd wrote.
A variety of different factors affects when and how quickly a vulnerability goes from being discovered to disclosed to patched. The severity of a vulnerability — meaning to what degree it can be exploited and how many individuals may be negatively impacted by that exploitation — typically dictates the pace at which information is shared and acted upon.






